Top Phishing and Social Media Threats: Key Findings from the Quarterly Threat Trends & Intelligence Report

In today’s online landscape, it is crucial for organizations to stay on top of the threats that put their enterprises at risk. Agari and PhishLabs have put together their Quarterly Threat Trends & Intelligence Report detailing their analysis of phishing and social media attacks this quarter. The report presents statistics regarding the volume of attacks, the tactics used by cybercriminals, and the main targets of these attacks, documenting the changes since last quarter. Below are the key findings from the report.
Phishing Threat Trends
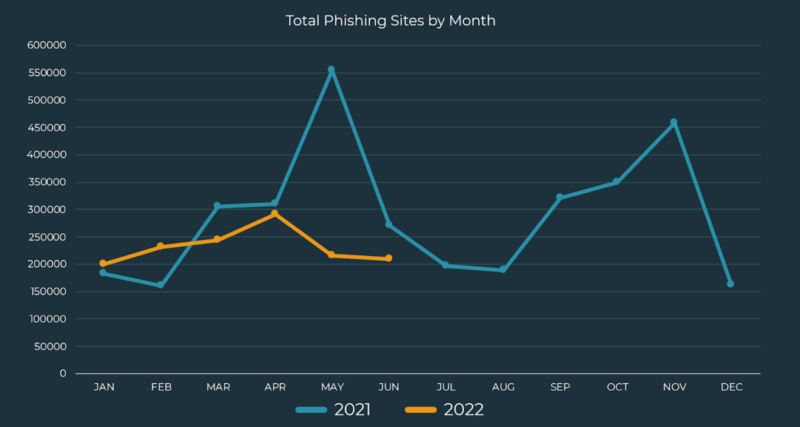
The volume of total phishing sites increased almost 6% from Q1 and remains steady, as opposed to the erratic spikes in activity that took place in 2021. For the remainder of 2022, phishing volume is expected to steadily climb as criminals learn where businesses’ weaknesses lie and take advantage of their vulnerabilities.
Although financial institutions remain the top targeted industry at 42% of attacks, these attacks have declined more than 19% since 2021. The second most targeted industry was telecommunications, experiencing 23% of all phishing attacks. Social media accounted for 21% of overall volume, notwithstanding a small decrease in attacks.
Phishing Targeting Corporate Users
Malicious emails increased in volume in Q2 in spite of a slight decrease in the total share of emails, making up 6.8% of the total. Emails classified as Do Not Engage increased in volume and share, accounting for 12% of employee-reported emails. These emails do not contain clear indicators of malicious intent, but are considered suspicious. Emails classified as No Threat Detected accounted for 81.3% of employee-reported emails, a slight decline in Q2.
Credential theft attacks decreased by 4.2% but still represented the largest proportion of email-based threats at nearly 55%. Response-based attacks that rely on social engineering tactics reached the highest volume and proportion since 2020, accounting for 41% of email-based scams. Malware delivery increased slightly and accounted for 4.5% of attack volume. Credential theft attacks targeting Office 365 accounts reached a six-quarter high in share and volume, accounting for more than 58% of all credential theft phishing links.
In Q2, 54.2% of response-based email threats were Advanced-Fee scams (also known as 419 scams), up 3.4% this year. BEC also increased, accounting for 16.3% of attacks. Hybrid vishing attacks reached a six-quarter high, an increase of 625% since Q1 2021, accounting for 24.6% of response-based threats. In spite of a slight decrease in share, vishing volume has increased overall.
Emotet reports increased 30.7% and made up 47.4% of malware payload volume, overtaking QBot at 42.8%. Bumblebee, first detected in March 2022, was the third most reported payload at 2.9% of all attacks. Emotet, disrupted and taken down by authorities in January 2021, has recovered and regained status as the most commonly preferred payload by cybercriminals. Emotet operators are believed to be testing new tactics to gauge their effectiveness since its reemergence in November 2021.
Free webmail abuse made up 73% of BEC attack volume, while maliciously registered or compromised accounts declined to 27%. The top provider abused by cybercriminals in BEC attacks was Google/GMAIL, making up 71.7% of total attack volume. Microsoft experienced the greatest increase in share, growing more than 6% to contribute to 8.3% of BEC incidents.
Social Media Threat Trends
Social media attacks increased 20.3% from Q1 (102% from Q2 2021), averaging nearly 95 attacks per enterprise per month. Impersonation scams declined in share by 6.1% but still accounted for the largest share of social media threats at 40.7%. Fraud and cyber threats both increased to fill the second and third place spots. Data leaks have declined for six quarters in a row and accounted for only 0.4% of social media threats in Q2, down from nearly 25% in Q1 2021.
Impersonation of a brand decreased 7% from Q1, accounting for 25% of social media attack volume, while executive impersonation increased to make up 15.3% of social media attack volume. Brand and executive presence on social media is a significant factor in business success, and cybercriminals continue to take advantage by falsely using the names and faces of businesses to their own ends.
The financial industry accounted for more than 68% of social media attacks in Q2; national/regional banks took the top spot at 30.5%. Computer software was the only non-financial institution to experience an increase in attack share, up 0.7% to account for 13.4% of overall abuse.
Dark Web Threat Trends
Credit and debit card fraud represent the largest share of all incidents on the dark web at 67.3%, up 13.6%. Sale of corporate credentials accounted for 13.1% of dark web incidents, making it the second most common dark web threat in spite of a significant decrease in share, closely followed by consumer credentials at 13%.
Financial institutions made up almost 79% of dark web attacks (40.1% national/regional banks, 30.3% credit unions, 6.8% financial services). Telecom and ISPs made up 8% of all dark web abuse, a 0.5% decrease in share. Staffing and recruiting, dating, and retail all experienced declines in share as well.
Cybercriminals use a variety of avenues to market and sell stolen data. In Q2, 45.1% of stolen data listings were observed being marketed on chat-based services, an increase of 24.1% in share. Carding marketplaces and forums declined in share and accounted for 22.1% and 18.7% of the total respectively, while credential marketplaces increased 1.1% in share to 13.3%.
Conclusion
Threat actors are taking advantage of new and uncommon methods to maximize attack effectiveness. Phishing remains the top online threat, with month-to-month volume trending slightly down despite a 6% increase from Q1. Response-based email scams continue to increase, reaching the highest recorded volume since 2020. Hybrid vishing attacks seen in Q2 are a prominent example of cybercriminals modifying tactics to circumvent security measures.
Bad actors targeted organizations more in the first half of 2022, increasing investments in new, non-traditional tactics in addition to commonly reliable methods. It is important for security teams to invest in monitoring and protections that keep up with threat trends as much as possible, partnering with technology providers when necessary to protect against abuse.


Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Analysis of previous reports
Q1 2022 Phishing Threat Trends and Intelligence Report
The post ” Top Phishing and Social Media Threats: Key Findings from the Quarterly Threat Trends & Intelligence Report” appeared first on TripWire
