Federal agencies given five days to find hacked Exchange servers

CISA, the US Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency, has told federal agencies that they have until 12:00pm EDT on Monday April 5 to scan their networks for evidence of intrusion by malicious actors, and report back the results.
CISA is ordering agencies with on-premises Microsoft Exchange servers to urgently conduct the scans following widespread exploitation of vulnerabilities, in fear that some compromises may have remained undetected.
In an updated directive, CISA has directed federal departments and agencies to download and run the latest version of Microsoft’s scanning tool (known as MSERT).
Agencies have also been told that every week, for four weeks after the first scan, the latest version of MSERT should be downloaded and run again, and any findings that indicate compromise must be reported to CISA.
Because a full scan with MSERT can take several hours and be a drag on server resources, agencies are advised to run the tool during off-peak hours.
In addition, and by the same April 5 deadline, agencies are being told to download and run Microsoft’s Test-ProxyLogon.ps1 script. The script analyses Exchange and IIS logs, indicating potential attacker activity.
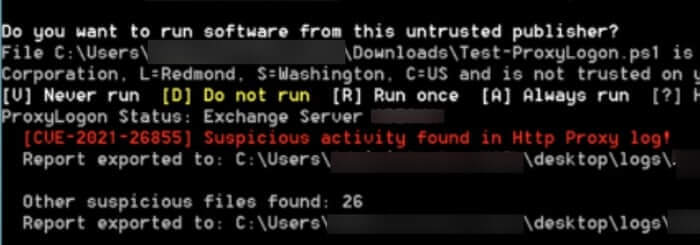
Again, CISA is requesting that reports from the script be shared with them.
Lastly, CISA is calling upon all agencies to harden the defences of their on-premises Microsoft Exchange servers by 12:00pm EDT on Monday, June 28 2021. This includes provisioning firewalls, installing security updates within 48 hours of release, using only software that is still officially supported by a vendor, installing anti-virus software on Exchange servers and keeping it current, capturing and storing logs, and reviewing users’ permissions and roles.
CISA says it has identified that some federal agencies are still operating Microsoft Exchange servers that require additional hardening.
Of course, if all this advice makes good security sense for federal agencies and departments then it’s hard to argue that it doesn’t also make sense for private sector companies and other organisations.
Every organisation at risk should be considering taking similar steps to ensure that they too have not been compromised by the attacks against Microsoft Exchange Server.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” Federal agencies given five days to find hacked Exchange servers” appeared first on TripWire
Source:TripWire – Graham Cluley
