Achieve CIS Compliance in Cloud, Container and DevOps Environments

If you are embracing DevOps, cloud and containers, you may be at risk if you’re not keeping your security methodologies up to date with these new technologies. New security techniques are required in order to keep up with current technology trends, and the Center for Internet Security (CIS) provides free cybersecurity best practices for many newer platforms.
The CIS benchmarks and controls provide clear instruction to help any organization tackle threats and reduce risk. Meanwhile, Tripwire makes benchmark alignment simple in cloud and container environments, securing each component of your DevOps toolchain.
Cloud
Many organizations are moving on-premise infrastructure into the cloud, which requires a wealth of new security know-how. Traditional security monitoring tools may lack visibility into these new environments. CIS has released benchmarks for Amazon Web Services, Microsoft Azure and Google Cloud Platform, giving much-needed guidance for those charged with securing these platforms. These benchmarks cover both familiar topics with a cloud twist and also new paradigms, everything from Identity and Access Management (IAM) configuration to virtual networking and computing.
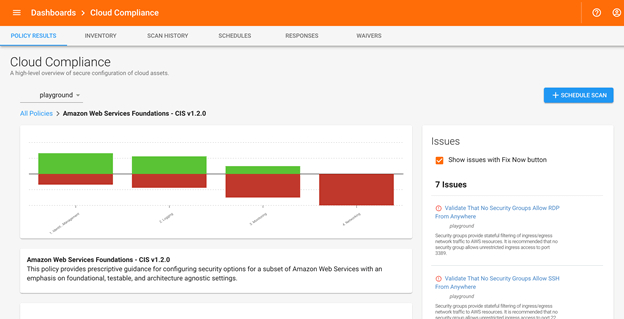
Tripwire Configuration Manager helps overcome the cloud infrastructure visibility problem, allowing the monitoring of cloud configuration data and validation of CIS compliance within your cloud platforms. Common misconfigurations can be automatically remedied and enforced by Tripwire Configuration Manager, elevating your security baseline in less time while requiring fewer resources.
Containers
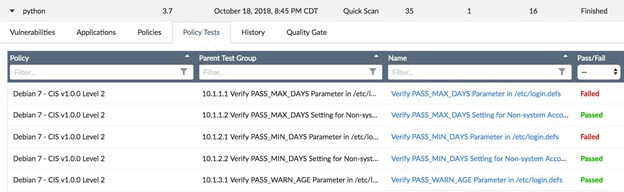
Another hot topic is containerization, and many of those embracing containers are unaware that the misconfiguration of container hosts can be equivalent to granting domain administrator permissions to a successful attacker. Locking down your container hosts is essential, and CIS once again provides benchmarking guides for Docker and Kubernetes hosts to keep them secure.
Tripwire Enterprise powers automated monitoring of Docker and Kubernetes hosts for CIS compliance, ensuring a best practice security posture for your container hosts.
DevOps
While cloud and container infrastructure are important parts of DevOps, there are still more ways that Tripwire can help achieve CIS policy compliance within your DevOps process. Tripwire for DevOps allows for CIS benchmark policy evaluation of Docker images in your build pipeline. Performing compliance validation in your CI/CD tools, such as Jenkins or TeamCity, is one method of integrating security earlier in your DevOps cycle, or “shifting security to the left.”
This enables quicker time to resolution for any compliance issues arising in the development and deployment process, and can keep security risks from ever manifesting in your production environment.

Center for Internet Security benchmark recommendations are free cybersecurity best practice guidelines and a great first step for securing your DevOps infrastructure and components. They provide prioritized guidance and clear remediation steps for combating misconfigurations.
Tripwire solutions empower the user to achieve CIS policy compliance in both DevOps build processes and in an ongoing continuous manner once deployed by automating configuration checks and supplying clear remediation information.
Learn more about how Tripwire solutions can help secure your cloud, container and DevOps assets.
The post ” Achieve CIS Compliance in Cloud, Container and DevOps Environments” appeared first on TripWire
Source:TripWire – Ben Layer
