The New CIS Community Defense Model (CDM) Brings Security Within the Grasp of All Small Organizations

Part of operating an effective security program is the ability to never rest upon any previous success. When guarding against an adversary, yesterday’s success is quickly eclipsed by the dynamic shift in the attacker’s tactics. Just as a doctor “rules out” a particular diagnosis, an effective attacker first searches for well-known vulnerabilities using catalogs of offensive exploits. These are part of the attacker’s playbook.
Thankfully, the Center for Internet Security (CIS) has always been and continues to be dedicated to offering some of the best guidance for those entrusted with protecting online systems. Similar to the necessity of continuous improvement for any security program, the CIS team devotes itself to improving upon its previous models.
Initiated in 2008, The CIS Controls are now in version 8, undergoing changes not only over the course of its journey but also in regards to its stewardship and its name. Initially known as the “Top 20 Controls,” “The CIS Controls” are a vast and considerable undertaking for any organization, so the authors have endeavored to make the job easier for organizations of varying sizes. For example, Version 7 introduced three “Implementation Groups” (IG), which provide a categorized approach for achieving the security level that suits an organization’s capabilities.
Over the last few years, and in further pursuit of the goal of offering the best practice guidelines for everyone, the CIS created the Community Defense Model (CDM). The model, now updated to version 2, serves a few purposes. One is stated in the executive summary:
Enterprises naturally want to know “How effective are the CIS Controls against the most prevalent types of attacks?”The CDM was created to help answer that and other questions about the value of the Controls based on currently available threat data from industry reports.
Other purposes flow from the overall methodology of the document’s authors, such as:
- Mapping CIS Safeguards to the MITRE ATT&CK framework.
- Identification of the security function, that is, independent of any specific attack, the ability of a CIS Safeguard to defend against one or more attacker (sub-)techniques.
- The use of authoritative data sources to identify the top five attack types that enterprises should defend against.
- The use of authoritative data sources to determine the attack pattern, which are the sets of attacker (sub-)techniques used in each attack type.
- Identification of the security value, the benefit of implementing a CIS Safeguard to defend against an individual attack or a group of attacks.
The CDM fulfills a very desperate need in that the CIS controls, coupled with the MITRE ATT&CK framework, create a seemingly overwhelming task for many small organizations. In too many instances, a company will turn away from these lofty goals, opting for a home-grown version of cybersecurity that often fails. The CDM offers the ability to accomplish a true basic hygiene posture in a manageable way.
If one had to devise a single-sentence summary of why an organization should use this model, it would be: The CIS CDM can be directly and empirically mapped to its value. A closer examination of the CDM bears this out. To start, the top five attack types are identified. Malware, Ransomware, Web Application Hacking, Insider Privilege and Misuse, and Targeted Intrusions are addressed with the goal of prevention. Even the most basic defensive steps of IG1 can result in a protection level greater than 77% and up to 86% for each specific type.
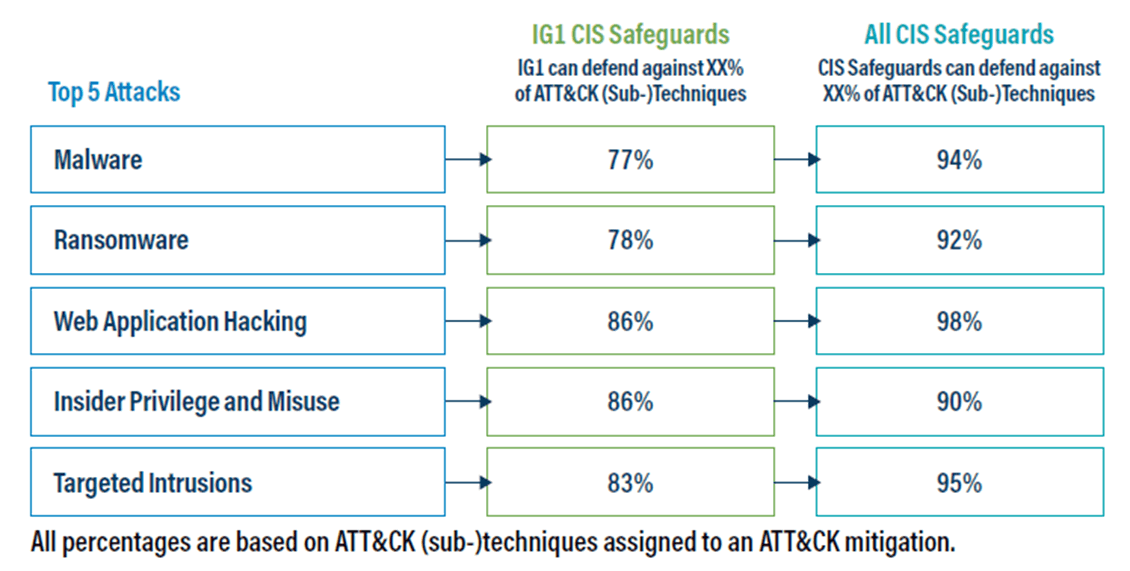
While comprehensive, the CDM makes it clear that not all ATT&CK (sub-)techniques map to CIS safeguards and not all ATT&CK (sub-)techniques can be mapped to a mitigation strategy. These are included in the appendices in the CDM. Other appendices include ATT&CK Navigator visualizations for each of the attack types outlined in the document. This is the empirical data that outlines the known attack patterns of the adversary. It is a playbook of defense.
Overall, the level of detail offered in CDM version 2.0 is breathtaking, but not as initially intimidating as the full CIS Controls. This gives small organizations a better opportunity towards establishing an effective cybersecurity program based on an established and industry-recognized set of criteria. It is still not an easy journey, but the CDM moves cybersecurity within closer reach for many who may otherwise choose other unproven methods.
The fact that many of the efforts of the Center for Internet Security are made possible through the work of volunteers shows that we can win the war on cybercrime. It demonstrates the selfless passion and commitment that many still have towards making the internet a safe place.
Of course, if you need help getting started with the CDM or even if you are already fully immersed in your efforts at applying the CIS Controls in your organization, Tripwire is here to help: https://www.tripwire.com/solutions/cis-20.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” The New CIS Community Defense Model (CDM) Brings Security Within the Grasp of All Small Organizations” appeared first on TripWire
Source:TripWire – Bob Covello
