How Cybersecurity Leaders Can Understand the Value of Their Organization’s Security Solutions

“Gartner projections show the growth in cybersecurity spending is slowing. Cybersecurity grew at 12% (CAGR) in 2018, and it is projected to decline to only 7% (CAGR) by 2023. Gartner clients are also reporting that after years of quarterly reporting on cybersecurity to their boards, that boards are now pushing back and asking for improved data and understanding of what they have achieved after years of such heavy investment (see “IT Key Metrics Data 2020: IT Security Measures — Analysis”).
Following the Equifax hack in 2017, the CEO stepped down and made very clear that the hack was a fundamental reason for doing so. The final U.S. House of Representatives subcommittee report issued in December 2018 indicated “Equifax’s CEO did not prioritize cybersecurity” (see “8 Reasons More CEOs Will Be Fired Over Cybersecurity Incidents”).
– The Gartner Group
The Problem
Information Security leaders have to demonstrate the value and purpose for each solution that’s purchased and prove the solution that was chosen is doing the job it was procured to do. Executives are therefore requiring Information Security leaders to prove the value of the solutions in ways they understand. They need to see the value not in security metrics but in dollars and cents.
While they understand that the Secure Email Gateway is blocking thousands of malware-laden emails every month, executives do not understand that one successful phishing email could cost the company millions of dollars. A formula that shows the probability of that happening and the lowered risk using the solution against cost of the solution proves value in a way that executives can understand.
Choices
The total number of cybersecurity companies, covering some 16 security domains, is around 3,500 and growing every year.
This creates an incredible selection of vendors to choose from. Logic might point to a solution from every domain to cover every aspect of cybersecurity within an organization. Some organizations’ budgets provide for this comprehensive approach. Others have to be innovative and look to automation in order to keep costs down.
Choosing the right solution for the organization requires a Security Leader to understand the business, the risk environment and the current solutions on the market. With the constant increase in threats and complexity of attacks, the cybersecurity market for solutions continues to grow exponentially. It’s one thing to understand the threats that are current and emerging, while it’s another matter entirely to understand the solutions available to help mitigate those threats cost-effectively and efficiently.
Justification
Information security leaders must prioritize risk and the mitigating technology associated with it.
The justification for solutions must be presented in terms of potential risk versus investment. Executive teams are aware of the cost of cybersecurity investments but not the cost of risk. That is where ROI as well as calculations of Annual Risk Occurrence and Annual Loss Expectancy come in.
Some organizations conduct annual risk assessments. These assessments are good for identifying areas that need risk-mitigating solutions. But they do not offer the ROI of the solutions needed to mitigate the risk, nor do they incorporate current industry standards for costs related to a security eventincident or data breach, which have their own separate related costs.
Formulas
Many Information Security Leaders struggle with providing mathematical or statistical data to support their decisions, or recommendations around cybersecurity solutions. Fortunately, there are formulas that can provide mathematical support to proving ROI of cybersecurity solutions. They can explain the value of investment in cybersecurity in dollars and cents to a Board or Senior Leadership teams in language that they can understand and comprehend.
One formula created by the Center for Information Security is easy to use and understand.
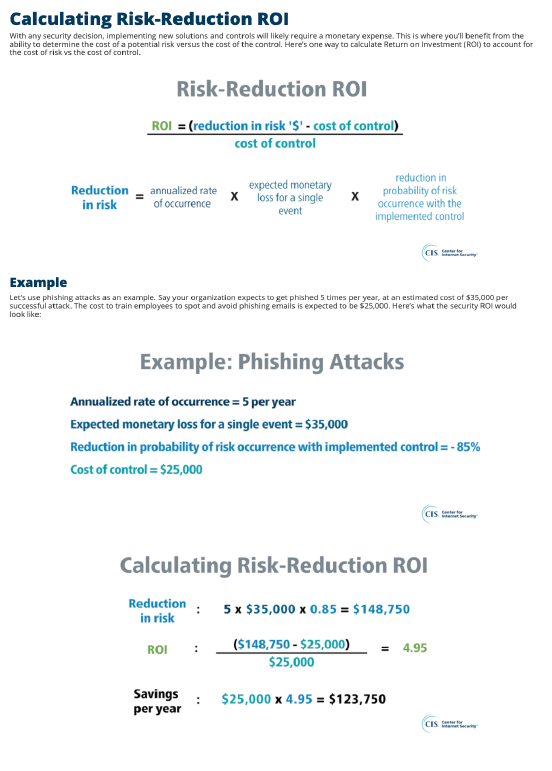
Using Cost values and some solution metrics, a dollar value can be provided for each “Savings per year.” Obviously, these are not savings that the company can apply to their budget. But they are savings in terms of dollars not spent on a data breach or security incident.
In Summary
As cybersecurity investments continue to drop, breaches continue to evolve and more complex threats continue to emerge, the need becomes even more apparent for better methods that are capable of proving the value of solutions that Cybersecurity leaders are recommending. The process of tying the asset cost to risk-reduction ROI will evolve and develop into an industry standard at some point. It will also most likely become part of some of the high-level certification courses in the future.
Investments will continue to drop until executives understand why they are investing in cybersecurity solutions and what the value of those solutions are. Specifically, they need to understand how those solutions protect the bottom line and the company’s brand. After all, cybersecurity solutions are not just about preventing phishing emails or ransomware. They can extend into the Dark Web to provide protection of the company brand and in some cases fraud detection.
Adept Information Security leaders understand these solutions and their value. It’s up to them to show that value with knowledge of the threats as well as an understanding of the cybersecurity market, the cost to the business and most importantly the savings those solutions provide are a plus for the organization as a whole.


Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” How Cybersecurity Leaders Can Understand the Value of Their Organization’s Security Solutions” appeared first on TripWire
