Top 5 Scam Techniques: What You Need to Know

Scammers are increasingly resourceful when coming up with scam techniques. But they often rely on long-standing persuasion techniques for the scam to work. So, you may hear about a new scam that uses a novel narrative, but there is a good chance that the scam relies on proven scam techniques once the narrative is stripped away. These scam techniques often exploit our characteristics and heuristics, or things that make us human and fallible.
In this blog post, I will cover some of the most common scam techniques and explain how they work.
Evoking visceral influence
Visceral influences such as hunger, thirst, pain, fear, excitement, sexual desire, greed, etc. are our primal states. They can be extremely powerful when evoked, as people will orientate all their attention to addressing the needs of that state. For example, have you ever heard that you should not go shopping for food when you’re hungry? This is good advice; when we are under the visceral influence, our rational thinking is compromised.
Scammers love evoking visceral influence in phishing correspondence. Examples include free prizes (excitement and greed) or a compromised account (fear). The key is to entice the potential victim to act quickly and impulsively without reasoning. Being in a visceral state also helps people to forget rational advice that they might be inclined to follow otherwise.

What to watch for
How the email makes you feel? Is it stressing you out, or are you excited at the prospect being offered?
Urgency
Visceral influence is fleeting. It comes quickly and wanes quickly. This is why scammers frequently pair evoking visceral influence with urgency cues.
Urgency is typically evoked by mentioning deadlines such as ‘You have 24 hours to recover your account’ or ‘Hurry, as only the first 100 people can claim this offer.’ But it can also be more subliminal such as in the example below. Here, the scammer has orchestrated a situation that is likely going to put pressure on the potential victim to act quickly (i.e., renewing subscription unless it is turned off).

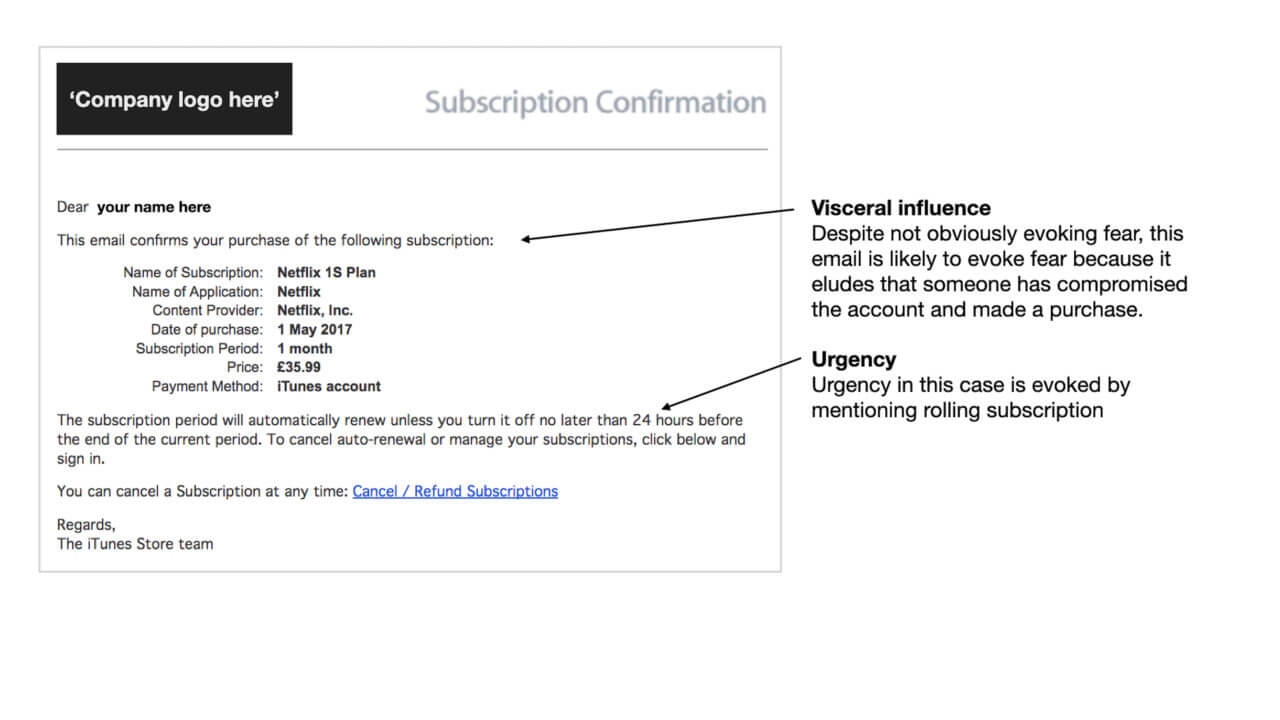
Urgency is often evoked in scams to persuade people to act quickly. That’s especially when under the visceral influence, which compromises careful thinking. It is often paired with other scam techniques such as scarcity.
What to watch for
Any indication of limited time in the correspondence that indicates you need to act quickly.
Scarcity
When something is hard to get, we want it more. We also tend to place greater value on it, as difficulty obtaining it will skew perception of quality. As such, we are more willing to do stupid things to get it, something which scammers know very well. Scarcity is evoked by limiting offers such as a ‘one-day offer.’ This encourages instant decisions so we can avoid missing out on a great opportunity. Scarcity is a known persuasion technique that’s often used in sales.
What to watch for
Indication that the offer is a one-time deal or somehow unique and that you will be missing out if you don’t act on it.
Authority
First is that, from an early age, we are brought up to respect and obey authority figures. Therefore, any requests coming from people in a position of authority will likely result in less resistance.
Second, we have also been brought up to trust people in certain professions because these people inspire trust and confidence. We typically trust that lawyers, doctors and even religious figures such as ministers have our best interests at heart. This means that we may not question their motives as we would the motives of other people. Some people are also more easily influenced by authority figures, which would make them even more vulnerable to authority cues.
What to watch for
Pressure to comply with requests from authority sources, especially if there is a threat that non-compliance would lead to arrest or penalties.
Social proof
Our world and our behaviors are shaped by looking at others, seeing what they do and evaluating how they behave. This can be exploited by scammers who may fake testimonials, recommendations and reviews online. Social proof lowers our risk perceptions. We become more open to trying things and products from which other people benefited. Purchasing items that come with good reviews or testimonials or purchasing from companies that have been recommended gives us confidence in that purchase.
Scammers exploit social influence in a couple of ways. These include faking testimonials and reviews or even going as far as creating fake social media accounts to do so. There’s also targeting individuals with phishing emails that pretending to come from people who have benefited from a particular product or service.
Another way of exploiting social proof is targeting groups of people who have something in common such as people who work or socialize together. In such situations, a scammer typically persuades one person in that group to go along with a purchase or an investment, as others in the group end up doing the same upon seeing a member of a trusted group recommending the investment. This is how pyramid schemes often work.
What to watch for
Testimonials and recommendations that are provided by the offer itself. These include any extremely positive reviews, especially if they are not detailed, as well as testimonials that appear in seemingly unrelated places such as social media pages.
Further Reading
Protecting a New Vulnerable Population on the Internet
Protecting the New Most Vulnerable Population – The Grandparent Scam
The post ” Top 5 Scam Techniques: What You Need to Know” appeared first on TripWire
Source:TripWire – Martina Dove
