ENISA Releases Guidelines for Cloud Security for Healthcare Services

The healthcare sector is undergoing digitalization and adopts new technologies to improve patient care, offer new services for remote patients and reach operational excellence. The integration of new technologies in the complex healthcare IT infrastructure creates new challenges regarding data protection and cybersecurity.
On the one hand, the COVID-19 pandemic has been a driver for increased cyber-attacks on healthcare organizations including phishing attacks that aim to collect user credentials as well as ransomware attacks that seek to encrypt the data of hospitals.
On the other hand, the pandemic has helped to stress the need for remote healthcare services. Cloud platforms have provided the elasticity and fast access required for the deployment of these services. Organizations subsequently deployed cloud solutions to cover ERP systems along with health information systems like electronic health records, data analytics, medical devices and telemedicine.
To help IT professionals in healthcare security to establish and maintain cloud security while selecting and deploying appropriate technical and organizational measures, ENISA issued a study that aims to provide cloud security practices for the healthcare sector.
Legislative background
According to the European Union NIS Directive, hospitals are defined as Operators of Essential Services (OES), while cloud providers are Digital Service Providers (DSP). Therefore, both hospitals and cloud vendors must comply with the NIS Directive security requirements when contracting with cloud services.
At the same time, the GDPR defines medical data as a “special category” of personal data, which is sensitive by nature and imposes a higher standard of protection for their processing. Healthcare organizations as data controllers that are processing medical data must implement appropriate technical and administration measures to ensure the security of systems, services and data. Further, cloud providers are considered data processors under GDPR as they are acting on behalf of the data controllers; hence, they have obligations as data controllers.
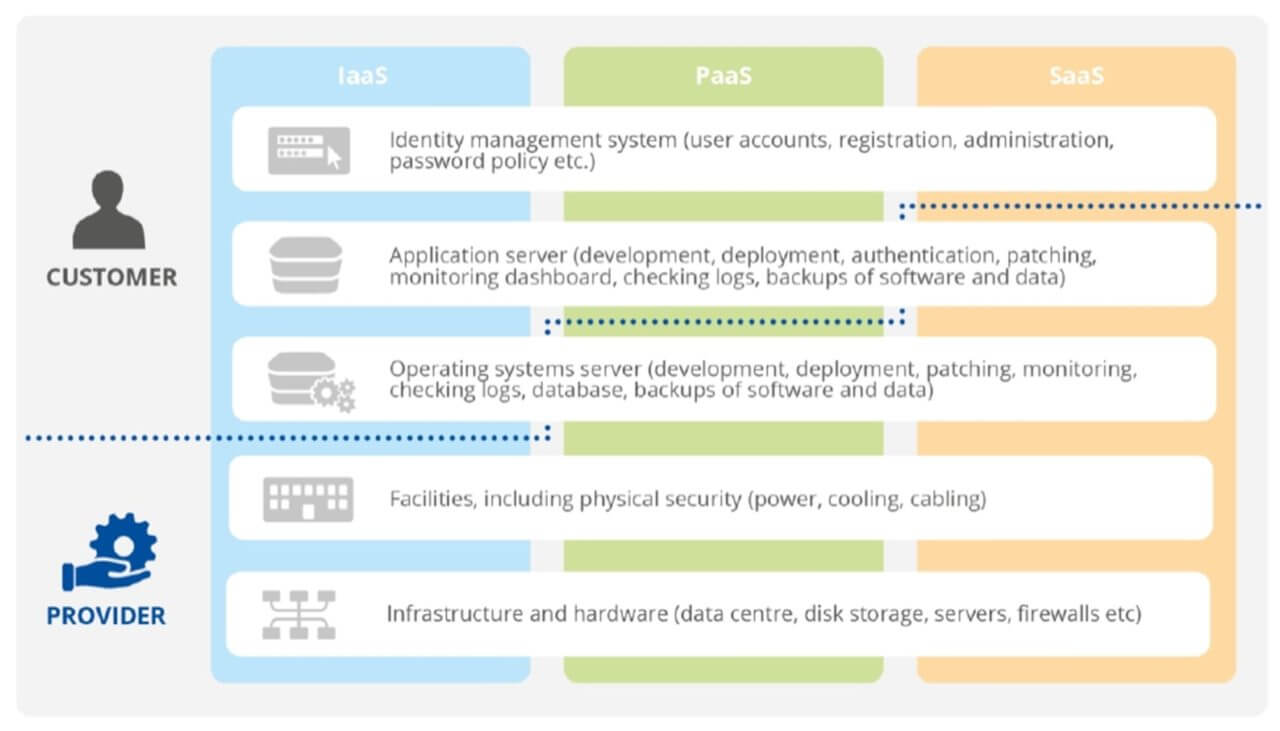
The report reminds healthcare organizations migrating to the cloud that the Shared Responsibility Model applies, that is, cloud customers and cloud providers have certain security requirements in the cloud (the customers) and of the cloud (the providers).
While migrating to the cloud, healthcare organizations are facing security and data protection challenges. The authors of the ENISA report interviewed healthcare professionals in Europe to explore those obstacles. Those respondents identified the following cloud security and data privacy challenges.
Cloud security challenges
Lack of trust: Stakeholders in the healthcare sector such as patients, physicians, and medical staff indicated a lack of trust of cloud solutions. To combat this, it is helpful to raise awareness for cloud security issues and train personnel in identity, authentication and access management mechanisms. Without training and education, human error and social engineering attacks are likely to prevail.
Lack of security and technology expertise: Migrating the entire on-premises IT infrastructure or individual services to the cloud requires personnel who understand cloud technologies and the associated security and data protection aspects. However, the demand for cloud security experts in the healthcare sector is higher than its supply, hindering cloud computing advancement.
Cybersecurity investment is not a priority: Lack of management buy-in and restricted public financing results in less support to promote the digitalization efforts and to increase cybersecurity and data protection maturity in the healthcare sector.
Regulatory compliance of cloud providers: Healthcare is a heavily regulated industry. As a result, organizations are facing difficulties identifying cloud vendors that are compliant with their legal requirements, thereby limiting their options.
Integration of cloud with legacy systems: The integration of cloud solutions with existing infrastructure is challenging and motivates some organizations to refrain from using cloud services. In many cases, legacy systems that are part of health IT infrastructure cannot be updated, which complicates integration and interoperability with new technologies. Consequently, these systems are more vulnerable to cybersecurity attacks.
Data protection challenges
Privacy by design techniques: The GDPR introduces a legal requirement on privacy by design and by default for both data controllers and data processors. Therefore, healthcare organizations need to ensure that cloud vendors employ such an approach when developing and deploying the service.
Data governance: Healthcare organizations collect and manage patient data. This information is either automatically transferred to the cloud via medical connected devices, or it is submitted by medical practitioners. Data accuracy is essential for healthcare providers. Organizations need to establish data governance policies to identify and classify sensitive data and then apply controls to ensure data accuracy.
Data deletion: It is extremely important to be able to erase data after retention time has expired or upon the data subject’s request without undue delay. However, effective data deletion is a technical challenge.
Encryption: Encryption is important to ensure secrecy and integrity, and it must be applied both to data at rest and data in transit. Encryption needs to be implemented at client- and server-side but also in the channel connecting them.
Cloud security best practices
To address these challenges, ENISA suggests implementing the following security and data protection measures.
- Identify security and data protection requirements such as legislation, internal policies and legal requirements for specific products.
- Conduct a risk assessment and data protection impact assessment to identify cybersecurity and data protection threats and risks for cloud deployments and evaluate the impact of the overall risk.
- Establish processes for security and data protection incident management and define the actions to be taken after a cloud provider security incident. Define roles and responsibilities and align actions with the cloud provider’s security provisions.
- Define business continuity processes, assign roles and responsibilities, ensure adequate backup and identify the cloud provider’s responsibilities in the event of a service disruption.
- Identify disaster recovery requirements and ensure that the disaster recovery and data restore processes of the cloud service provider meet these requirements.
- Ensure the organization’s data are either removed upon contract termination or deleted if data retention period has expired.
- Define requirements for event logging and continuous monitoring.
- Determine and setup processes for vulnerability and patch management.
- Identify, inventory and classify data stored in cloud environments.
- Enable and ensure encryption for data at rest and in transit.
- Define security requirements for key management and ensure procedures for key management are implemented.
- Ensure all data is provided in a standardized format upon request from the cloud provider.
- Identify and inventory all devices and endpoints and define security baseline for hardening these assets.
- Ensure and enforce strong authentication and access controls.
- Establish regular, targeted awareness and training programs for employees and partners.
- Ensure that traffic between untrusted and trusted environments is restricted and monitored.
- Apply segmentation practices in accordance with need-to-know, least-privilege principles.
- Ensure the cloud service provider provides physical security controls to protect data centers and prevent unauthorized physical access.
Conclusion
The adoption of cloud solutions by the healthcare organizations presents improvements in availability, scalability and reliability of services to remote patients. It introduces several security and data protection challenges that need to be addressed to accelerate the digitalization of the healthcare sector. Healthcare organizations should implement the measures described in the ENISA report to ensure the reliability and effectiveness of their operations. However, support is required from government and EU authorities to overcome barriers like understaffing and underbudgeting in hospitals.
You can learn more about how Tripwire helps to secure healthcare infrastructure and protect patient data here.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” ENISA Releases Guidelines for Cloud Security for Healthcare Services” appeared first on TripWire
