Average ransomware payouts shoot up 171% to over $300,000

Organisations hit by ransomware attacks are finding themselves paying out more than ever before, according to a new report from Palo Alto Networks.
The Unit 42 threat intelligence team at Palo Alto Networks teamed up with the incident response team at Crypsis to produce their latest threat report which looks at the latest trends in ransomware, and compares payment trends to previous years.
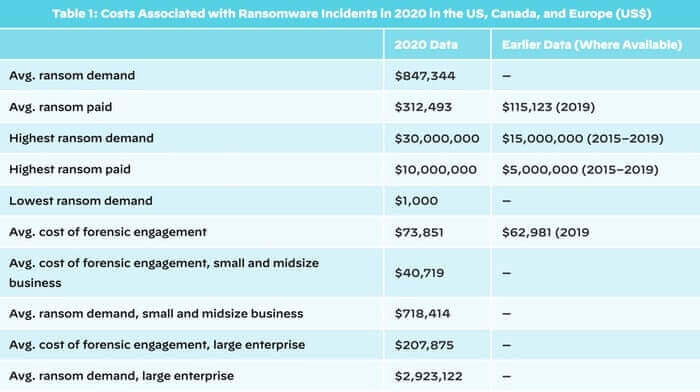
According to the research, the average payment following a ransomware attack in 2020 rocketed up 171% to $312,493 compared to $115,123 in 2019.
And it’s not just the case that the criminals behind ransomware attacks are making more from their victims – they’re also becoming greedier.
The report reveals that the highest ransom demanded in 2020 ($30 million) was double the highest seen throughout the period 2015-2019 ($15 million). Those sky-high demands were reflected in big pay-days for attackers, with the highest measured at $10 million – again, twice as big as the highest seen during the previous five years.
On average, according to the researchers, ransomware operators demanded an eye-watering $847,344 for each ransomware attack during 2020.
These high figures, and the seeming ease with which malicious hackers have managed to successfully infiltrate more and more organisations and extort money from them, have taken place as ransomware attacks have increasingly turned into a “double-extortion” model:
“In a case of double extortion, ransomware operators encrypt and steal data to further coerce a victim into paying a ransom. If the victim doesn’t pay the ransom, the ransomware operators then leak the data on a leak site or dark web domain, with the majority of leak sites hosted on the dark web. These hosting locations are created and managed by the ransomware operators. At least 16 different ransomware variants are now threatening to expose data or utilizing leak sites, and more variants will likely continue this trend.”
With a traditional ransomware attack, a solution is to simply restore your data from an uncompromised backup.
But restoring from a backup doesn’t undo the damage done if an attacker has exfiltrated your data and is threatening to sell it on to other criminals, or publish it on the web.
In some cases, ransomware operators have even reached out to security journalists in an attempt to maximise damage to a corporation’s brand, or threatened to contact investors in an attempt to knock a breached business’s share price.
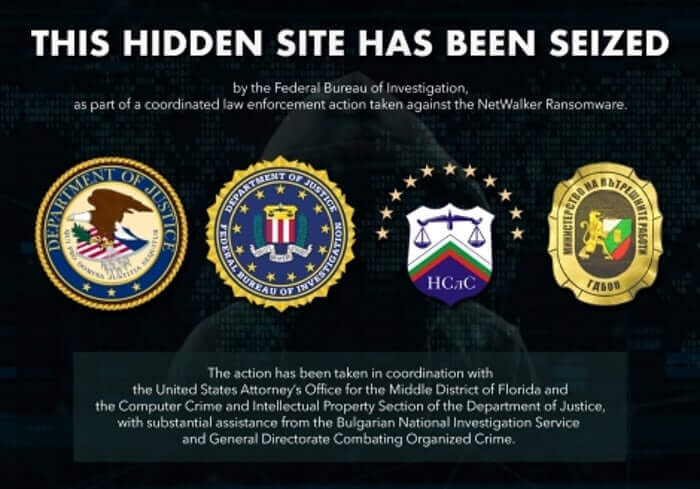
According to the report, the ransomware operation which was most engaged in leaking data between January 2020 and January 2021 was NetWalker. NetWalker leaked the data of some 113 organisations around the world, exceeding by far the next closest ransomware family RagnarLocker which leaked data from 26 victims.
The good news is that in January this year, law enforcement agencies around the world worked together to disrupt the operations of the NetWalker gang, and the website it used to leak data has been seized.

Good news as that is, the success of ransomware attacks has – no doubt – encouraged a rise in interest from other criminals to move into the arena.
Ransomware is a serious problem which can have significant impacts – but financial and operational – on companies of all sizes. Make sure that your business is following best practice advice and tips on how to reduce the chances of an effective ransomware attack.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” Average ransomware payouts shoot up 171% to over $300,000″ appeared first on TripWire
Source:TripWire – Graham Cluley
