Ransomware Characteristics and Attack Chains – What you Need to Know about Recent Campaigns

Ransomware has been around for decades going back all the way to 1989. Since then it has only magnified in scope and complexity. Now at a time when working remotely is becoming more universal and the world is trying to overcome the Covid-19 pandemic, ransomware has never been more prominent. Ransomware is a type of malware that prevents users from accessing their system or personal files and demands a “ransom payment” in order to regain access. There are two types of campaigns for ransomware “Human-operated” and “Auto-spreading”, this article focusing on the human-operated campaigns.
Human-operated campaigns tend to have common attack patterns which include: Gaining initial access, credential theft, lateral movement and persistence. For many of the human-operated campaigns, typical access comes from RDP brute force, a vulnerable internet-facing system, or weak application settings. Once attackers have gained access they can deploy a plethora of tools to get user credentials. After gaining credentials lateral movement takes place with either deploying a widely known commercial penetration testing suite called Cobalt Strike, changing settings of the WMI (Windows Management Instrument) or abusing management tools with low-level privilege. Finally, attackers want to keep a connection and make it persistent; this is done by creating new accounts, making GPO (Group Policy Object) changes, creating scheduled tasks, manipulating service registration, or by deploying shadow tools.
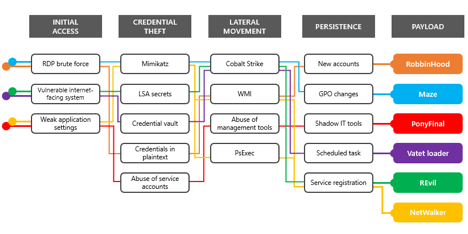
Diving deeper into the campaigns
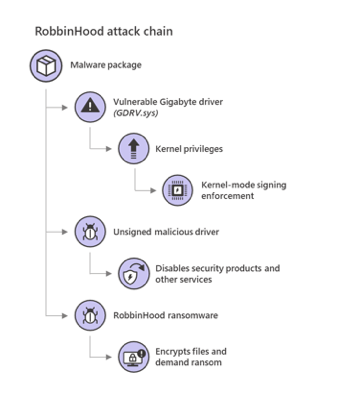
RobbinHood ransomware
RobbinHood ransomware made waves in 2019 when it infected Baltimore and Greenville city networks. Research into CVE-2018-19320 shows the RobbinHood ransomware takes advantage of a vulnerable driver installed on a user’s machine. This low-level driver is primarily used to program and query status on several embedded ICs (integrated circuits) on the user’s hardware, and is exposed to applications through its low-level kernel driver. The driver is installed with a default access permission that allows non-privileged user processes to get HANDLE and issue IOCTL codes to the driver. With this access, attackers can disable code signing and load their own kernel module to gain complete control of the system. Once attackers have infected a user’s system they establish persistence by creating new local or AD user accounts so they can regain access after their tools have been removed. Below is the attack chain.

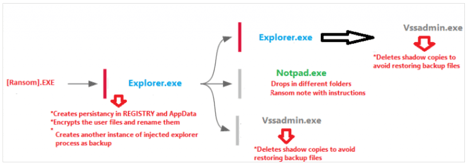
NetWalker ransomware
With the rise of Covid-19, hospitals and healthcare providers have become a target for ransomware. The NetWalker campaign has been infecting hospitals and healthcare organizations by conducting spear phishing campaigns providing information about Covid-19. Attached to the Covid-19 email is a .vbs file and an executable file. NetWalker leverages “compromised networks using misconfigured IIS-based (Internet Information Services) applications to launch Mimikatz and steal credentials, which they can then use to launch PsExec.” To keep the persistency of the attack alive, NetWalker deletes the original executable file from its location and drops the original payload in the users ‘AppDataRoaming’ folder then creates a registry key that will execute the file every time the host performs a startup. Below is the attack chain.

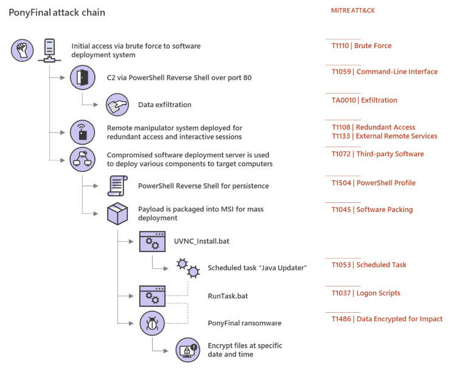
PonyFinal ransomware
PonyFinal ransomware is at the tail end of protracted human-operated ransomware campaigns that are known to stay dormant and wait for the most opportune time to deploy the payload. Like many ransomware campaigns, attackers have been observed using brute force attacks against systems management servers to gain initial access. Attackers then would deploy a .vbs script file to open a PowerShell reverse shell to orchestrate the attacks and begin data exfiltration. With the data stolen from the systems management server, the attackers then target endpoints that already have JRE (Java Runtime Environment) installed which is needed for the ransomware to run. In some cases, the JRE may be deployed by the attacker. Delivery of the payload is the final step which consists of an MSI file containing two batch files – the first file is for creating a scheduled task which then subsequently calls the second batch file for downloading the payload. Below is the attack chain.

Maze ransomware
Maze ransomware has been around for a while now and was one of the first ransomware that was used to sell stolen data. Microsoft explains that “Maze has been delivered via email, but campaign operators have also deployed Maze to networks after gaining access using common vectors, such as RDP brute force. Once inside a network, they perform credential theft, move laterally to access resources and exfiltrate data, and then deploy ransomware.” Microsoft goes on to say that, “After gaining control over a domain admin account through credential theft, campaign operators used Cobalt Strike, PsExec, and a plethora of other tools to deploy various payloads and access data.”
REvil ransomware
REvil ransomware was one of the first campaigns to take advantage of the Pulse VPN vulnerabilities to steal credentials used to access networks. Subsequently, they used CVE-2019-19781 affecting Citrix ADC reportedly used by as many as 80,000 firms. Citrix released a mitigation for the vulnerability on the affected versions of Citrix ADC, but after 3 weeks of the announced flaw, nearly 40,000 unprotected Citrix appliances still did not have the migration enabled. Microsoft explains that REvil attack techniques overlap with many other groups, relying on credential theft tools like Mimikatz once in the network and performing lateral movement and reconnaissance with tools like PsExec.

Vatet loader
Vatet loader campaign is one of the most prolific ransomware campaigns during this time targeting hospitals, aid organizations, insulin providers, medical device manufacturers, and other critical verticals causing dozens of serious infections. Microsoft explains, “To access target networks, the group starts off with a brute force attack on RDP endpoints, and sending emails containing .lnk files that launch malicious PowerShell commands. Once inside a network they steal credentials, including those stored in the Credential Manager Vault, and move laterally until they gain domain admin privileges.”
Other Ransomware families
There are several other ransomware families that are human-operated campaigns which include:
- Paradise: This is a crypto-locking malware that was formerly distributed by email. It is now being used in more sophisticated attacks.
- RagnarLocker: This malware heavily uses RDP and Cobalt Strike with stolen credentials.
- MeduseLocker: Deployed mainly by TickerBot infections.
- LockBit: LockBit is distributed by attackers that use the publicly available penetration testing tool CrackMapExec for lateral movement across compromised networks.
Response actions for active attacks
Keeping an active look at systems and networks and having a proactive approach to hardening security around them is very important. As you have read, ransomware can be catastrophic for organizations and completely hamstring them into submission unless proper fail-safes and alterations to security permissions are implemented.
Investigate affected endpoints and credentials
With credential theft needed for most lateral movement, assume that the credentials were available to attackers and the associated accounts are compromised. Microsoft recommends, “Use of advanced hunting to identify accounts that have logged on to affected endpoints and using the threat analytics report by Microsoft Defender ATP to create hunting queries.”
Address internet-facing weaknesses
Keeping a handle on perimeter systems that may allow attackers to access your network through a misconfigured application is important. A public scanning interface, such as shodan.io can be used to augment your data. Microsoft says the following system risks are considered to be of interest to attackers.
- RDP or Virtual Desktop endpoints without MFA
- Citrix ADC systems affected by CVE-2019-19781
- Pulse Secure VPN systems affected by CVE-2019-11510
- Microsoft SharePoint servers affected by CVE-2019-0604
- Microsoft Exchange servers affected by CVE-2020-0688
- Zoho ManagedEngine systems affected by CVE-2020-10189
Building security hygiene to defend networks
Microsoft recommends the following to help defend networks against human-operated ransomware and start a process of building proper security hygiene.
- Randomize local administrator password using a tool such as LAPS (Local Administrator Password Solution)
- Apply Account Lockout Policy
- Ensure good perimeter security by patching exposed systems. Apply mitigating factors, such as MFA or vendor-supplied mitigation guidance, for vulnerabilities.
- Utilize host firewalls to limit lateral movement such as preventing endpoints from communicating on TCP port 445 for SMB.
- Turn on attack surface reduction rules, these rules can block ransomware activity:
- Use advanced protection against ransomware
- Block process creations originating from PsExec and WMI commands
- Block credential stealing from windows local security authority subsystem.
Summary
With an uptick in human-operated ransomware campaigns creating a strain on SecOps for many healthcare and critical industries sectors, keeping systems and network perimeters secure has never been more important. Maintaining a proactive approach with a security mindset in mitigation for the following ransomware campaigns is key to hardening outer perimeter security.
The post ” Ransomware Characteristics and Attack Chains – What you Need to Know about Recent Campaigns” appeared first on TripWire
Source:TripWire – Matthew Jerzewski
