Ransomware Gangs Scavenge for Sensitive Data by Targeting Top Executives

In their attempt to extort as much money as quickly as possible out of companies, ransomware gangs know some effective techniques to get the full attention of a firm’s management team.
And one of them is to specifically target the sensitive information stored on the computers used by a company’s top executives, in the hope of finding valuable data that can best pressure bosses into approving the payment of a sizeable ransom.
Although the technique of prioritising the theft of data from managers’ PCs is not a new one, it has been highlighted by a report from ZDNet over the weekend.
In his report, ZDNet journalist Catalin Cimpanu describes a conversation he had last week with a company that paid millions of dollars following an attack by the Clop ransomware.
“…in recent intrusions, a group that has often used the Clop ransomware strain has been specifically searching for workstations inside a breached company that are used by its top managers.” “The group sifts through a manager’s files and emails, and exfiltrates data that they think might be useful in threatening, embarrassing, or putting pressure on a company’s management — the same people who’d most likely be in charge of approving their ransom demand days later.”
As regular readers know, in recent years ransomware gangs have not just increasingly targeted large organisations in their attacks in preference to thousands of home users. They have also valued highly the prize of exfiltrating sensitive data such as business plans, financial details, and intellectual property that corporate victims would dread falling into the public domain or their commercial rivals.
And where better to find such commercially sensitive information than on the workstation of a chief executive, chief financial officer, or communications director.
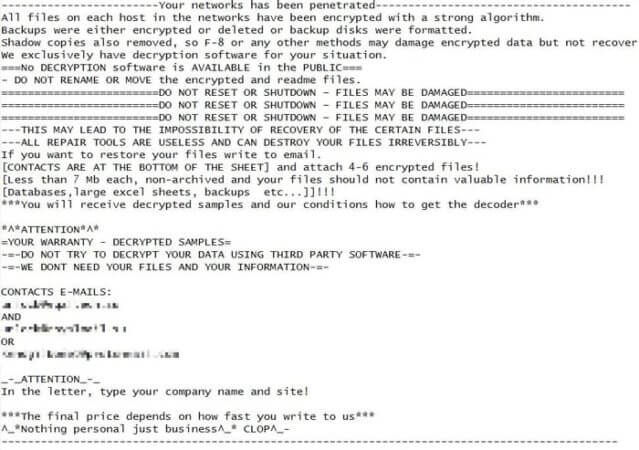
According to Lawrence Abrams of Bleeping Computer, the technique is not one unique to the Clop ransomware – but has also been seen in attacks using other notorious ransomware families such as Ragnar Locker, Egregor, and Maze.
This may be a signal of something that is little understood outside of the security world – the people hacking your network and exfiltrating your data may be different than those who created the ransomware.
Some of the most egregious ransomware operates as a service, with the malware developers leasing their malicious code to less-technically minded cybercriminal affiliates who may use them in attacks, or even hire other specialists in unauthorised network intrusion to infiltrate a company’s network to steal sensitive data and then do as much damage as possible.
According to Abrams, when a corporate victim pays a ransom following such an attack the proceeds can be split three ways between the operators of the ransomware, the affiliate, and the intrusion group.
So, what should your company be doing to protect itself against ransomware attacks like this?
Well, you should still be making secure offsite backups, and running up-to-date security solutions, while ensuring that your computers are protected with the latest patches against newly-discovered vulnerabilities.
Furthermore, you staff should be educated and made aware of the risks and methods used by cybercriminals, and made to use hard-to-crack, unique passwords to protect sensitive data and accounts as well as enabling multi-factor authentication. Sensitive data should be strongly encrypted wherever possible.
And I would further suggest that your company’s security team should consider where the firm’s most sensitive information is stored, and investigate how easy it might be for a hacker to access it. In short, you might uncover weaknesses in your business’s infrastructure if you attempt to hack your own company’s top executives rather than waiting for a malicious attacker to do the same.
To discover more ransomware prevention tips, click here: https://www.tripwire.com/state-of-security/security-data-protection/cyber-security/22-ransomware-prevention-tips/
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” Ransomware Gangs Scavenge for Sensitive Data by Targeting Top Executives” appeared first on TripWire
Source:TripWire – Graham Cluley
