PLEASE_READ_ME Ransomware Campaign Targeting MySQL Servers

Digital attackers launched a new ransomware campaign dubbed “PLEASE_READ_ME” in an effort to target MySQL servers.
Guardicore first spotted the attack back in January 2020. After that, it witnessed a total of 92 attacks emanate from 11 IP addresses, with most based in Ireland and the United Kingdom at the time of analysis.
The security firm found that each attack began the same way. As quoted in its research:
The attack starts with a password brute-force on the MySQL service. Once successful, the attacker runs a sequence of queries in the database, gathering data on existing tables and users. By the end of execution, the victim’s data is gone – it’s archived in a zipped file which is sent to the attackers’ servers and then deleted from the database. A ransom note is left in a table named WARNING, demanding a ransom payment of up to 0.08 BTC.
Over the course of its analysis, Guardicore picked out two variants of the campaign. The first lasted from January to November 2020 and consisted of 63 attacks. Each of those instances involved the delivery of a ransom note including a bitcoin wallet address, an email address for technical support and a 10-day window for the victim to pay.
Those behind PLEASE_READ_ME had collected 24,906 USD as a result of this variant at the time of Guardicore’s analysis.
The second variant dispensed with email communications and a bitcoin wallet address. Instead, it directed recipients to visit a .ONION site. The site’s dashboard provided victims with the ability to submit their infection token in order to pay their ransom. It also gave visitors the ability to buy 250k different databases from 83k MySQL servers belonging to victims who didn’t pay.
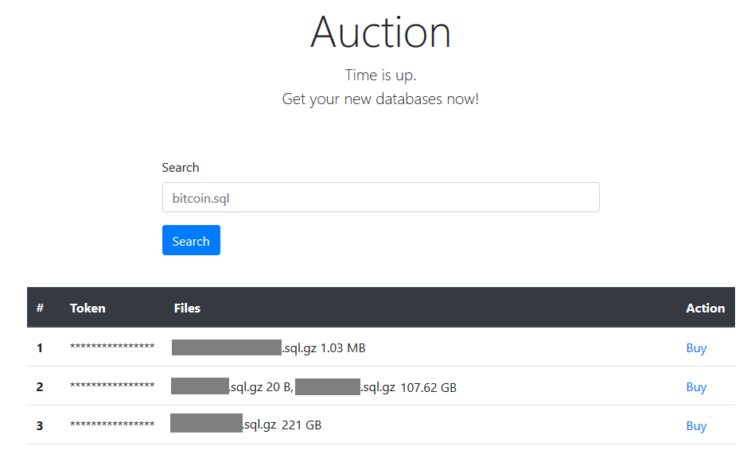
That variant, which started on October 3 and lasted through November, consisted of 29 attack instances involving seven IP addresses.
News of this attack highlights the need for organizations to defend themselves against ransomware. They can do so by following these steps in order to prevent a ransomware infection from occurring in the first place.
The post ” PLEASE_READ_ME Ransomware Campaign Targeting MySQL Servers” appeared first on TripWire
Source:TripWire – David Bisson
