How Social Norms Can Be Exploited by Scammers on Social Media

Social media platforms are excellent hunting grounds for scammers. This is where we connect with our friends or people who we have something in common with. This is precisely what scammers exploit—our connections and the trust that is afforded between friends or acquaintances.
From an early age, we are taught to be kind and compassionate as well as to help others, especially people we know such as friends and family. In turn, they will help us if we ever need it. This is a socially desired behavior.
Most people think and operate in this way. But this is also how we can be exploited by scammers. Look at the following real-life case study of a common Facebook scam that targets the friends of a victim’s compromised account.
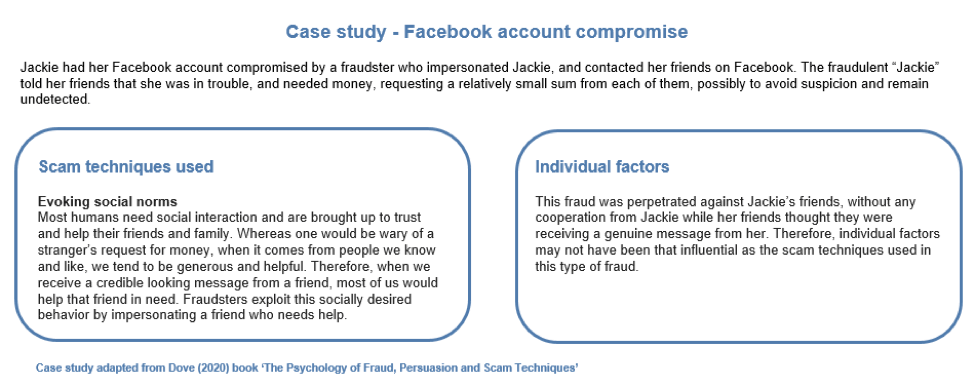
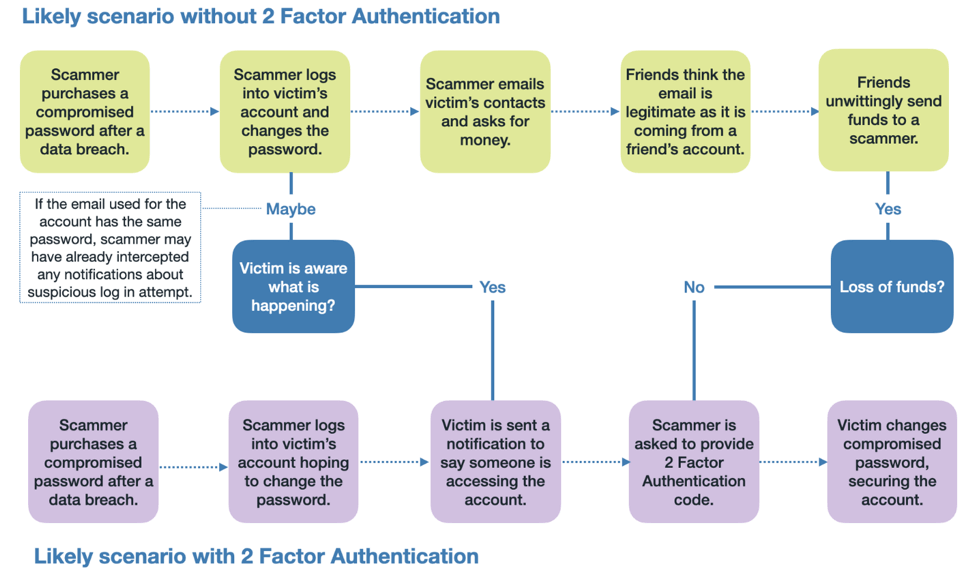
Although this scam was perpetrated against Jackie’s Facebook friends, there is still something Jackie could have done to prevent this scam. While we cannot control how social media companies protect our data from cybercriminals, we can still do something to make it hard for cybercriminals to fraudulently use our data. Make sure you use strong, unique passwords for all of your logins with the help of a good password manager. This measure is important because if a scammer gets hold of your account log in details and you use the same password on your social media account that is used on our email, the intruder can easily log in to both accounts. This means that any login alerts sent by a social media account will be intercepted. Using the same password for multiple accounts also means that the scammer may compromise your other accounts. The fraudulent login process would also be interrupted if there is a two-factor authentication method enabled on your accounts.

If you are a ‘friend’ who has just received a strange message from one of your friends on a social media platform, you would be wise to double-check the information given. Call the person who has sent you the request on their phone to verify the information. If you are unable to do so, you can try getting verification some other way. For example, you can try asking a question that only the person would know how to answer. Or try asking a trick question – something you know is not an accurate fact about the friend in question – to see how they respond. Then watch for vague responses or avoidance to answer the question. This can often raise red flags that something is not right.
It is also important to understand that many scams exploit our kindness and good nature. There are plenty of fundraising campaigns on social media, and many are not genuine. It is always recommended to get into the habit of checking facts before transferring funds.
Here are some other tips on how to stay safe on social media.
More articles that may interest you:
Phishing attacks often target small businesses – here’s what to watch for
Protecting a New Vulnerable Population on the Internet
Protecting the New Most Vulnerable Population – The Grandparent Scam
Protecting the New Most Vulnerable Population – Subscription Scams
The post ” How Social Norms Can Be Exploited by Scammers on Social Media” appeared first on TripWire
Source:TripWire – Martina Dove
