Ransomware demands acts of kindness to get your files back

The great thing about working in the world of cybersecurity is that there’s always something new. You may think you’ve seen it all, and then something comes along that completely surprises you.
And that’s certainly true of the GoodWill ransomware, which security firm CloudSEK described this week.
In fact, the GoodWill ransomware stands out so much from the crowd that you might be forgiven for thinking that it is an April Fool’s joke that has somehow broken out at the wrong time of year.
Because the GoodWill ransomware isn’t interested in extorting money from you. It wants you to do something good for the world.
Like most other ransomware, GoodWill encrypts the usual file types – documents, databases, photographs, and videos – locking away your content.
But rather than demand thousands of pounds worth of cryptocurrency in exchange for the decryption key, the GoodWill ransomware wants you to do something good for the world (and provide some video proof):
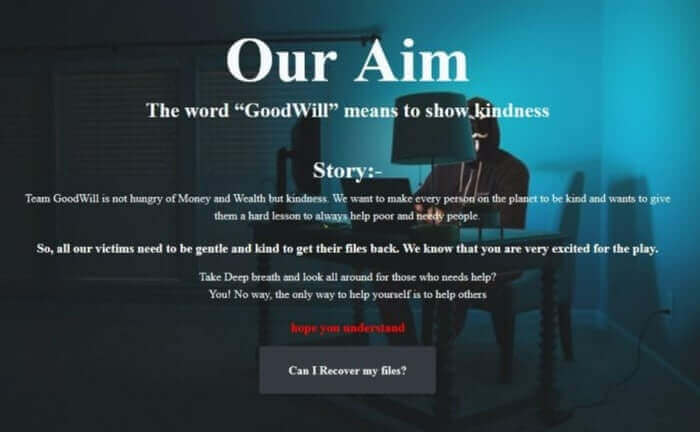
Our Aim The word “GoodWill” means to show kindness Story:- Team GoodWill is not hungry of Money and Wealth but kindness. We want to make every person on the planet to be kind and wants to give them a hard lesson to always help poor and needy people. So, all our victims need to be gentle and kind to get their files back. We know that you are very excited for the play. Take Deep breath and look all around for those who needs help? You! No way, the only way to help yourself is to help others hope you understand
In a multi-page ransom note, the GoodWill ransomware tells you to perform three acts of goodwill.
The first request is for you to donate new clothes and blankets to the homeless. Victims are told to make a video of them giving assistance to people sleeping rough, and to post it on their Facebook, Instagram, and WhatsApp to encourage others to help those in need.
The second requested act involves taking five poor children (under the age of 13) to Dominos, Pizza Hut, or KFC, and allow them to order any food that they wish.
Take some Selfies of them with full of smiles and happy faces, Make a beautiful video story on this whole event and again post it on your Facebook and Instagram Stories with photo frame and caption provided by us. Take a screen shot of your posts, snap of restaurant’s bill and send email to us with valid post link, later our team will verify the whole case and promotes you for the next activity. Help those less fortunate than you, for it is real human existence.
The final requested act of goodwill involves providing financial assistance to those who need urgent medical assistance, but cannot afford to pay for it themselves.
Visit the nearest hospital in your area and observe the crowd around you inside the hospital premises. You will see that there will be some people who need certain amount of money urgently for their medical treatment, but they are unable to arrange due to any reason. You have to go near them and talk to them that they have been supported by you and they do not need to worry now, Finally Provide them maximum part of required amount. Again, Take some Selfies of them with full of smiles and happy faces, Record Audio while whole conversation between you and them and send it to us.
The ransomware attackers say that if you provide convincing evidence that you have done the above then they will provide a decryption tool (with key and video tutorial) for the recovery of the scrambled files.
Will any of the ransomware’s victims go along with the scheme? I guess the first we will know is if we begin to see posts on social media of people doing charitable deeds, using the GoodWill ransomware’s provided “photo frame”.


Whether your company is hit by GoodWill or a more conventional financially-motivated flavour of ransomware, it’s clear that prevention is always better than cure.
Follow the same advice to protect your business
So how can my company protect itself from the BlackCat ransomware?
It’s the same tips as we recommend with other ransomware, including:
- making secure offsite backups.
- running up-to-date security solutions and ensuring that your computers are protected with the latest security patches against vulnerabilities.
- using hard-to-crack unique passwords to protect sensitive data and accounts, as well as enabling multi-factor authentication.
- encrypting sensitive data wherever possible.
- educating and informing staff about the risks and methods used by cybercriminals to launch attacks and steal data.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” Ransomware demands acts of kindness to get your files back” appeared first on TripWire
Source:TripWire – Graham Cluley
