World Password Day is Dead. Long Live World Password Day!

In 2002 I sat in a local bookstore in Jackson Hole, WY that offered a few Internet-connected computers for hourly use. After chatting with the owner and petting the resident store dog, I took a few guesses at the password protecting these computers. It took me maybe 10 attempts. It was, of course, some variation of the dog’s name. While this is a very dated story, it’s this kind of story that still drives many people’s perception of why a strong password is necessary. We imagine some nefarious (well, not in my case) criminal sitting at a keyboard, guessing passwords based on pet names or children’s birthdays. That mental model is, of course, largely false. The risk of an individual human actor guessing your password by repeatedly typing it into a prompt is nearly zero.

So how do we modernize our understanding of the threat landscape when it comes to passwords? Well, the first step is to stop talking about passwords. As long as we continue to conceptualize the threat as being related to passwords, we’ll continue to miss the mark. Passwords are part of the overall authentication picture, but we stand to gain more in terms of securing our critical data, whether personal or professional, from expanding our understanding of authentication and the associated threats.
Credentials, Factors, and Trust
I’m a big proponent of adopting language to drive change. We should stop talking about passwords exclusively. Passwords are really a single component of the larger set of “credentials” that can be used for authentication. When we talk about credentials instead of passwords, we pull additional authentication factors into the conversation, such as biometrics, keys, SMS messages, and other authentication tokens. It’s true that passwords, especially ‘weak’ passwords, are the weakest link in the authentication chain. We’ve spent years advocating for stronger passwords as a means to address the problem. We’ve gone so far as to create an entire industry around managing passwords because we’ve pushed users into creating multiple, unique passwords that are so complex we can’t remember them. The problem is that in this sort of arms race between people creating complex passwords and attackers building tools to crack them, there’s no winning. This problem can’t be solved at the same logical level at which it’s created.
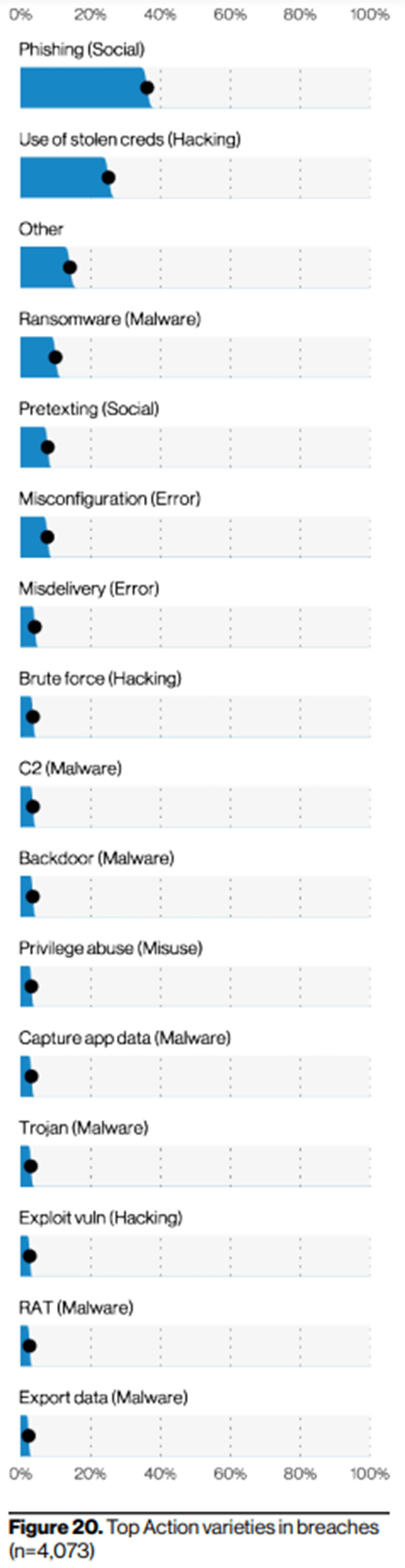
At the same time, credential compromise remains a significant part of the threat landscape. The Verizon Data Breach Investigations report for 2021 puts “use of stolen creds” as the second action variety in breaches, just below phishing (which is an often-used method to steal credentials). For attackers, it’s easier and less likely to be detected if they’re accessing systems with valid credentials.

The solution is to move beyond passwords alone for authentication. In today’s world that means implementing multi-factor authentication (MFA). When you incorporate multiple factors into the authentication process, you change the game for the attackers, and you improve the playing field for the defenders. It’s no longer sufficient to compromise a username and password in order to gain access. If you’re a skeptic (and most information security folks are), you’ll point out that attackers have already adapted to MFA and that there are successful attacks against MFA today. And you’re absolutely right, but they are more complex, more costly, and less successful than simply stealing a database full of password hashes and cracking them. What’s more, the successful introduction of MFA as a technology provides a new architecture on which defenders can continue to innovate. It gets us, as an industry, off of the endless train of creating stronger and stronger passwords. In fact, it paves the way for passwordless authentication, where we no longer need passwords to establish trust. And that’s what the entire process is about, establishing sufficient trust to grant access.
Long Live World Password Day!
Maybe all of this means that it’s time for World Password Day to move from currency to history, and to act as a reminder that we shouldn’t rely on passwords alone, or maybe at all. For this World Password Day, go make a list of the top 10 services you regularly authenticate to. Then go turn on MFA for each of them. It’s probably the single best thing you can do to protect your own identity and data.
The post ” World Password Day is Dead. Long Live World Password Day!” appeared first on TripWire
Source:TripWire – Tim Erlin
