Nvidia’s Stolen Code-Signing Certs Used to Sign Malware

Nvidia certificates are being used to sign malware, enabling malicious programs to pose as legitimate and slide past security safeguards on Windows machines.
Two of NVIDIA’s code-signing certificates were part of the Feb. 23 Lapsus$ Group ransomware attack the company suffered – certificates that are now being used to sign malware so malicious programs can slide past security safeguards on Windows machines.
The Feb. 23 attack saw 1TB of data bleed from the graphics processing units maker: a haul that included data on hardware schematics, firmware, drivers, email accounts and password hashes for more than 71,000 employees, and more.
Security researchers noted last week that binaries that hadn’t been developed by NVIDIA, but which had been signed with its stolen certificate to come off like legitimate NVIDIA programs, had appeared in the malware sample database VirusTotal.
The signed binaries were detected as Mimikatz – a tool for lateral movement that allows attackers to enumerate and view the credentials stored on the system – and for other malware and hacking tools, including Cobalt Strike beacons, backdoors and remote access trojans (RATs) (including a Quasar RAT [VirusTotal] and a Windows driver [VirusTotal]).
Gist that contains @virustotal Enterprise search queries to find samples signed with the leaked NVIDIA certificates#NvidiaLeaks #LAPSUS
based on my and @GossiTheDog‘s work
https://t.co/JxnbrLSjVz pic.twitter.com/KYRKdYcF8R— Florian Roth ⚡️ (@cyb3rops) March 5, 2022
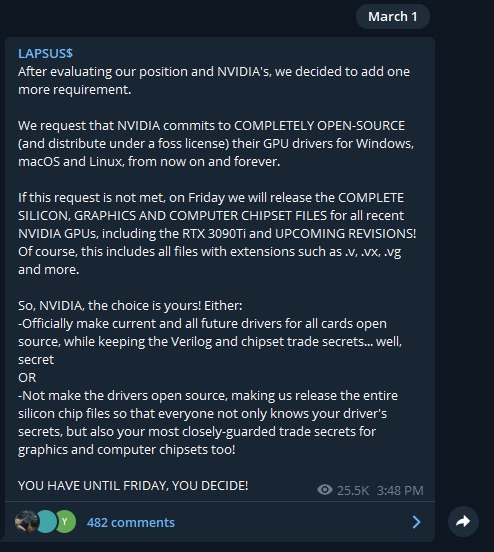
Last Tuesday, March 1, Lapsus$ demanded that NVIDIA open-source its drivers, lest Lapsus$ do it itself.
Three days later, Lapsus$ released what was purportedly a massive dump of proprietary source code stolen from Samsung, vx-underground reported.
LAPSUS$ extortion group have successfully breached both NVIDIA & Samsung.
-March 1st: They demand NVIDIA open-source its drivers, or else they will
-March 4th: LAPSUS$ released Samsung proprietary source code.See attached images for more details directly from LAPSUS$ pic.twitter.com/U3VD7R2KRl
— vx-underground (@vxunderground) March 4, 2022
On Feb. 27, Lapsus$ claimed that it had been in NVIDIA’s systems for a week, that the gang isn’t state-sponsored and that it’s “not into politics AT ALL” – a clarification that’s apparently important for cybercrooks now that the Russia/Ukraine cyber war zone is burning at fever pitch.
Doxxed Emails, Password Hashes & More
Last Wednesday, March 2, the compromised-email notice site Have I Been Pwned put up an alert regarding 71,335 NVIDIA employees’ emails and NTLM password hashes having been leaked on Feb. 23, “many of which were subsequently cracked and circulated within the hacking community.”
As has been noted, at least on the face of it, that number of 71,000 compromised employee accounts – a number that the graphics processing units maker hasn’t confirmed or denied – doesn’t make sense. In its most recent quarterly report (PDF), NVIDIA only listed a workforce of 18,975.
But, given that the Telegraph’s initial report cited an insider who said that the intrusion “completely compromised” the company’s internal systems, it could be that the stolen data included former employees.
Lapsus$ released a portion of the highly confidential stolen data, including source codes, GPU drivers and documentation on NVIDIA’s fast logic controller product, also known as Falcon and Lite Hash Rate, or LHR GPU.
Lapsus$ demanded $1 million and a percentage of an unspecified fee from NVIDIA for the Lite Hash Rate bypass.
Expired But Still Recognized Certs
Both of the stolen Nvidia code-signing certificates are expired, but they’re still recognized by Windows, which allow a driver signed with the certificates to be loaded in the operating system, Bleeping Computer noted.
According to security researchers Kevin Beaumont and Will Dormann, the stolen certificates use these serial numbers:
- 43BB437D609866286DD839E1D00309F5
- 14781bc862e8dc503a559346f5dcc518
How to Block the Signed Malware
David Weston, director of enterprise and OS security at Microsoft, tweeted on Thursday that admins can keep Windows from loading known, vulnerable drivers by configuring Windows Defender Application Control policies to control which of Nvidia’s drivers can be loaded.
That should, in fact, be admins’ first choice, he wrote.
WDAC policies work on both 10-11 with no hardware requirements down to the home SKU despite some FUD misinformation i have seen so it should be your first choice. Create a policy with the Wizard and then add a deny rule or allow specific versions of Nvidia if you need
— David Weston (DWIZZZLE) (@dwizzzleMSFT) March 3, 2022
David Weston, Microsoft Vice President, OS Security and Enterprise, went on to tweet the attributes to be blocked or allowed.
These are all the attributes you can block or allow on: pic.twitter.com/3BV3QoMuMX
— David Weston (DWIZZZLE) (@dwizzzleMSFT) March 3, 2022
Who Is Lapsus$ Group?
Lapsus$ Group emerged last year. It’s probably best known for its December attack on the Brazil Ministry of Health that took down several online entities, successfully wiping out information on citizens’ COVID-19 vaccination data as well as disrupting the system that issues digital vaccination certificates.
As well, in January 2022, Lapsus$ also crippled the Portuguese media giant Impresa.
Register Today for Log4j Exploit: Lessons Learned and Risk Reduction Best Practices – a LIVE Threatpost event sked for Thurs., March 10 at 2PM ET. Join Sonatype code expert Justin Young as he helps you sharpen code-hunting skills to reduce attacker dwell time. Learn why Log4j is still dangerous and how SBOMs fit into software supply-chain security. Register Now for this one-time FREE event, Sponsored by Sonatype.


The post “Nvidia’s Stolen Code-Signing Certs Used to Sign Malware” appeared first on Threat Post
Source:Threat Post – Lisa Vaas