NitroHack Modifies Windows Discord Client into Infostealing Trojan

Security researchers discovered a new malware threat called “NitroHack” that modifies the Discord client for Windows into an infostealing trojan.
MalwareHunterTeam observed malicious actors abusing DM’s from infected Discord users as a distribution vector. Specifically, they leveraged those accounts to inform a victim’s friends that they could obtain free access to the premium Discord Nitro service by downloading a file.
By complying, a user inadvertently infected themselves with NitroHack. This malware appended malicious code to the “%AppData%\Discord�.0.306modulesdiscord_voiceindex.js” file as well as attempted to change the same file in both the iscord Canary and Discord Public Test Build clients.
Bleeping Computer explained that the malware acted in this matter to establish persistence and to steal a user’s account tokens:
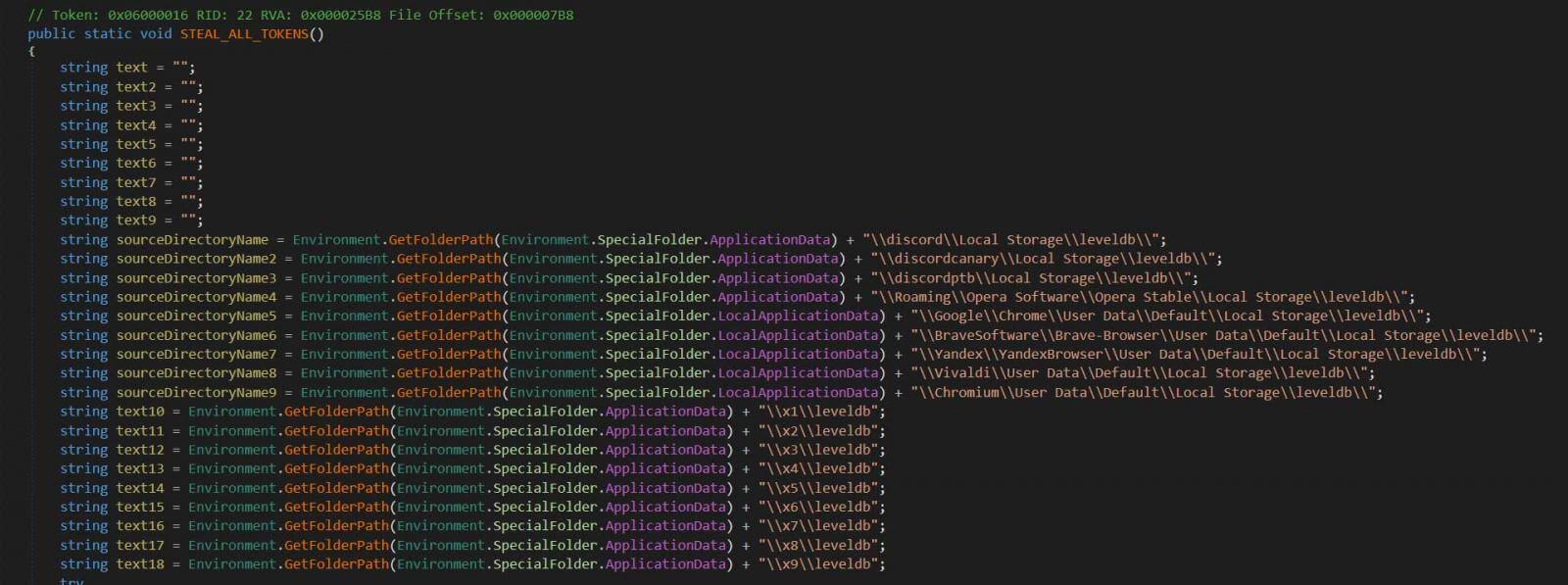
To steal these tokens, NitroHack will copy browser databases for Chrome, Discord, Opera, Brave, Yandex Browser, Vivaldi, and Chromium and scan them for Discord tokens. When done, the list of found tokens will be posted to a Discord channel under the attacker’s control.
NitroHack didn’t reserve all of its malicious activity to just users of the Windows Discord client, however. The malware also attempted to connect to the “https://discordap[.]com/api/v6/users/@me/billing/payment-source” URL.” It did this for the purpose of stealing web client users’ payment card information.
It’s at that point when NitroHack stole a list of a victim’s contacts. It then sent them a link disguised as a Nitro Hack service link.
Users can verify whether they’ve suffered a NitroHack infection by opening the “%AppData%\Discord�.0.306modulesdiscord_voiceindex.js” file with Notepad. The normal file should simply contain “module.exports = VoiceEngine;” Anything else could be indicative of a malware infection.
News of this newest malware threat comes less than a month after researchers found that an updated version of AnarchyGrabber had stolen victims’ plaintext passwords and infected victims’ friends on Discord.
The post ” NitroHack Modifies Windows Discord Client into Infostealing Trojan” appeared first on TripWire
Source:TripWire – David Bisson
