Wall Street targeted by new Capital Call investment email scammers

Business Email Compromise (BEC) scammers, who have made rich returns in recent years tricking organisations into transferring funds into their accounts, have found a new tactic which attempts to swindle Wall Street firms out of significantly larger amounts of money.
According to a newly published-report by Agari, scammers are seeking to defraud Wall Street businesses and their customers out of US $809,000 on average per incident.
This emerging form of BEC attack is a “capital call” scam, where the fraudsters pose as an investment or insurance firm seeking a portion of money previously promised by an investor for a particular investment vehicle.
Such funds are, inevitably, significantly larger (Agari says on average they are seven times higher) than those sought in most wire transfer scams.
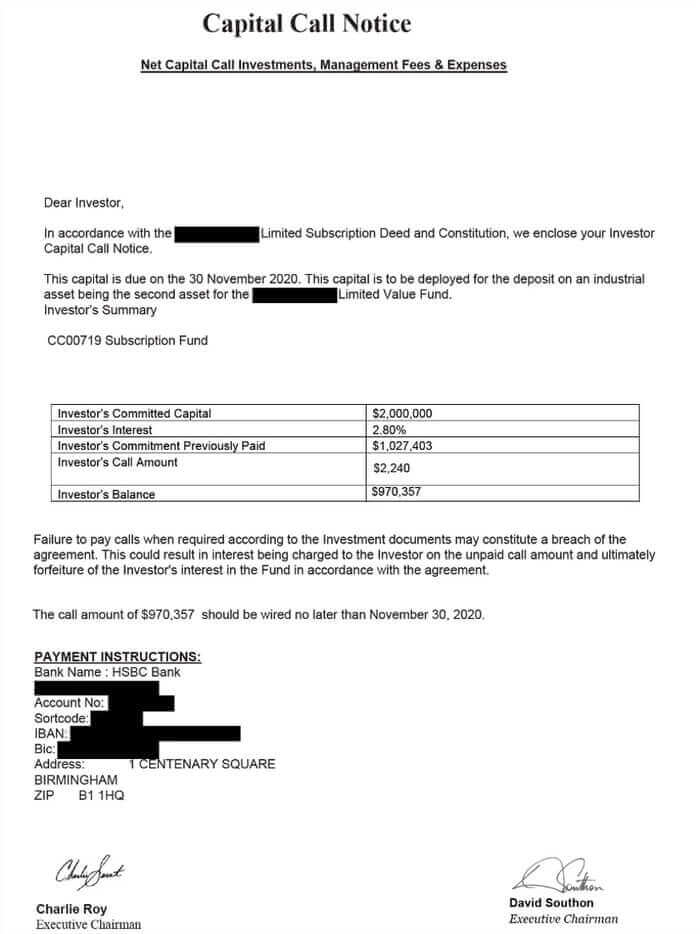
In an example shared by the researchers, the scam email attached a Capital Call Notice for US $970,357.00 to be deposited into a bank account under the fraudsters’ control.

If the targeted investor was duped into wiring the funds, then it is likely that money would be quickly moved into other accounts and withdrawn by mules to prevent the payment from being returned to the victim.
Threat researcher Crane Hassold told Bleeping Computer that the examples seen to date do not indicate that the attackers are using any inside knowledge when requesting capital call payments, but are instead referencing fictitious investments.
That suggests to me that the attackers are much less likely to succeed in their fraudulent requests than if they had hacked into investment firms and were specifically able to target investors who were expecting to receive a capital call notice at some point.
Furthermore, the attacks seen by Agari have mostly come through the Czech webmail provider Centrum, rather than making more of an effort to disguise themselves as a communication from an investment firm.
However, it is still possible for someone to be duped and potentially lose a large amount of money. And it would be a brave person indeed who betted against attackers in the future posing more successfully as an investment firm when sending out capital call scam emails, and using inside knowledge to make the social engineering much more likely to succeed.
Once again, there is a clear call for businesses to put in place both strong email security solutions and clear, strong processes to reduce the chances that funds are ever wired to fraudsters.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” Wall Street targeted by new Capital Call investment email scammers” appeared first on TripWire
Source:TripWire – Graham Cluley
