Black Basta ransomware – what you need to know

What is Black Basta?
Black Basta is a relatively new family of ransomware, first discovered in April 2022.
Although only active for the past couple of months, the Black Basta ransomware is thought to have already hit almost 50 organisations – first exfiltrating data from targeted companies, and then encrypting files on the firm’s computer systems.
Victims have reportedly been hit in countries around the world including the United States, UK, India, Canada, Australia, New Zealand, and UAE.
50 companies in a couple of months? That sounds like a lot. And then the gang demands money?
Correct. Targeted organisations are presented with a ransom demand after the ransomware has installed itself, encrypted files, and deleted shadow copies and other backups.
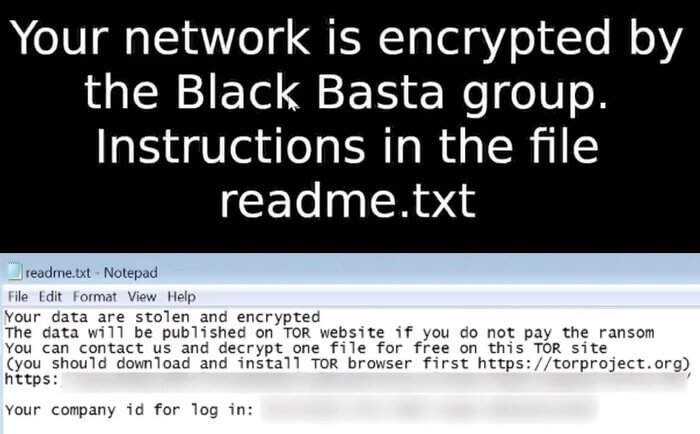
If victims want the key to unlock their data, or prevent the Black Basta gang from leaking the data, they need to pay their extortionists a large amount of cryptocurrency.
Who is being hit by the Black Basta ransomware?
The ransomware attacks do not appear to be targeting a specific vertical or industry, with reports of infections at a range of victims including manufacturing, utilities, transport, and government agencies.

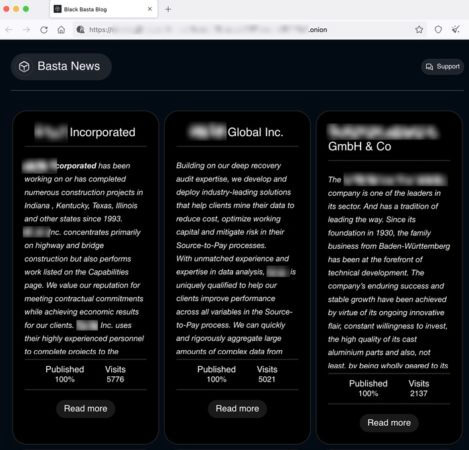
These victims will have found that having secure backups is not a complete solution. Backups may help you get your company back up and running again, but it doesn’t stop Black Basta from publishing data it has stolen from your servers on its site on the dark web.


So what makes Black Basta noteworthy?
Aside from the rapidly-growing list of victims and a surfeit of new variants, there are some other things that make the Black Basta ransomware interesting.
Recently, VMWare ESXi variants of Black Basta have been discovered that target virtual machines running on Linux servers, alongside the versions which infect Windows systems.
In addition, many of the attacks have made use of Qakbot (also known as QBot) to help it spread laterally through an organisation, perform reconnaissance, steal data, and execute payloads.
Furthermore, a group policy object is created on compromised domain controllers to disable Windows Defender and anti-virus solutions.
Do we know where the Black Basta ransomware might originate from?
It’s difficult to be certain, although some Russian language posts have been left by people claiming to have links to Black Basta on underground internet forums.
The cybersecurity community is split regarding whether the Black Basta group is associated with other well known ransomware gangs or not. What does seem reasonable to believe is that they were, at the very least, inspired by the success of other ransomware-as-a-service operations.
So how can my company protect itself from Black Basta
The best advice is to follow the same recommendations we have given on how to protect your organisation from other ransomware. Those include:
- making secure offsite backups.
- running up-to-date security solutions and ensuring that your computers are protected with the latest security patches against vulnerabilities.
- using hard-to-crack unique passwords to protect sensitive data and accounts, as well as enabling multi-factor authentication.
- encrypting sensitive data wherever possible.
- reducing the attack surface by disabling functionality that your company does not need.
- educating and informing staff about the risks and methods used by cybercriminals to launch attacks and steal data.
The post ” Black Basta ransomware – what you need to know” appeared first on TripWire
Source:TripWire – Graham Cluley
