Barnes & Noble warns customers it has been hacked, customer data may have been accessed

American bookselling giant Barnes & Noble is contacting customers via email, warning them that its network was breached by hackers, and that sensitive information about shoppers may have been accessed.
In the email to customers, Barnes & Noble says that it became aware that it had fallen victim to a cybersecurity attack on Saturday October 10th.
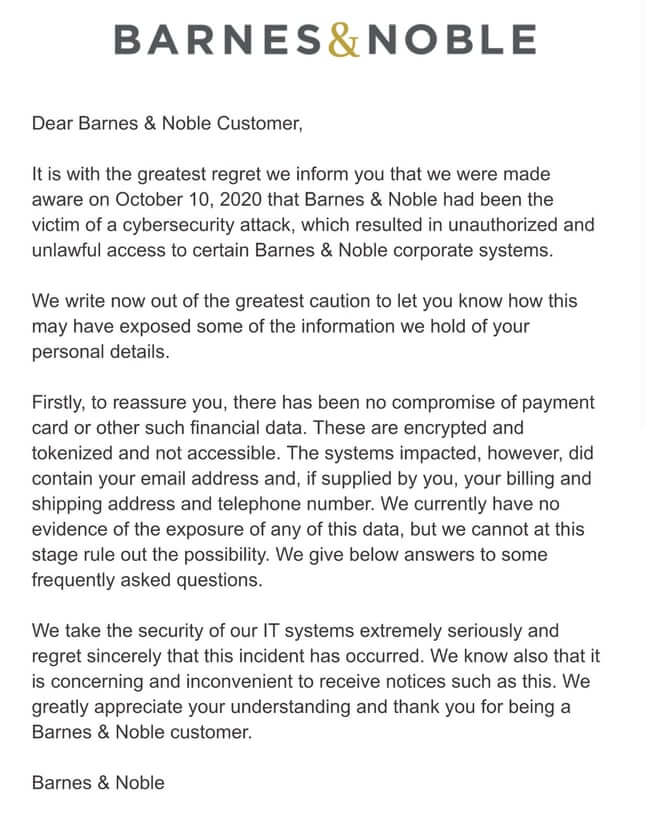
Part of the email reads:
“It is with the greatest regret we inform you that we were made aware on October 10, 2020 that Barnes & Noble had been the victim of a cybersecurity attack, which resulted in unauthorized and unlawful access to certain Barnes & Noble corporate systems.”
“Your payment details have not been exposed. Barnes & Noble uses technology that encrypts all credit cards and at no time is there any unencrypted payment information in any Barnes & Noble system. No financial information was accessible. It is always encrypted and tokenized.”
However, although payment information might be considered at risk – the bookseller says that there was personal information stored on the compromised servers, including customers’ email addresses, billing and shipping addresses, and telephone numbers.
In addition, Barnes & Noble stores details of customers’ past transactions, revealing a history of books and other products that have been purchased from the retailer in the past. Depending on your literary tastes, that clearly could prove embarrassing.
The company says that although it has no evidence that the personal details have been exposed by the security breach, it “cannot at this stage rule out the possibility.”
When I hear a company say, effectively, “it doesn’t know” if certain details were accessed by hackers my recommendation is to assume the worst.
The confirmation of a security breach came after a weekend of complaints from Barnes & Noble customers who complained that they were unable to download books they had purchased to their Nook ebook readers:
“I’d really really really like to read the book I bought a few days ago.”
“Good thing your payment processing isn’t down or else you wouldn’t be able to take my money for books I can’t read.”
“I was able to finally access the shop just now, but can’t download my purchases from the server. Basically I can buy books but can’t access the books I already purchased!”
According to Barnes & Noble’s Nook Twitter account, a “system failure” was responsible for the service interruption for Nook owners. The firm said it was “working urgently to get all NOOK services back to full operation. Unfortunately it has taken longer than anticipated, and we sincerely apologize for this inconvenience and frustration.”
One assumes that the “system failure” was related to the hack, and there is inevitably going to be speculation that Barnes & Noble might be the latest in a long line of companies to have suffered a ransomware attack – perhaps combined with the exfiltration of data from the compromised servers.
Credence to that theory is given by security researcher Troy Mursch (also known as @BadPackets) who has claimed on Twitter that Barnes & Noble has been running Pulse Secure VPN servers for months that have not been patched against the critical CVE-2019-11510 vulnerability.
The security hole in unpatched Pulse Secure VPN servers has been exploited on other occasions to steal usernames and passwords, giving easy access to hackers keen to break into a company’s internal network. This method has been used on many occasions to install ransomware on networks, and blackmail corporate victims.
With that in mind, if ransomware has indeed been planted on Barnes & Noble’s network and caused the system outage the clues about what was going to happen might have been there for all to see for a while.
In August, ZDNet reported that plaintext usernames and passwords for over 900 Pulse Secure VPN enterprise servers were being distributed on a Russian-speaking hacking forum.
Amongst those companies included in the list? Barnes & Noble.
Customers of the bookseller would be wise to be wary of unsolicited emails they might receive, now their details might be in the hands of criminal hackers. However, I suspect the biggest victim of this attack is likely to be Barnes & Noble itself as it attempts to bring its systems back online and recover from the damage done to its brand and reputation.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” Barnes & Noble warns customers it has been hacked, customer data may have been accessed” appeared first on TripWire
Source:TripWire – Graham Cluley
