JavaScript Used by Phishing Page to Steal Magento Credentials

Digital attackers created a Magento phishing page that used JavaScript to exfiltrate the login credentials of its victims.
Sucuri came across a compromised website using the filename “wp-order.php” during an investigation.
This phishing page hosted what appeared to be a legitimate Magento 1.x login portal at the time of discovery. In support of this ruse, it loaded its CSS code and images from the malicious domain orderline[.]club.
In its analysis of the website, Sucuri found that the Magento phishing page was a bit unconventional in the method by which it exfiltrated its victims’ stolen data. As quoted in its research:
… [T]he phishing page uses a technique that doesn’t require a separate PHP file or rely on PHP functions to send out an email to the attacker, which is what we often find for exfiltration on phishing pages like this.
Instead, this phishing attack uses a JavaScript EventListener method (addEventListener) with the change event for the username and login (password) fields…
The phishing page specifically sent out a GET request to orderline[.]club/fget.php in order to pass its victims’ data to the attackers.
Provided below is an illustration of this delivery mechanism at work and its application of base64 encoding to the exfiltrated information.
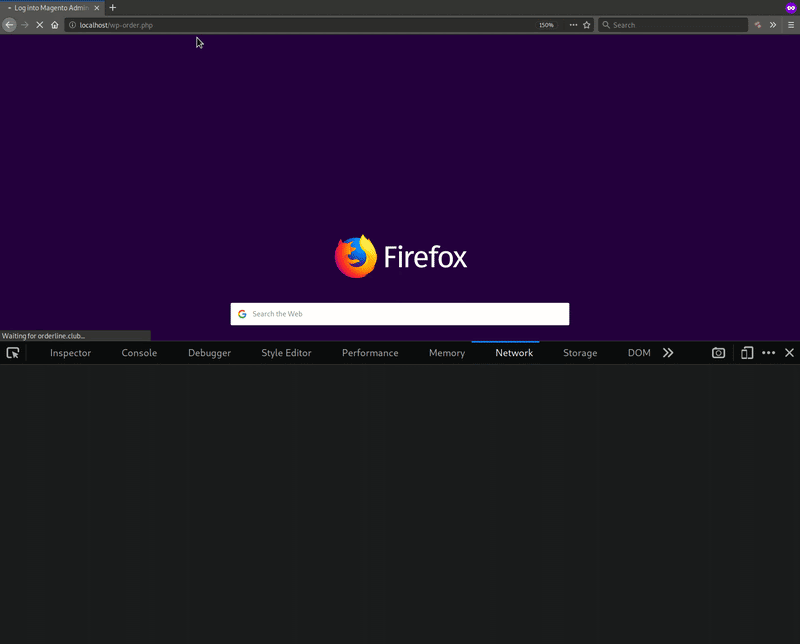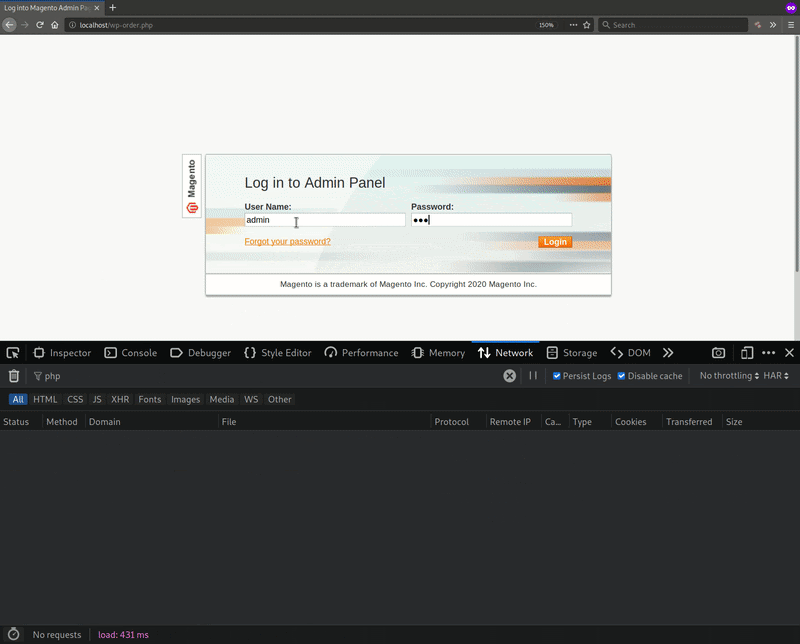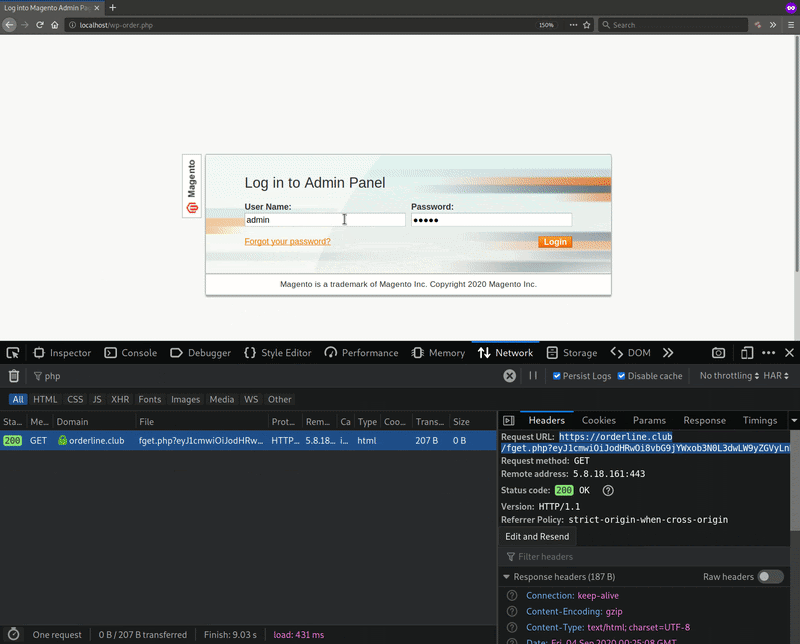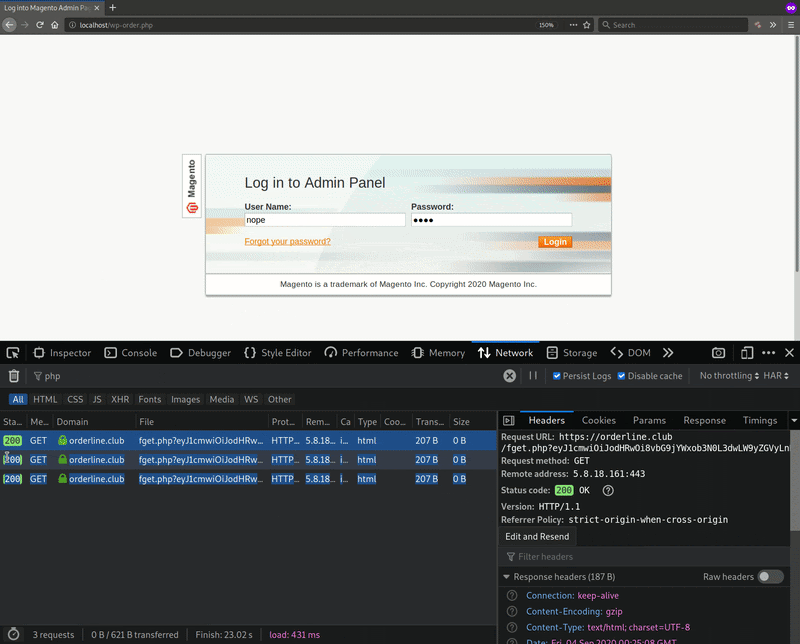
Over the course of its analysis, Sucuri found evidence that the phishing page was still in development. Its researchers concluded that they the security community could therefore see additional phishing campaigns incorporate this type of JavaScript-based exfiltration technique in the future.
News of this attack highlights the need for organizations to defend themselves against phishing attacks. They can do so by educating their employees about some of the most common types of phishing attacks that are in circulation today. This resource is a good place to start.
The post ” JavaScript Used by Phishing Page to Steal Magento Credentials” appeared first on TripWire
Source:TripWire – David Bisson
