Upgrade From Whitelist Profiler to Tripwire State Analyzer

If you’re a Tripwire® Whitelist Profiler customer, then you know that the software does an excellent job of executing its core functionalities. These include comparing the running state of a machine to the approved and expected configurations in your environment to stay in compliance with audit and internal policies. Although Whitelist Profiler is proficient in this regard, that doesn’t mean it can’t be improved in other capacities such as ease of use. This was the sentiment expressed by real Whitelist Profiler customers when asked what they would want out of the software if they could have anything. Tripwire® State Analyzer is the manifestation of the push for heightened usability. The application has all the same core capabilities of Whitelist Profiler but with numerous new features aimed at creating even more accurate and efficient processes for your team.
Web-Based Interface to Configure Allow Lists
In Whitelist Profiler, the configuration of allowlists was performed manually on CSV files using a text editor. This process, while sufficient to accomplish the task, was very prone to human error. As the complexity of allowlist items increased, the corresponding difficulty of updating the configuration increased further. With Tripwire State Analyzer, we have implemented a modern user interface, allowing for simple updates to allowlists with validation checks on the inputs to prevent bad configurations from stopping the entire process. The user interface also displays a historical record of changes made to allowlists as well as an intuitive rollback feature to revert changes to a prior configuration version. From editing and viewing allowlists in the user interface to viewing assessment data, the time savings and ease of use improvements are tremendous.
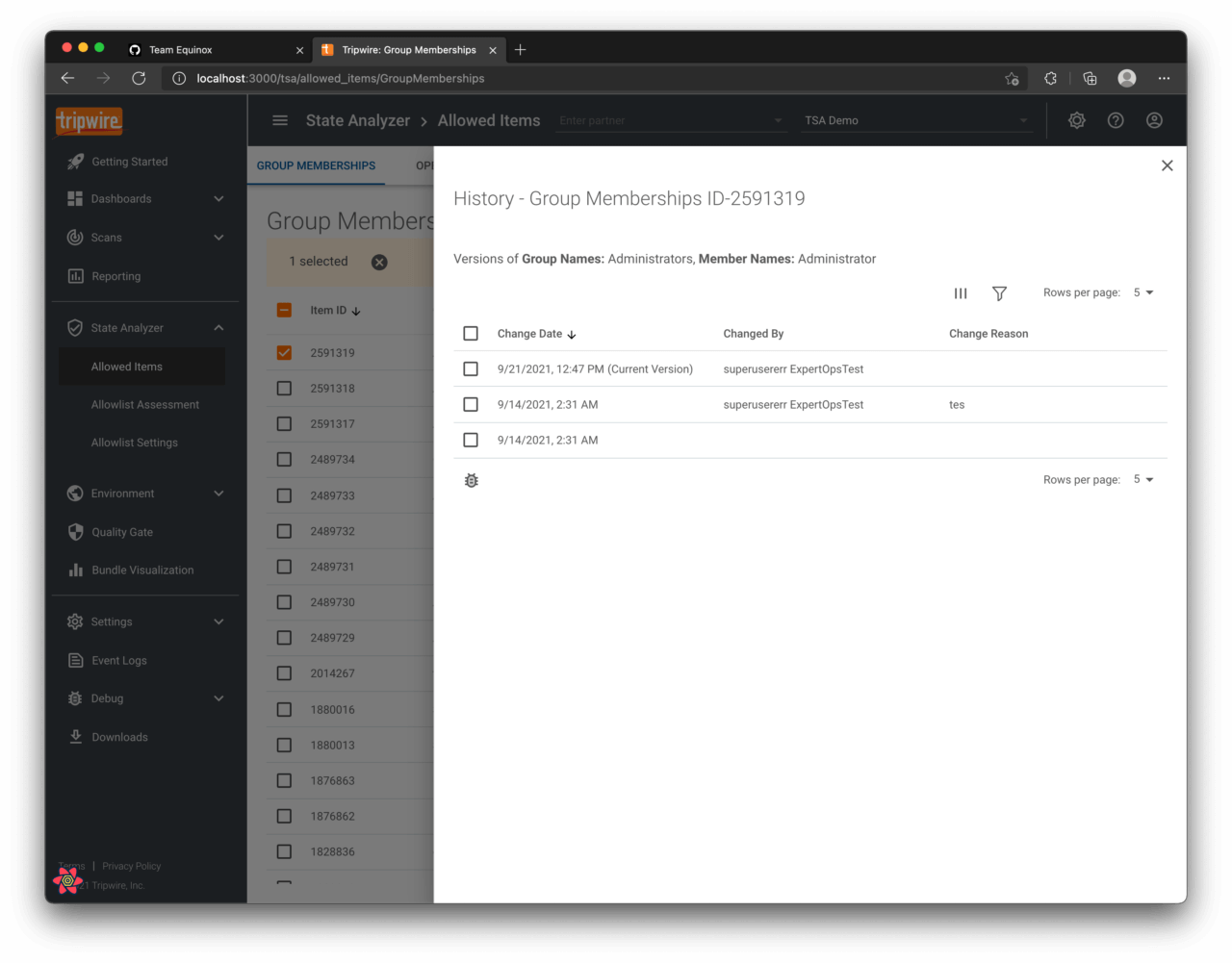
View History on the Configured Items
When looking at changes made to configurations in Whitelist Profiler, all that is visible is the time of the most recent change. There is always the possibility that the configuration could have been changed multiple times by multiple different people and for a variety of purposes. Recording and maintaining level of detail is extremely useful when audits are being conducted or analysis is being conducted on changes to the allowlist. That is precisely why Tripwire State Analyzer maintains a history of every single change made to your allowlists, all the way down to the who, what, when, where, and why.

Local Database of the Related Scan Data
One area where Tripwire State Analyzer (TSA) really builds on its ease of use is in its ability to minimize any disruptions it may cause your Tripwire ® Enterprise console. Instead of running scanning data back and forth from the Tripwire Enterprise API into Whitelist Profiler, the application utilizes two databases in order to improve processing speed and reduce stress on the Tripwire Enterprise console. The first database stores relevant data funneled in from Tripwire Enterprise, while the second database serves as a backup for when the first is overloaded. This process results in a significant increase in processing efficiency and heightened data integrity while simultaneously asking for less data from Tripwire Enterprise as the TSA process runs.
Different Levels of User Access
From an administrative perspective, Tripwire State Analyzer offers a much simpler system that results in much less human error. In instances you need your audit team to validate allowlists but don’t want them to be able to make any changes to them, they can be granted a login to the user interface that allows them to see what is configured as well as what is set up based on policies or compliance states and assessment information. However, they will not be able to make any edits to those items. This allows for much more granular use controls, and it could save your team a great deal of time by preventing unnecessary errors and reducing the burden of research for other operational needs.
Being an Appliance vs a Software
Your team will love the major improvements in usability that Tripwire State Analyzer has to offer. One factor playing into that improvement is the fact that Tripwire State Analyzer is an appliance as opposed to installed software. Software updates require a tremendous amount of oversight from your IT team into whether the update was installed correctly, configured correctly, etc. However, as an appliance, most of this oversight is removed, as it allows for updates through administrative commands. This takes the guess work out of the update process and creates historical records of the maintenance performed.
A Great Value For a Small Price Increase
We understand that Whitelist Profiler is more than sufficient for accomplishing its intended objectives. However, we believe that the improvements in usability built on top of the core functionalities of Whitelist Profiler give Tripwire State Analyzer a substantial amount of value in terms of enhanced auditing records and operational time saved for your teams. Considering these benefits against the slight increase in price, we believe Tripwire State Analyzer makes a valuable addition to your cybersecurity suite.
To learn more about Tripwire State Analyzer, download the datasheet here.
The post ” Upgrade From Whitelist Profiler to Tripwire State Analyzer” appeared first on TripWire
Source:TripWire – Josh Sensibaugh
