Fulfilling Security Requirements for the Transportation Sector

Protecting our critical infrastructure against the threat of ransomware remains a top priority for both the private sector and the federal government. In fact, a recent survey from Tripwire found that security professionals in both sectors still identify ransomware as a top security concern. More than half (53%) of respondents in that study said they were most concerned about ransomware, for instance. This was followed by vulnerability exploits, phishing, and social engineering at 35%, 34%, and 24%, respectively.
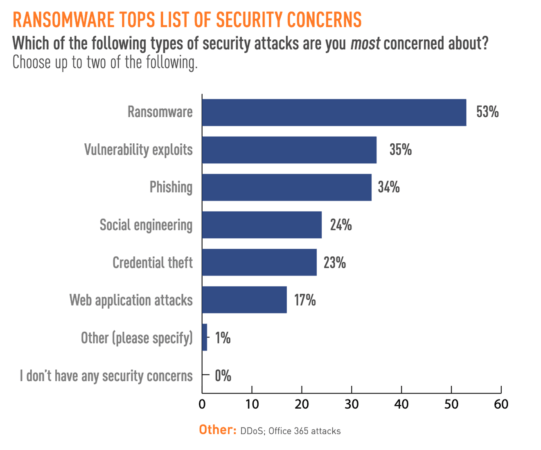
These findings aren’t a surprise in light of some of the ransomware attacks that made headlines in 2021. In particular, an incident involving a gas pipeline company back in May demonstrated the extent to which ransomware can disrupt normal life by targeting critical infrastructure systems. This explains why the Biden Administration has taken steps to modernize the nation’s cybersecurity, pressure Russian President Vladimir Putin to crack down on ransomware gangs operating out of Russia, and sanction cryptocurrency exchanges that have helped to facilitate ransomware payments.
What’s in the Transportation Security Agency’s New Security Requirements?
After updating their approach to protecting the pipeline sector, the Transportation Security Agency (TSA) has introduced an initial set of security requirements to improve cybersecurity across the transportation industry “in response to ongoing threats to surface transportation systems and associated infrastructure.” As such, it is part of a larger effort to secure U.S. critical infrastructure against ransomware and other digital threats.
Via the new security directives, the TSA requests immediate action from higher-risk freight railroads, passenger rail, and rail transit to protect transportation security. To meet the requirements, owners and operators must designate a cybersecurity coordinator, report cybersecurity incidents to CISA within 24 hours, develop and implement a cybersecurity incident response plan to reduce the risk of an operational disruption, as well as complete a cybersecurity vulnerability assessment to identify potential gaps or vulnerabilities in their systems. TSA also released guidance for lower-risk surface transportation owners and operators (i.e., Greyhound or charter bus systems) to encourage voluntary adoption of the same digital security requirements.
How Tripwire Can Help Organizations Fulfill Those Requirements?
Designating a cybersecurity coordinator
As IT and OT environments continue to converge, it’s essential to approach security from a wholistic standpoint – one that allows for full visibility from industrial devices to the cloud. When selecting a cybersecurity coordinator (often a CISO), it’s imperative that the individual has access to the business units, geographies, and technology that may be impacted by a cyber event. Because of this wide range of responsibilities, your organization may even opt to select more than one coordinator, taking an “office of the CISO” approach. From there, Tripwire solutions can help the designated coordinator gain visibility into what, when, and where there has been impacted due to a cybersecurity event.
24-hour notification
Tripwire can monitor continuously both in the IT and OT environments against policies, changes, or malicious activity. With Tripwire’s continuous 24/7 monitoring, the cybersecurity coordinator can easily respond back to the TSA with updates on potential intrusion to both the IT and OT environment.
Incident Response
When it comes to developing and implementing an incident response plan, a crisis table top exercise is often the best approach to identify strengths and weaknesses in overall cybersecurity posture. Once specific needs are identified, an organization can more clearly understand the tools needed to reach to reach their security goals, whether that means introducing new software or a managed services partner.
Completing a vulnerability assessment
Transportation owners and operators will require comprehensive visibility into their Industrial Control Systems (ICS) along with an accurate inventory of assets to conduct a thorough vulnerability assesment. Tripwire can help with this identification process by discovering and profiling all assets on the network. Such visibility puts organizations in a position to set up immediate security alerts for quick resolution of potential issues, monitor those assets and the industrial network in general for potential problems, as well as avoid plant disruptions by hardening systems and detecting misconfigured systems.
Will Transportation Owners and Operators Comply?
We know that high-risk transportation owners and operators are required to make these changes, but will lower-risk organizations responsible for surface transportation do the same? Based on the previously mentioned Tripwire survey, it’s likely that yes, they will. Both the private and public sector have indicated that they are hungry for direction from the federal government, and most have chosen to adopt NIST guidelines regardless of whether their industry requires them to.
The post ” Fulfilling Security Requirements for the Transportation Sector” appeared first on TripWire
Source:TripWire – Ben Jackman
