The Twitter mega-hack. What you need to know
What the heck has happened on Twitter?
Twitter accounts, owned by politicians, celebrities, and large organisations suddenly started tweeting messages to their many millions of followers, at the behest of hackers.
What did the messages say?
Here is a typical one which appeared on the account of rapper, songwriter, and optimistic Presidential candidate Kanye West and was distributed to his almost 30 million followers.
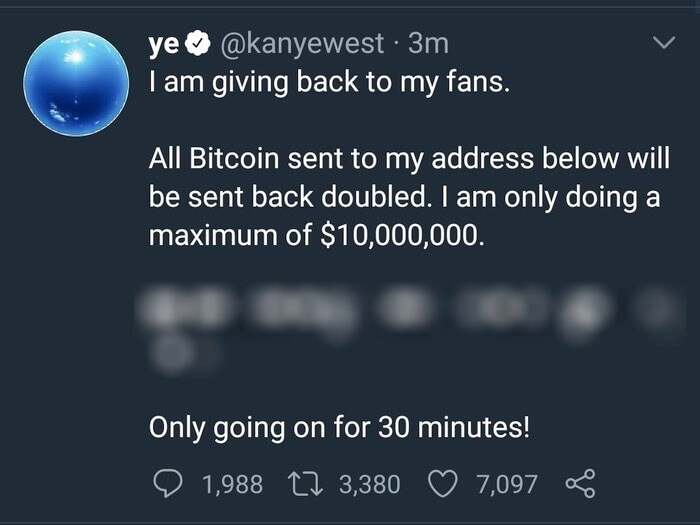
I am giving back to my fans.
All Bitcoin sent to my address below will be sent back doubled. I am doing a maximum of $10,000,000.
[redacted bitcoin address]
Only going on for 30 minutes.
To be honest I wouldn’t put it past Kanye West to post a tweet like that…
And he has in the past been a little sloppy when choosing his passwords, but on this occasion similar messages appeared on the accounts of Joe Biden, Barack Obama, Bill Gates, Jeff Bezos, Elon Musk, Kim Kardashian, Mike Bloomberg, Uber, Apple, Coinbase, Binance, and many other verified accounts.

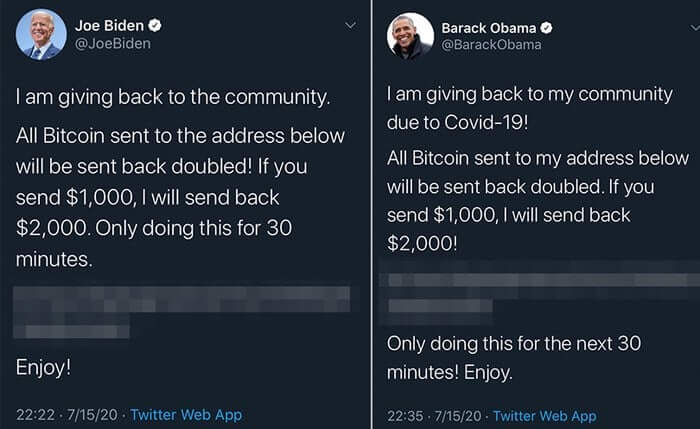
I am giving back to my community due to Covid-19!
All Bitcoin sent to my address below will be sent back doubled. If you send $1,000 I will send back $2,000!
Only doing this for the next 30 minutes! Enjoy.
And this, obviously, is a scam
Correct. We’ve seen cryptocurrency scams use a similar lure in the past, albeit never on this scale before. Potential victims are told that all they have to do is send X number of Bitcoin to a wallet in order to receive more Bitcoin in return. Sadly, some people fall for such confidence tricks.
So how did all these accounts get hijacked?
There are a number of ways in which online accounts can get hijacked.
These include, for instance:
- You might have made the mistake of reusing your Twitter password elsewhere on the net. If the other place suffers a data breach, a hacker might try to use that same password against your Twitter account. Two-factor authentication can help protect against this, but the best advice of all is to never reuse passwords.
- You might have had your password stolen from you via a phishing attack or keylogging malware. Two-factor authentication can also help protect against this. In addition, password managers and security software can also provide a layer of defence.
- You might have mistakenly told someone your password. Passwords should be secret. It’s hard to believe, however, that someone is big enough buddies with Bill Gates, Kanye West, Uber, and the rest to have had their passwords discussed over a candlelit dinner.
- Your account could be hijacked by a third-party app that is compromised. If the app had access to your Twitter account it could post tweets without your permission. An attack just like that happened to my Twitter account a few years ago. But in this case the messages claim to have been posted by the “Twitter web app” rather than a third-party app.
- A vulnerability. A hacker could exploit a previously unknown vulnerability on the Twitter website to post a message without authorisation. This might explain why so many different Twitter accounts were able to be compromised.
However, it appears that what actually happened was much worse than all of the above.
Stop teasing. Tell me how it happened
At the moment the suspicion is that a hacker managed to gain access to Twitter’s administration panel – a section of Twitter’s infrastructure that is supposed to be restricted to a small number of Twitter staff, helping them to troubleshoot problems with users’ accounts.
As Motherboard reports, Twitter is investigating whether one of its employees was responsible for the hack or might have granted hackers access to the internal administration tool.
From the administration panel, a malicious user could reset the email address associated with a Twitter account (thus granting someone else access to it), and disable two-factor authentication.
So it wouldn’t matter if you had 2FA enabled on your Twitter account, this hacker could have gained access to it?
Correct.
And presumably they could do anything they want with your account?
If they wanted to, yes. In this case it appears they chose to run a “make money quick” cryptocurrency scam. But it could just as easily have been abused to read users’ private messages, or steal other information.
One question. They hacked so many high profile people’s accounts. Why not Donald Trump?
It’s surprising isn’t it? He is perhaps Twitter’s most famous user. Maybe Twitter has additional protections in place specifically related to the @realdonaldtrump account after it was deleted by a rogue employee a few years ago.
What’s Twitter doing about this?
Aside from investigating whether one of its employees might have been involved, and how it can harden its internal security, the site briefly prevented verified users from posting tweets. In addition, restrictions were put in place to prevent tweets being posted that contained Bitcoin addresses.
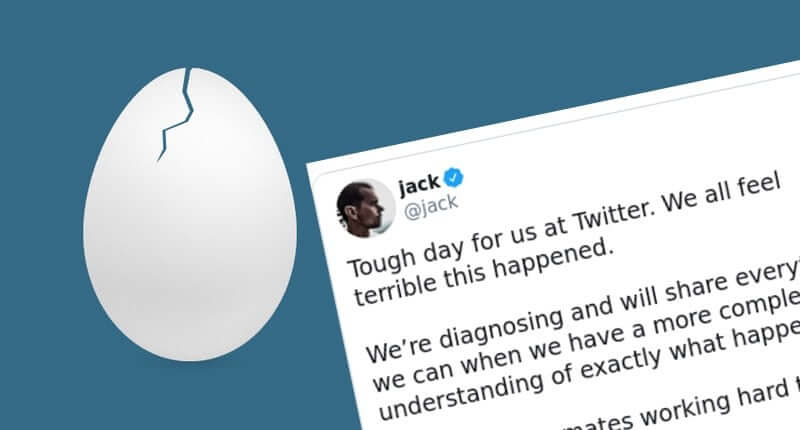
Twitter’s Jack Dorsey said the company would share more information when it had a “more complete understanding of exactly what happened.”
Tough day for us at Twitter. We all feel terrible this happened.
We’re diagnosing and will share everything we can when we have a more complete understanding of exactly what happened.
💙 to our teammates working hard to make this right.
— jack (@jack) July 16, 2020
So what do we know of the hackers?
Not much, and it’s hard to be definitive about how much money they have made from this scam. However, BBC News has suggested that the attack might be related to an Instagram account that posed a message saying that the hack was a “charity attack”. In the message, the Instagram user claimed that scammed money would “find its way to the right place.”
Is there anything I should do as a Twitter user?
Yes. Stop believing everything you read on Twitter. Even if it comes from a company, a reality TV star, or an account with a verified tick.
This actually is good advice even when Twitter hasn’t been hacked.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” The Twitter mega-hack. What you need to know” appeared first on TripWire
Source:TripWire – Graham Cluley
