Cosmic Lynx: The Highly-Professional Cybercrime Gang Scamming Businesses Out of Millions of Dollars

Things just got serious.
Business Email Compromise is no longer solely the province of chancers and opportunistic Nigerian actors such as the Yahoo Boys. Organised criminal gangs with a high level of professionalism have seen the opportunity and seized it.
Security researchers at Agari have published a report detailing their investigations into a Russian cybercrime gang they say have stolen millions of dollars from companies in 46 countries since mid-2019.
What makes the report particularly interesting is that the Cosmic Lynx gang is believed to have moved on from their tried-and-trusted techniques of using banking trojans and click fraud malware to generate income into highly professional Business Email Compromise (BEC) attacks.
The attacks specifically target senior executives at Fortune 500 or Global 2000 companies, with three quarters of those in Cosmic Lynx’s sights holding job titles such as General Manager, Managing Director or Vice President.
According to Agari’s investigation, an attack typically begins with the gang’s impersonation of a company’s CEO, asking a targeted employee to work with “external legal counsel” to co-ordinate payments required to close a fake corporate merger or acquisition. Of course, the scammers also require the targeted employee to keep details of the transaction strictly confidential because of their “sensitive nature.”
Cosmic Lynx’s professional approach to cybercrime means that its email communications are not riddled with grammatical errors or misspelled words which might ring alarm bells for a recipient. Instead, the emails are detailed and use vocabulary that wouldn’t look amiss from the typical Chief Executive Officer.
Some of the emails even open with a paragraph or two about the current COVID-19 pandemic in an attempt to build rapport with their intended victim, and disarm any suspicions.
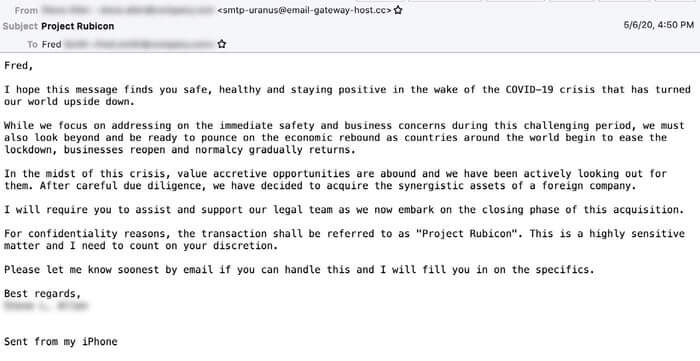
Part of one email reads:
I hope this measure finds you safe, healthy and staying positive in the wake of the COVID-19 crisis that has turned our world upside down.
While we focus on addressing on the immediate safety and business concerns during this challenging period, we must also look beyond and be ready to pounce on the economic rebound as countries around the world begin to ease the lockdown, businesses reopen and normalcy gradually returns.
In the midst of this crisis, value accretive opportunities are abound and we have been actively looking out for them. After careful due diligence, we have decided to acquire the synergistic assets of a foreign company.
I will require you to assist and support our legal team as we now embark on the closing phase of this acquisition.
All of this, of course, is just the beginning of the scam and is intended to introduce the targeted employee to a “lawyer” who will provide assistance during the fake acquisition of the foreign company.
According to Agari’s research, nearly all of the lawyers impersonated during the attacks are based in the United Kingdom.


To make the email more convincing, the emails from the fake lawyer are sent from a domain that closely resembles a genuine law firm’s domain. In addition, the emails contain a picture of the impersonated lawyer (presumably taken from the genuine law firm’s website or LinkedIn), alongside a link to the real law firm’s website, and the type of confidentiality disclaimer abhorred by environmentalists the world over.
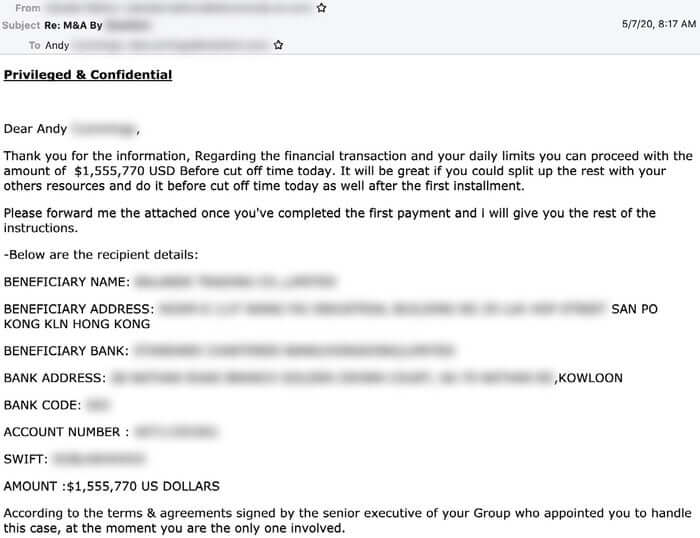
Ultimately, if they do not realise that they are being targeted by a highly professional team of scammers, the targeted employee will be duped into moving funds into bank accounts operated by money mules, typically located in Hong Kong.

According to the FBI, Business Email Compromise has cost victims a staggering $26 billion over a three year period, and – if anything – is showing all the signs of becoming even more popular amongst cybercriminal gangs looking to steal themselves a fortune.
The fact that organised professional criminal gangs like Cosmic Lynx, who have previously been associated with other malicious activity – such as Android click fraud and Emotet and Trickbot banking malware attacks – are now venturing forcefully into the field of BEC should act as a stark warning for all organisations to take the threat more seriously.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” Cosmic Lynx: The Highly-Professional Cybercrime Gang Scamming Businesses Out of Millions of Dollars” appeared first on TripWire
Source:TripWire – Graham Cluley
