Application Security Report 2022: Key Trends and Challenges

At a time when the state of cybersecurity is constantly changing, with new and increasing threats arising each day, it is vital for all organizations to keep it near the top of their list of priorities. Business applications are increasingly targeted by cybercriminals, and their ability to protect and defend themselves against these attacks is a crucial part of their operations. Just as there are many different kinds of cybercriminals and cyberattacks, there are many ways a business may choose to go about bolstering their application security.
In an effort to explore the current state of application security, Cybersecurity Insiders partnered with Beyond Security by HelpSystems to conduct an in-depth study of cybersecurity trends. The resulting report is based on a comprehensive survey of cybersecurity professionals to gain insight into current trends, challenges, and solutions for application security. The respondents’ demographics vary based on career level, department, company size, industry, and resources in order to create a balanced representative sample.
Major concerns and challenges
According to 44% of survey respondents, one of the biggest application security concerns for organizations is protecting data. Additionally, 42% of respondents are concerned about keeping up with the rising number of vulnerabilities, 38% about threat and breach detection, and 37% about securing cloud applications. Other major concerns cited by cybersecurity professionals include securing applications they develop (37%) and protecting against malware (29%).
When asked which types of applications present the highest security risk to businesses, 42% of respondents say customer-facing web apps and 40% cite legacy apps. Trailing behind a bit, but still posing a risk are mobile apps (30%), desktop apps (28%), and internal-facing web apps (26%).
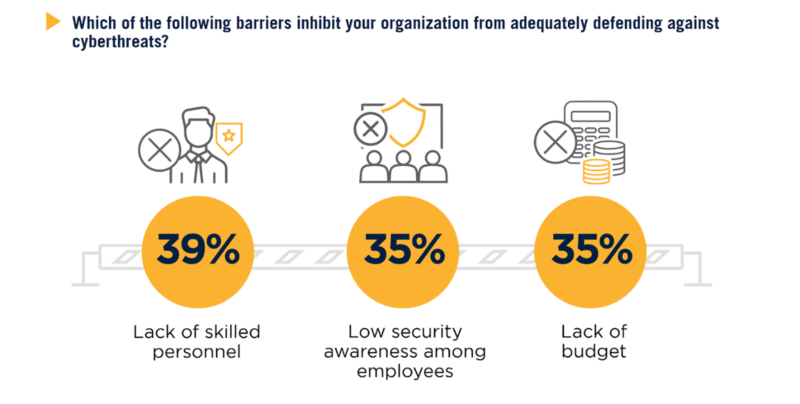
The study also strives to understand what potential problems may be serving as an obstacle for businesses to better defend themselves against attacks on applications. The challenges that organizations cite as major barriers to better defense include a lack of skilled personnel (39%), low security awareness among employees (35%), and lack of budget (35%), followed by a lack of collaboration between departments (29%), and lack of management support and awareness (26%).
Similar problems crop up in the course of penetration testing business applications. When asked about the biggest challenge to penetration testing, 25% of respondents cite difficulty in finding and hiring skilled people, while 16% say it is too expensive to test as many applications as they would like, and 13% say it is too expensive to test as frequently as they would like. Additionally, 45% say that the pressure to develop and release new software quickly causes application developers to neglect secure coding practices.
Attacks on applications: how common are they, and what forms do they take?
Of the organizations surveyed, 44% have experienced data breaches, including a total of 20% within the past year alone. While 24% of respondents have not experienced any data breaches, a concerning 32% are not sure if they have experienced an application breach or compromise in the past.
Regarding security attacks against applications within the last 12 months, 31% of respondents say they have been targeted by malware attacks, followed by 23% who have experienced distributed denial-of-service (DDoS) attacks, 21% who have experienced application misconfiguration, and 20% who have experienced stolen credentials. While the major threats remain much the same, attacks on applications are increasing in volume and risk.
How organizations are protecting against attacks
A majority of organizations (91%) have a dedicated application security program of some sort in place. While a relatively small 9% of those surveyed rely exclusively on outsourced application security, 39% of these businesses use in-house management, and 36% employ a combination of in-house and outsourced application security. This means that organizations are largely basing their application security at least partially on the skill and expertise of their own cybersecurity professionals.
One way to secure business applications is to test them automatically at some point, or at multiple points, during development and release. When it comes to automatic security testing, 54% of organizations surveyed have some kind of automated testing in the software release lifecycle. Of those organizations, 48% automate security testing during software testing, 31% during monitoring, 29% during code development, and 23% during product release. A smaller proportion of organizations automate security testing during operation review (16%) and planning (15%).
Overall, the study shows that organizations are taking application security seriously and working to secure their applications against attacks. An encouraging 51% of respondents project an increased application security budget over the next 12 months, as well as 34% who expect their budgets to remain level.
Conclusions
Attacks against applications are a growing threat, putting businesses at risk of malware, disruption, theft, and misconfiguration exploits. Organizations must put time, effort, and money into ensuring the security of their applications, and the majority of those surveyed for this study see application security as a priority and a major concern.
While organizations understand the importance of application security and are willing to put the work in, there are several obstacles that make it difficult to put into practice. The most challenging barriers in place are lack of personnel, staff security awareness, and not having a suitable budget to secure applications. However, more than half of those surveyed expect to see a budget increase for application security in the upcoming year.
For more information, you can find the full survey here.
The post ” Application Security Report 2022: Key Trends and Challenges” appeared first on TripWire
