BlackCat ransomware – what you need to know

What is this BlackCat thing I’ve heard about?
BlackCat (also known as ALPHV) is a relatively new ransomware-as-a-service (RaaS) operation, which has been aggressively recruiting affiliates from other ransomware groups and targeting organisations worldwide.
What makes BlackCat different from other ransomware-as-a-service providers?
Like other ransomware groups, BlackCat extorts money from targeted organisations by stealing sensitive data (and threatening to release it publicly), and encrypting systems. But BlackCat goes one stage further and also threatens to launch a distributed denial-of-service (DDoS) attack if its demands are not met.
This technique is known as “triple extortion.”
Furthermore, BlackCat has gained traction since late 2021 by offering payouts to its affiliates of up to 90%.
So criminals who previously worked with the REvil, BlackMatter, and DarkSide ransomware gangs may be lured to using BlackCat instead?
Precisely.
And the potential financial gains to be made by BlackCat ransomware affiliates may be further boosted by the fact that the sophisticated BlackCat ransomware is written in the Rust programming language. The use of Rust reduces the chances of the ransomware executable containing bugs that security researchers may be able to exploit, as well as making it fast to find and encrypt files on targeted networks, and able to run on Windows and Linux systems.
So, it’s not just Windows computers that could be hit?
Correct. Which means that there is potential for even more computer systems within an organisation to be hit – including some that IT administrators may have previously imagined would have been avoided.
Sounds nasty. Have their been able high profile attacks linked to the BlackCat ransomware group?
ZDNet reports that BlackCat was responsible for last weekend’s attack on two German oil companies, causing serious disruption for hundreds of gas stations, and caused Shell to reroute supplies.
How much money are BlackCat asking for?
That will vary depending on the target, but some companies have reportedly been the recipients of demands of up to $14 million.
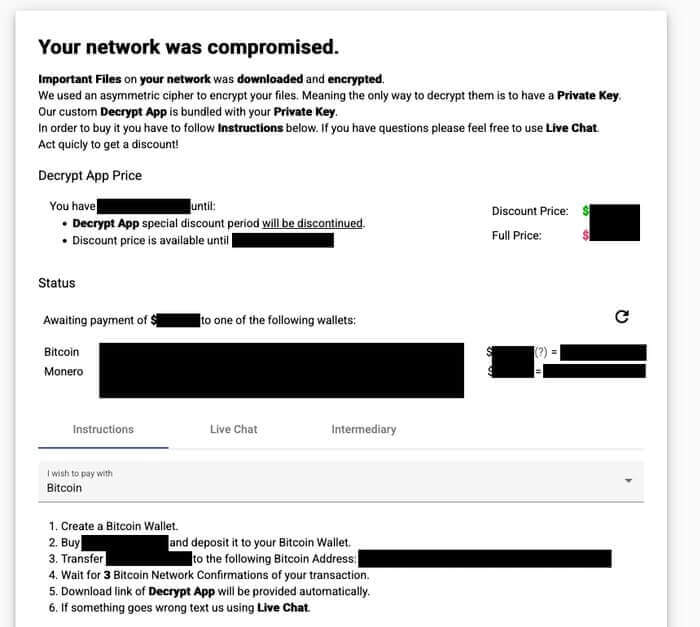
Discounts are available for companies who pay up early.
That’s kind of the cybercriminals! Do we know who is responsible?
It seems likely that BlackCat has been born out of the ashes of other ransomware groups, some of whom have been feeling the heat lately due to a number of arrests and action being taken against infrastructure by law enforcement.
Investigative cybersecurity reporter Brian Krebs has published an interesting account of his contact with online criminals who may be associated with BlackCat.
What can be said with some certainty is that the group is Russian-speaking.
So how can my company protect itself from the BlackCat ransomware?
It’s the same advice as with other ransomware, which includes
- making secure offsite backups.
- running up-to-date security solutions and ensuring that your computers are protected with the latest security patches against vulnerabilities.
- using hard-to-crack unique passwords to protect sensitive data and accounts, as well as enabling multi-factor authentication.
- encrypting sensitive data wherever possible.
- educating and informing staff about the risks and methods used by cybercriminals to launch attacks and steal data.
If my company has been unlucky enough to have fallen victim to BlackCat, should we pay the ransom?
That’s a decision that only your company can make. The more companies that pay a ransom, the more likely it is that criminals will launch similar attacks in the future.
At the same time, your business may feel it has no choice but to make the difficult decision to pay if the alternative is to risk the entire business.
Whatever your decision, you should inform law enforcement agencies of the incident and work with them to help them investigate who might be behind the attacks.
And remember this: paying the ransom does not necessarily mean you have erased the security problems that allowed you to be infected in the first place. If you don’t find out what went wrong – and why – and fix it, then you could easily fall victim to further cybercrime attacks in the future.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” BlackCat ransomware – what you need to know” appeared first on TripWire
Source:TripWire – Graham Cluley
