The Evolving Threat of Ransomware

Currently, ransomware is the most prominent cyber threat to businesses and individuals. Ransomware attacks are growing more prevalent as cybercriminals find new ways to profit from them. According to CyberEdge’s 2021 Cyberthreat Defense Report, 62% of organizations were victimized by ransomware in 2019—up from 56% in 2018 and 55% in 2017. This rise is arguably fueled by the dramatic increase in ransomware payments. More than half (58%) of ransomware victims paid a ransom last year, which is up from 45% in 2018 and 39% in 2017.
There are three key factors that make ransomware more profitable for attackers: cryptocurrencies, Ransomware as a Service (RaaS), and geopolitical safe-havens.
Cryptocurrencies provide a safe mechanism for threat actors to be paid while reducing the likelihood of authorities being able to track the money. All contemporary ransomware will ask the victim to send the ransom money to a cryptocurrency wallet address. Ransomware as a Service permits sophisticated ransomware gangs to sell their harmful services to anyone who wants to participate in this criminal enterprise. RaaS providers charge a percentage of the profit generated by the purchaser of the service. The malevolent organization “REvil” promoted RaaS by carrying out multiple ransomware attacks as well as supporting and giving tools to individuals interested in using its service.
Geopolitical safe havens allow governments to turn a blind eye to their citizens’ cybercrime activities as long as the cybercriminal isn’t targeting domestic companies or persons. Russia and China are the most notable countries in the geopolitical cybercriminal sector since they are notorious for not pursuing recognized cybercriminals for cyberattacks that they commit or assist in on a global scale.
Since the first incidence of ransomware in 1989, which is known as the “AIDS Trojan,” the threat of ransomware has evolved, aided by technological advancements and globalization. The AIDS Trojan demanded a $189 ransom payment from its victims in order to recover their data. While $189 may not seem like much, when compared to the time and effort spent developing the ransomware and the incurred risk, infecting many victims may drastically shift the motivation. In 2020, the average ransomware payment to threat actors was $200,000, with the highest reported payment being $40 million. Keep in mind that these figures may not be exact because they are based on publicly available information. For fear of damaging their public image and reputation, many corporations do not disclose these types of activities. Large ransoms, coupled with reduced or non-existent prosecutions, are an attractive incentive for threat actors.
How Ransomware Works
Ransomware is more than just the mere technical mechanics of unleashing malicious software to a wide audience and hoping for a payout to follow. The most successful ransomware criminals perform a lot of due diligence in order to maximize the payment.
Prior to an attack, threat actors perform reconnaissance on their target to learn about the infrastructure they are working with in order to discover exploitable flaws. Cybercriminals may spend months learning about their target, gaining a better understanding of a company’s operations. Certain vulnerabilities such as operating system flaws can be exploited by cybercriminals to deliver the harmful payload.
In many cases, the attackers will also aim to discover effective avenues of social engineering against the staff to unleash the ransomware. A social engineering operation will aim to influence an employee targets into unknowingly assisting the attacker.
Organized attackers will plan their assaults with care and patience, waiting for the right time to strike. The reconnaissance performed by the cybercriminals is the key to any successful instance of cybercrime.
Most ransomware is designed using public-key cryptography. Public-key cryptography is a cryptographic algorithm that encrypts and decrypts data using a pair of keys to prevent unwanted access or usage. Typically, ransomware encrypts as much of the victim’s data as possible using the public key, which can only be decrypted with the threat actor’s private key. The malicious actor will threaten and demand money from the victim in order to expedite the ransom procedure. The most common threats include deleting the victim’s data if they do not cooperate within a specific time frame, damaging the device, or publicly disclosing the victim’s data.
One of the reasons not to pay the ransom is because the victim cannot be certain that the threat actor will send a decryption key or keep the data private. While the victim cannot be certain that the threat actor will keep their part of the agreement, according to the CyberEdge Report, “Cybercriminals have learned that withholding data following payment receipt is bad for business.” Unfortunately, the usual reactions to ransomware have become a self-fulfilling prophecy, propelling ransomware’s influence over organizations. The three data sets that show the self-fulfilling cycle of ransomware are as follows:
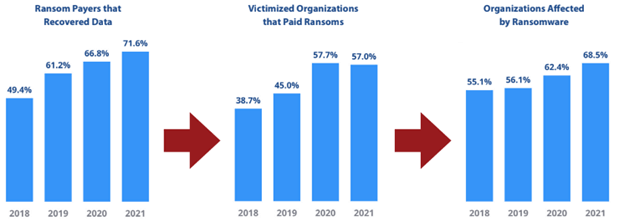
CyberEdge 2021 CDR Report v10 ISC2 Edition, page 21, figure 15.
Businesses need to prepare and protect themselves before they are victimized. One of the main goals in balancing risk management and cybersecurity isn’t to be invincible to cyber threats. The goal is to not be an easy target so that the criminal can find “easy pickings” elsewhere.
Today’s Ransomware
Not only has today’s malware evolved exponentially from prior incarnations, but it is also far more powerful and widespread than preceding ransomware variants. Due to characteristics incorporated by malware creators in the new varieties of ransomware, modern ransomware can have disastrous consequences and be more difficult to analyze and detect. Previously, ransomware such as the “AIDS Trojan” featured a simple workaround that allowed the victim to decrypt the symmetric key and avoid paying the ransom. Today’s malware, on the other hand, is far more sophisticated. One can imagine future ransomware with greater, more nefarious capabilities.
To protect against these types of risks as a corporation, a few cybersecurity fundamentals must be in place such as tools for avoiding, identifying, and remediating cyber threats. Basic cybersecurity fundamentals such as the principle of least privilege, separation and segregation of duties, secure on-boarding and off-boarding processes, multi-factor authentication, and cybersecurity awareness training are a few of the most crucial cybersecurity fundamentals that every firm should adopt.
Of course, Tripwire is here to help you on your organization’s journey to a robust cybersecurity
environment, as well.


Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” The Evolving Threat of Ransomware” appeared first on TripWire
