Sextortion Scams – How They Persuade and What to Watch for

Extortion, and especially “sextortion” emails, are becoming more frequent, and they can be extremely alarming when received. Such emails work by using threats to extort money, evoking intense fear. This type of correspondence comes in many guises and features various elements, but essentially, they work in the same way.
These activities can refer to real-life experience such as cheating on a partner or online behaviors such as visiting porn sites. They are called sextortion scams because there is an element of sexual behavior to them, something which is highlighted by scammers as undesirable and shameful. They usually threaten to expose the victim’s shameful activities to colleagues, friends, and family. Scammers then ask for payment to keep this a secret. But there are some that don’t have sexual elements. Instead, threats of harm are used to extort money. For example, some threaten to harm or kill the victim unless a fee is paid quickly.
Although sextortion scams are not new, they have evolved drastically in the past few years.
Historically, victims of such scams were usually young women, typically targeted by someone they dated in real life or met online and who was in possession of private or sexual images of them. More recently, sextortion attacks started casting a wide net and targeting private individuals who have never had any prior contact with their perpetrator. Most ask for payment in cryptocurrency, usually bitcoin. This is a convenient payment option for cybercriminals because bitcoin, as virtual money, has little or no legal regulation across different countries. This makes it a perfect choice for criminal activities.
These types of emails often have common, repeated elements, as shown in the following diagram:
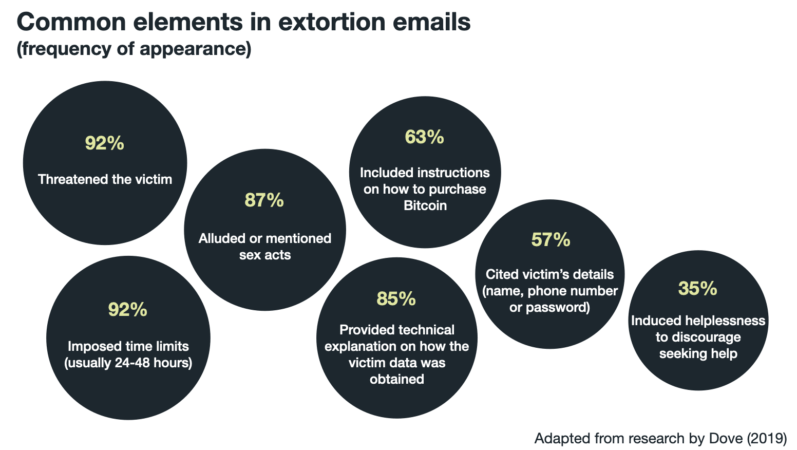
Common themes and techniques were also present in such correspondences. (See table below.) Their purpose is to evoke intense fear and emotion as well as to persuade the recipient that the correspondence is genuine, the threat is real, the transaction is reasonable because it is a payment for keeping the details confidential, the fight is futile, and the best course of action is to pay the requested amount.

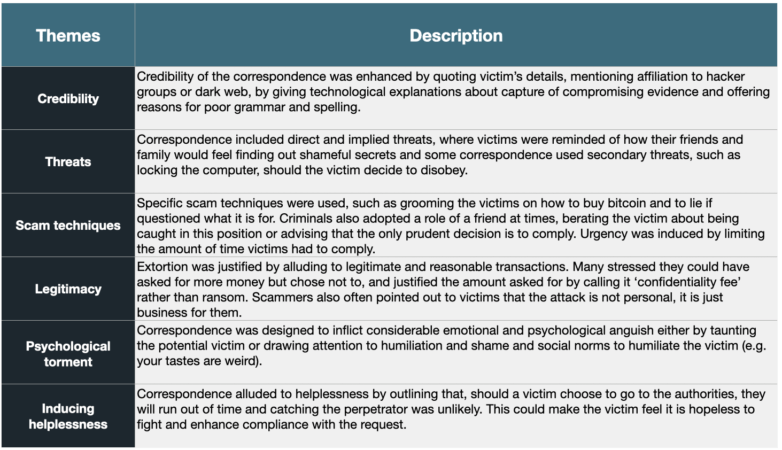
Credibility
To enhance credibility, statements such as “I am a member of an international hacker group” and “My nickname in dark net is Gray24” are often included. Without specifically saying it, these statements are there to persuade the victim that the person demanding the ransom is a skilled attacker who could feasibly obtain such details about the victim. Complex technological explanations were often given as to how the victim’s computer was compromised.
Some examples include an apology and an explanation for bad grammar: “I am apologise for my grammar, I’m from China.” As many scam warnings concentrate on bad grammar as a sign that the correspondence is fraudulent, offering an apology can act as a credible explanation for this warning sign.
Threats
These types of scams rely heavily on threats, often direct or implied. Direct menacing includes threatening to send the captured video of the victim to friends, family, and work colleagues. Some include additional threats like telling the victim that the malware, which can track activity, was installed on their computer and that their device will be locked if they try to do anything about the correspondence.
Implied threats are more subliminal. These include thoughts about what might happen if the victim was exposed to friends and family, e.g., resulting in shame or a loss of a relationship.
Here is an example of an implied threat taken from sextortion correspondence: “I don’t think that what you look at on your computer when no one is around is really awful but when all colleagues relatives and friends receive video record of it is definitely terrible news.”
These threats are specifically designed to evoke fear, which is a powerful primal drive that can severely compromise rational thinking and careful decision making. Additionally, some people experience fear more intensely than others and will therefore be more fear-averse, wanting to comply to make it go away quickly. People who are fear-averse will be particularly vulnerable to this type of scam.
Urgency and grooming
Scams frequently pair evoking fear with a sense of urgency. This is because fear, like other visceral influences (strong emotion, sexual desire, hunger etc.) will be short-lived, and this is when the person will be starting to think more clearly. This is why applying urgency is key. The goal is to get a potential victim to act while they are irrational, and urgency will aid this process.
Victims are typically given 24-48 hours to comply. Some examples go a step further, telling the potential victim that the time is tracked from the moment the email is opened.
Other techniques included grooming the victim in order to elicit secrecy by reminding them to be secretive when purchasing bitcoin and underscoring the point that their future depends on it. Any detection will lead to release of the footage the scammer has on the victim, the logic goes.
Legitimizing the crime
Many emails of this nature have some component where the perpetrator is trying to normalize this abhorrent activity. They may point out that the requested money is not an unreasonable amount, even calling it a confidentiality/privacy fee or a donation. Some pointed out that it’s not personal, that this is just a job, and that the victim should not hate them for what they are doing. This likens extortion to something like debt collecting, where a fee that a victim may not be happy about is legally enforced.
Psychological harm and helplessness
In almost all of these sextortion scams, victims are presented with words and phrases that are likely to evoke shame and humiliation, such as ‘nasty,’ ‘dirt,’ ‘sordid,’ ‘unpleasant,’ ‘unbridled’ etc. Repeating words like this throughout the correspondence will prime the victim to feel shame and lead to an increased fear response. Some included specific statements that evoke social norms and are designed to alarm.
Here is an example of how social norms are evoked in such correspondence: “I was shocked by what I saw!!! I want to say that you are a BIG pervert. Your fantasies are shifted far away from normal course.”
Many scammers rely on social norms to execute scams. We shape our behavior according to societal norms; therefore, a potential victim may feel that the society would judge their conduct if this got out, and they then pay the ransom to avoid shame and humiliation.
Many examples of this correspondence also include a segment on why a victim should not report the crime to the authorities: “At this point you may be thinking ‘I’ll just go to the cops,’ which is why I have used a fake name, fake return address and taken steps to ensure this letter cannot be traced back to me.”
The purpose of this is to render the victim helpless. By reminding the victim that there is nothing they can do about this, increasing the likelihood of resignation and eventual compliance.
Why sextortion emails work
Many people think they would never fall for something like this, but realistically, many people succumb to such phishing attacks because the story may sound plausible to them. They oftentimes also have no way of investigating if an explanation given to them by the scammer is credible. The fear will do the rest, leading to irrational decisions fueled by shame.
How these types of phishing attacks work:
- Visceral influences such as panic and fear are very influential. Rational advice will not be recalled when someone is under emotional stress.
- Persuasive elements subliminally influence decision making and encourage compliance, such as the application of urgency to make sure the person acts while they are under the visceral influence.
- Offering technological explanations will sound convincing enough to most people who have a limited knowledge of technology. Many won’t have friends who are able to advise them on whether these explanations are credible.
- Careful use of rhetoric in such emails, such as pointing to shame and social norms, induces semantic priming, which will further influence compliance and lead to resignation.
- Induced helplessness will encourage victims to surrender the fight. This is even more true of people who are fear averse, as they would most likely feel motivated to make it all go away quickly due to the level of psychological discomfort.
So, what should be done?
The best thing to do in any situation where emotions are high, there is a presence of fear, or psychological/emotional discomfort is present is to wait a while. These feelings are fleeting but can severely compromise a person’s ability to process information and make sound decisions.
The next thing to do is to share the experience. Report it to the authorities, and get advice and help on what to do. Even if there is a high likelihood that the threat is real and not just a scam, sextortion attackers don’t profit from outing you to your friends and family. They profit from getting money. And sharing such stories and correspondence examples leads to general awareness of this type of fraud.
The post ” Sextortion Scams – How They Persuade and What to Watch for” appeared first on TripWire
Source:TripWire – Martina Dove
