The True Cost of a Security Breach
There have been many articles about the cost of a security breach. With the emergence of privacy regulations that assign penalties based on a business’ profit, or those that calculate a value for each compromised record, it is possible to calculate the cost of a breach based on those metrics. However, it would seem that these hard numbers are not detailed enough to placate many security professionals.
Too many cybersecurity professionals take the unnecessarily broad leap from the quantifiable, to the speculative with ill-formed notions. Specifically, when discussing data breach costs, the topic of reputational damage always seems to enter the conversation. Yet, to many C-Level executives, this is perceived as a sensationalist ploy, brinksmanship, and an empty threat, and rightfully so. Nothing detracts more from an important message than an unquantifiable peril.
If we look to history as our guide, many disasters far greater than privacy violations have occurred, and the responsible companies have emerged, seemingly unscathed by the incident. Some organizations have blundered to the point of causing human casualties, but they still thrive. There is no need to cite specific names and events, as we are all too familiar, and this is not meant to be a festival of the macabre. From a purely cybersecurity perspective, the continued success of even the costliest breaches is evident.
The point is that a company’s reputation will be governed by market variables, such as its solvency, and its prior reputation. When we, as security professionals engage in inflammatory and alarmist speculation, we dilute the importance of our message. Ironically, the reputation that we damage may be our own.
It has often been stated that security professionals don’t speak the “language of the business”. This has always been confusing, as it doesn’t make sense to a purely technical crowd. However, when articulating the importance of a security initiative, there are some simple steps that should be observed to present the risk using a business perspective.
Know the Business
Psychologists live by the tenet of “meeting the client where they are”. This means that in order to reach a client, you must relate to their problem from their perspective. The same holds true for business. Security is not the primary goal of most businesses. The primary goal is always making enough money to keep the business afloat. How does your business accomplish that? When attempting to gain funding or a security initiative, it is important to perform the time-honored Return On Investment (ROI) calculation.
With many security projects, an accurate ROI is difficult to achieve. You cannot predict how many attacks you will definitively prevent. However, when it comes to breach calculations, this is a highly achievable number, but not without some diligent work.
Know The Data
The records of a financial firm will be quite different from the records of a non-profit organization, or a medical office. In some cases, the records may be stored across multiple systems, in varying states of completeness. In order to quantify the value of the data, you must perform an inventory of where all the data resides, and exactly what information that data contains.
In some cases, a system will only contain limited information, so the records will be worthless if breached. In other cases, systems may contain valuable data, including Personally Identifiable Information (PII), and in the case of a health care system, valuable medical data. Data classification can put a priority value on that data, but in order to present a case for a security budget to a Board of Directors, a true monetary value must be assigned to that data. This can be done using many of the benchmarks that already exist from the available media coverage and industry reports.
Got Spreadsheets?
Comparative information from other breaches should be presented along with the regulatory sanctions relevant to your business. For example, If your business adheres to GDPR, the penalties are based on the organization’s annual profits. If your business is subject to the CCPA, there is a per-violation penalty. If your organization adheres to multiple regulations, that should also be included. When these numbers are gathered for each system, and the number of potential records at stake, a clear business picture starts to materialize. For example, an organization with a global reach might be represented with the following:
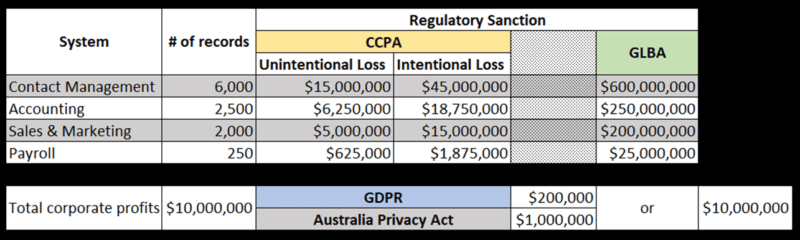
Move from the Simple to the Complex
When preparing a presentation about the value of the data, it may be best to move from the least valuable, to the most valuable records, showing the escalating costs of a breach. By doing so, when delivering the information, you can gauge the attention in the room, adjusting the presentation without overwhelming the audience. Your presentation should also stress that penalties are not levied against first-time violations. Rather, they are assessed against contributing factors, such as repeat offenses. Remember, the point here is to convey business information, not fear or threats.
Expand to the Peripheral Security Initiatives
If your organization is already doing everything correctly, there may still be some gaps that can be improved upon. For example, if all the sensitive data is encrypted, but you are not in full control of all the encryption keys, this is the time to work towards getting a key management platform. Or, if you are constantly chasing configuration drift, it may be time to work towards purchasing a configuration management system.
Follow the Metrics, Avoid the Sensational
Security metrics can now be more accurately tracked than ever before. It may take a lot of effort to track down all the data, and then correlate it to the true value as it relates to your particular business, but in the end, it will gain more buy-in than the hollow prediction of the reputational damage. The metrics are remarkable on their own. Sensationalism doesn’t serve us well.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc
The post ” The True Cost of a Security Breach” appeared first on TripWire
Source:TripWire – Bob Covello
