Global Phishing Campaign Sets Sights on COVID-19 Cold Chain

A global phishing campaign targeted organizations associated with the Coronavirus 2019 (COVID-19) cold chain.
Discovered by IBM Security X-Force, the operation began in September 2020 by targeting multiple entities that support the Cold Chain Equipment Optimization Platform (CCEOP).
A program created by Gavi, The Vaccine Alliance, CCEOP aims to cultivate an agile medical response to outbreaks of infectious diseases like COVID-19. It does this in part by working to strengthen the “cold chain,” or a supply chain that preserves vaccines by delivering doses in temperature-controlled environments.
The attack emails in this phishing campaign impersonated an employee at Haier Biomedical, a Chinese company working as a CCEOP supplier.
Posing as Requests For Quotations (RFQs) in association with CCEOP, the emails instructed recipients to click on a malicious HTML attachment that opened locally.
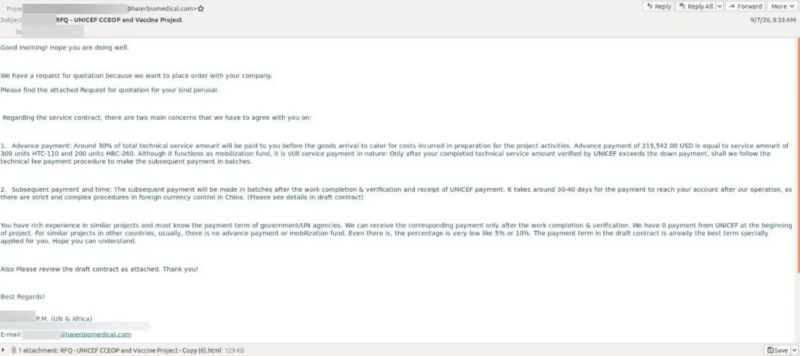
The attachment stole a victim’s credentials and enabled the attackers to gain insight into an affected organization’s plans to help distribute a vaccine as part of the COVID-19 cold chain.
There were additional opportunities for malicious activity, as well. As IBM Security X-Force explained in its research:
… [B]eyond critical information pertaining to the COVID-19 vaccine, the adversary’s access could extend deeper into victim environments. Moving laterally through networks and remaining there in stealth would allow them to conduct cyber espionage and collect additional confidential information from the victim environments for future operations.
At the time of discovery, IBM Security X-Force found that the campaign had targeted the European Commission’s Directorate-General for Taxation and Customs Union along with other COVID-19 cold chain organizations working in the manufacturing, energy and technology sectors. These companies based their headquarters in Germany South Korea, Taiwan and elsewhere.
Attribution of those responsible for the attack was unknown at the time of writing. Even so, IBM Security X-Force noted that a nation state might be behind the campaign.
This operation highlights the need for organizations to defend themselves against phishing attacks. They can do this by pairing their use of threat intelligence and implementation of MFA with ongoing security awareness education around some of the most common types of phishing attacks that are circulating in the wild today.
The post ” Global Phishing Campaign Sets Sights on COVID-19 Cold Chain” appeared first on TripWire
Source:TripWire – David Bisson
