State of Insider Data Breaches in 2020
Organizations protect critical assets and sensitive information from the outside world by continually updating their security controls and policies. However, the origin of a breach is not always outside of the organization, and recently, insider breaches have gained attention amid an increase in the flexibility of tools for information sharing.
Insider threats can be accidental or intentional, but the impact of insider breaches remain the same. Negligence at the organization regarding data privacy requirements and compliance can cause catastrophic data loss. To implement effective mitigation measures, employees must be aware of their responsibility towards the usage and sharing of data. With recent changes in data protection and privacy laws, various companies have seen a significant impact on their current security practices and controls.
Insider data threats are increasing more than ever before, and these threats are a major concern when it comes to risk management for companies. The Egress 2020 Insider Data Breach Survey identifies the challenges from the viewpoint of IT leaders and compares them with the perspective of employees regarding data protection and their responsibility.
In the previous year’s report, IT leaders showed rising concerns for the risk of insider data breaches. However, employees denied that they have caused such violations. This indicates that there is a gap between employees and IT leaders in the ways that they perceive responsibility and ownership of the company’s data. The report for 2020 inspects the development of the effective mitigating approaches that companies have taken to manage insider breach risk. Another difference of this year’s report is the broader perspective on these breaches based on different regions along with the evolved questionnaire.
Survey Key Findings from the Insider Data Breach Survey
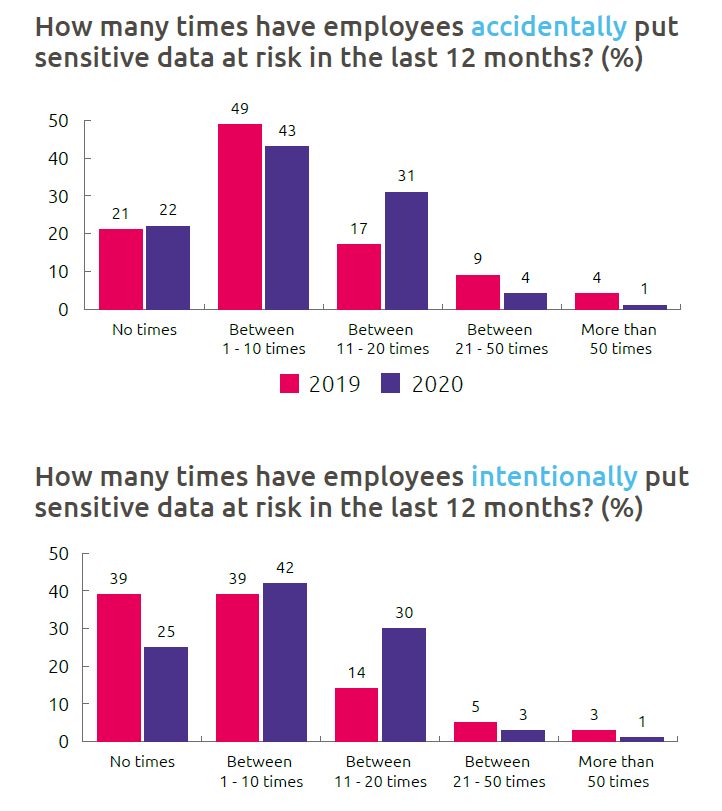
In this survey, 97% of IT leaders acknowledged the concerns regarding the insider breach risk for their organization. This indicates rising concerns in organizations, as this number increased by 2% from 2019. According to IT leaders, 78% of employees put data at risk accidentally in the last 12 months, while 71% of employees accepted that they or a colleague had inadvertently shared the organization’s information. On the other hand, 68% of employees agreed that they had not intentionally broken company policy for sharing the data, while 75% of IT leaders believed that employees had deliberately put data at risk.
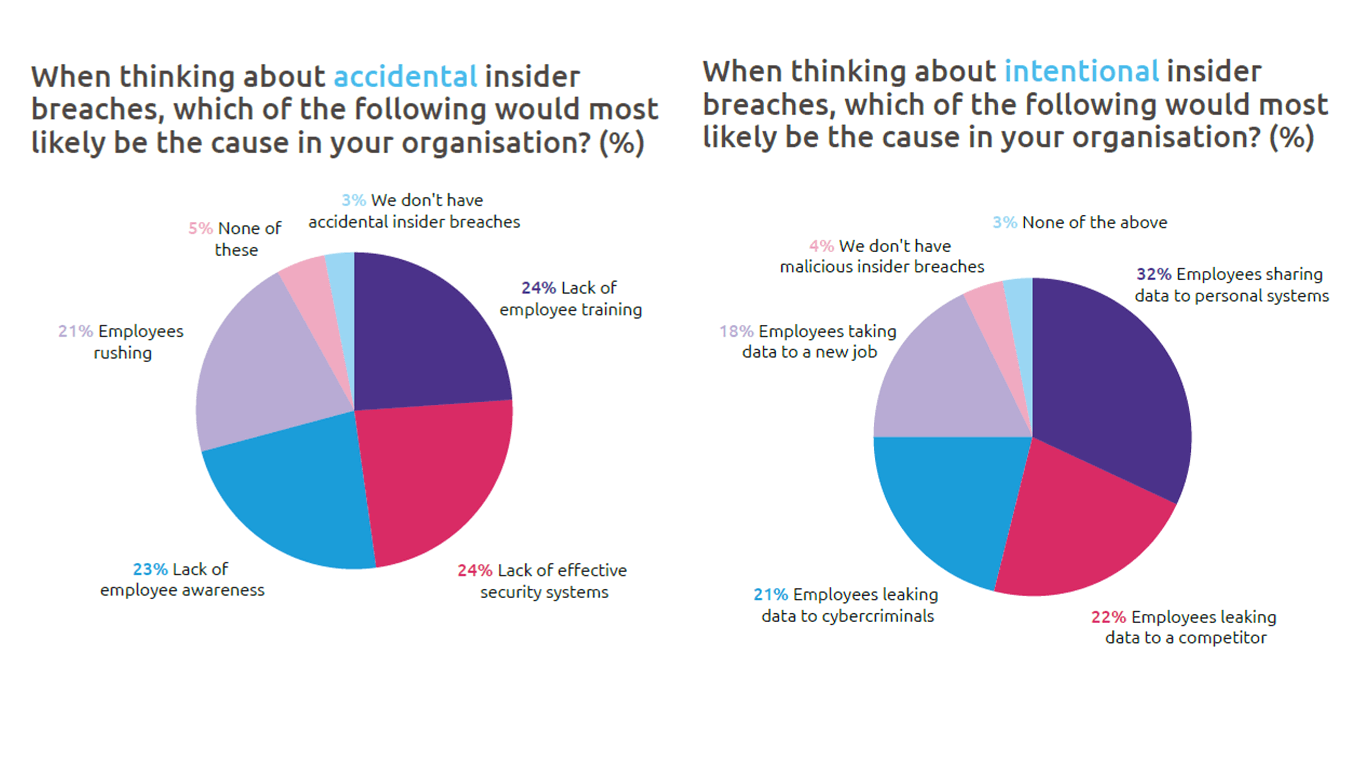
Insider breaches are mainly caused by sharing data to personal systems, followed by the leaking of data to a competitor and then cybercriminals. One of the widespread reasons behind this information (and common with the employees who might not have bad intentions) is employees taking the data to a new job. Departing employees take information with them when they feel a sense of personal ownership to it.
This reflects that employees perceive the responsibility towards data ownership differently than what is expected from them. With less defined boundaries, the challenge to protect internal information increases as employees work outside the physical limits, and the home environment changes the attitude of employees towards the data that they work on. For preventive measures, the first step is to identify sensitive data and the level of confidentiality for all types of data. The employee data is at the top in terms of accidental and intentional data, followed by intellectual property. With new data protection laws in place, customer data ranks third. This includes personally identifiable information.

Breach Impact
The reality has changed this year due to the enforcement of stringent regulations and compliance requirements for organizations. In 2019, IT leaders were more concerned about reputational impact due to insider data breaches, but in 2020, the main concern is financial implications. This shows that organizations are clear about how non-compliance of privacy regulations is going to cost them.
It is a challenge to get honest answers from employees when it comes to an insider data breach. When they were asked based on their personal responsibility towards data, only 8% admitted that they had accidentally shared information with an outsider.


Interestingly, when the question was amended for this year’s survey where employees were asked to share if they or a colleague had accidentally shared information externally, 27% admitted to having done so. This clearly shows that there is a gap between the number of reported incidents and the employees who admit and take responsibility for an incident. Insider breaches are mainly reported by the employees, and an increase in the unwillingness of admitting the truth can lead to an unsuccessful breach detection strategy.
Causes of Insider Data Breaches
The main reasons why an employee accidentally or intentionally shares data include being pressured or stressed, using a mobile device, tiredness and rushing/making a mistake. In some sectors such as healthcare, financial services and government, the data is highly sensitive, so the associated risk is above-average should the information be sent to the wrong person.
Employees are not always thinking as they ought to be regarding data ownership and security responsibilities. This introduces another layer of complexity to managing these breaches. With the seniority level, the rate of acceptance of data protection liability decreases. Policies that clearly indicate that all the employees share equal responsibility to protect data can bridge the gap between beliefs and expectations.
Looking ahead
The future seems worrisome with the increasing complexity and number of incidents. Currently, the primary source of reporting is the employee, and it leaves a significant loophole in the prevention strategies because an employee can choose to speak up or not. Therefore, a large number of incidents may go unnoticed and unreported. The statistics also indicate that insider data breaches will continue to rise.
The situation can be improved if IT leaders re-assess their mitigation and prevention strategies and build a technology stack that can respond dynamically to changing behaviors of the employees. It is better to be proactive and identify the risks based on behaviors and motivations. Proper on- and offboarding processes can be one such proactive approach.


Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” State of Insider Data Breaches in 2020″ appeared first on TripWire
