Hackers disguise malware attack as new details on Donald Trump’s COVID-19 illness

The confirmation that US President Donald Trump has been infected by the Coronavirus, and had to spend time this weekend in hospital, has – understandably – made headlines around the world.
And there are plenty of people, on both sides of the political divide, who are interested in learning more about his health status.
It’s no surprise, therefore, to discover that cybercriminals are exploiting that interest with the intention of infecting users’ computers.
Hot on the heels of the developing coverage of Donald Trump’s hospitalisation and return to the White House, hackers have spammed out emails designed to trick the unwary into clicking on a malicious link by offering more details related to the US President’s health.
Security researchers at Proofpoint, who last week warned of a malware campaign claiming to come from the Democratic National Committee, posted details on Twitter of the new and active malicious attack they had seen targeting hundreds of US and Canadian organisations.

The emails, which have been seen using subject lines such as “Recent materials pertaining to the president’s illness”, “Newest information about the president’s condition”, and “Newest info pertaining to President’s illness”.
The body of a typical malicious email sent out in the campaign reads as follows:
What we really know and even what we don’t about Trump’s COVID health problems.
Insider information about Trump’s][health condition, please remember to use the code because the record is encrypted: 123
[LINK]
As Bleeping Computer reports, clicking on the link does indeed take curious users to a Google Doc.

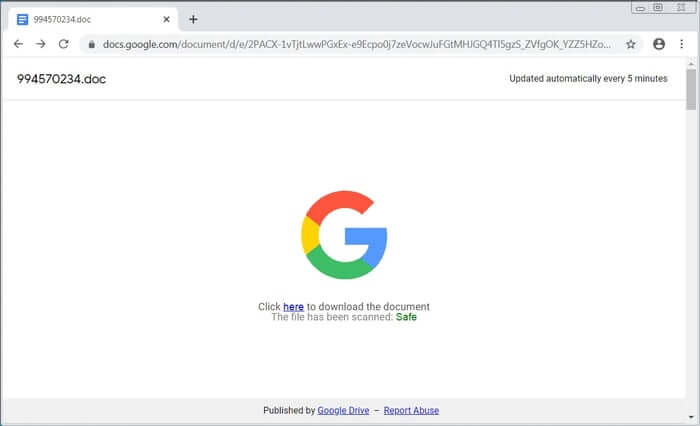
However, the Google Doc itself contains a link to a malicious webpage, where the malware can be downloaded from. To reassure targeted users, the online document deceptively gives the impression that Google has scanned the file residing at the link and deemed it safe.
In many ways the attack is quite cunning. The email uses an enticing lure (secret information about Donald Trump’s COVID-19 infection), and links to a legitimate domain (docs.google.com) that most users would instinctively trust, and that email and web security solutions are unlikely to block.
However, the document posted there links to somewhere malicious – and users hungry to gobble up the latest information about a hot news story, and maybe eager to share the details with their friends, might well click without thinking.
And doing so, of course, can be disastrous.
Because lurking at the end of the link is BazarLoader, a backdoor Trojan horse connected to the same hackers who develop the TrickBot malware.
If BazarLoader (sometimes called BazaLoader) infects your PC then hackers have an opportunity to strike, installing more malicious code onto your computer, stealing information, and perhaps spreading across the rest of your organisation’s network. If that access was exploited to exfiltrate data or install ransomware, the costs could be significant.
The gang behind BazarLoader have used similar tactics in the past. For instance, in April it was reported that they were actively attempting to infect companies using a wide range of email disguises including customer complaints, COVID-19-themed payroll reports, and employee termination lists – all with links to documents on Google Docs.
From the social engineering point of view, you can easily imagine that such attacks would succeed on occasion – so it would be no surprise to see the gang try similar attacks again and again as the news agenda changes over the coming weeks and months.
So maybe you’re wiser not to get your news tips from unsolicited emails, and instead seek out election-related news on the websites and TV stations of legitimate news outlets instead.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” Hackers disguise malware attack as new details on Donald Trump’s COVID-19 illness” appeared first on TripWire
Source:TripWire – Graham Cluley
