Survey: Nearly Half of Manufacturers Suffered a Digital Attack in the Last Year

Confidence isn’t new when it comes to cybersecurity. All the way back in 2015, for example, 86% of security professionals working in the energy sector told Tripwire that they were confident they could detect a breach in a week. Just less than half (49%) said it wouldn’t take them longer than a day to spot an attack.
It was the same story a year later when Tripwire surveyed infosec professionals in the retail sector. Most (95%) respondents said their organization could detect a breach within a month. That was the case even with 48% of survey participants admitting their breach detection products were just partially integrated.
Those statements weren’t consistent with the reality of the times, however. As an example, Mandiant’s M-Trends 2015 report stated that the average period for spotting an advanced persistent threat was 205 days. The 2015 Data Breach Investigations Report gave a similar estimate when it said that two-thirds of targeted attacks took months to detect.
These findings raise the question: Is this overconfidence still shaping security professionals’ expectations? What’s the situation look like in other sectors?
New Decade, Same Confidence
Make UK answered that question in sharing the results of its Cyber Security Survey 2021. Indeed, nearly nine in 10 (87%) of respondents in manufacturing told the UK manufacturers organization that they had the necessary tools, processes and technology to prevent or protect against a security incident. When asked to clarify what tools they were using, 97% manufacturers said they were using antivirus software and firewalls to secure their web connections. Just less than (90%) noted that they were using network-wide and system updates.
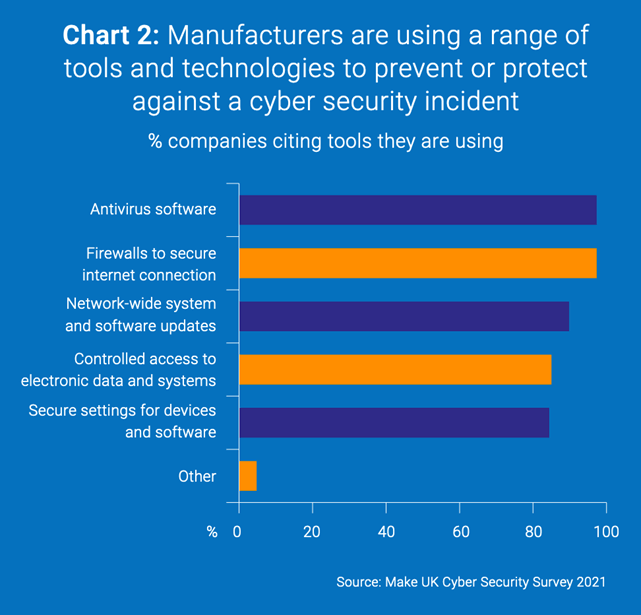
Approximately the same percentage (91%) went on to state that they had the resources to adequately assess digital security risk.
Once again, however, it appears that security professionals are overconfident in their employer’s breach preparedness. How else could 47% of manufacturing companies surveyed by Make UK have experienced a digital attack between May 2020 and May 2021? Of those victims, 63% said that the attacks ended up costing them up to £5,000. More than a quarter (26%) revealed that the incidents carried a price tag as high as £50,000, while six percent indicated that they lost more than £100,000 in those attacks.
Incident detection and response isn’t getting any easier for manufacturing, either. That’s because attacks against this sector are generally on the rise. Beazley found that the number of ransomware attacks reported to its breach response services increased 156% between Q4 2019 and Q1 2020, for instance. Similarly, NTT observed a 300% increase in the number of digital attacks targeted against manufacturing organizations for the rest of the year. That threat activity helped to make manufacturing the second most-attacked industry in 2020, reported IBM.
Behind the Stats
Several factors are behind this growing number of digital attacks in the manufacturing sector. First, manufacturers are joining other organizations in embarking on their digital transformation journeys. As quoted by Make UK in its report:
Make UK research tells us that manufacturers are shifting towards more smarter manufacturing models. While this must be encouraged, businesses also need to be aware that increased digital connectivity can lead to increased vulnerability, particularly as connected products are often used to store and transmit sensitive data, sometimes outside of the business itself, opening opportunities for a cyber-attack, particularly around data theft.
Second, manufacturers aren’t implementing the necessary security measures to address these risks. Antivirus software and firewalls offer some levels of protection, but they don’t do much in the face of more sophisticated attacks such as fileless malware and network incidents involving lateral movement. What’s more, nearly half (44%) of manufacturers said that they weren’t offering security training to their staff at the time of Make UK’s survey, with (66% admitting that digital security wasn’t a regular item on their Board’s monthly agenda.
The issue here isn’t always overconfidence. Some manufacturers don’t know how to get started. Meanwhile, others (59%) said that the cost of building a digital security program stood in the way of their organizations better defending themselves against digital threats.
How Manufacturing Organizations Can Move Forward
Manufacturing organizations need a cost-efficient way to defend themselves against digital attacks. Towards that end, Make UK includes 10 tips from the National Cyber Security Centre (NCSC) at the end of its survey. These include the following four recommendations:
- Use a risk management program to assess the risks confronting their information and systems. It’s crucial for manufacturers to have complete visibility of their environments to obtain an accurate vulnerability and risk profile. Subsequently, they need to be able to monitor their enterprise assets, industrial networks and DevOps environments.
- Improve their ability to detect malware. The way to do that is to have an automated way of receiving detailed reports on relevant system changes as they occur. It also helps to have the ability to analyze suspicious file behavior in quarantined environments so that their production systems always remain safe.
- Manage their assets’ secure configurations. There’s no way that organizations will be able to succeed unless they have the complete network visibility mentioned above. With that comprehensive view, it will take organizations less time to detect instances of configuration drift and return their assets to their designated baselines.
- Ensure they have the means to detect and investigate an incident. That begins with real-time change intelligence. From there, organizations can use that information to close the gap between their IT and security teams. This will help to save time and resources when it comes time to investigate potential threats.
For more tips on how to keep your manufacturing organization safe against digital threats, download your copy of Make UK’s survey here.
The post ” Survey: Nearly Half of Manufacturers Suffered a Digital Attack in the Last Year” appeared first on TripWire
Source:TripWire – Dean Ferrando
