A Full Rainbow of Protection: Tripwire Is More than ‘Just FIM’

Imagine an arc. Not just any arc. A rainbow. When we think of a rainbow, it conjures impressions of color, inspiration and even supernatural characteristics. Does your cybersecurity program long for a magical pot of gold at the end of a rainbow? With all the moving parts of cybersecurity, sometimes it seems like we are merely chasing rainbows.
However, it doesn’t have to be that way. Now, thanks to the innovative products in the Tripwire catalog, there is a bridge between Information Technology (IT) and Operational Technology (OT). Surprisingly, that bridge resembles the arc, not only of a single but a double rainbow.
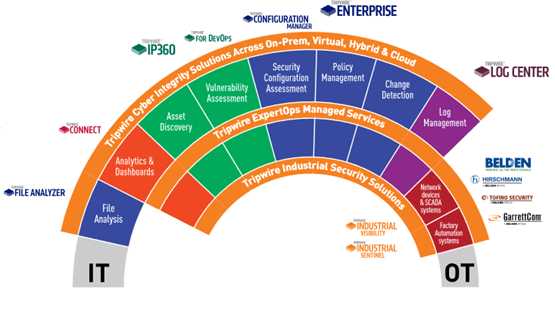
Tripwire has enhanced its Tripwire Enterprise product offering to keep pace with the expanding IT terrain. While IT and OT are still separate entities, their proximity is not as distant as it once was.
Tripwire’s Log Center™ gives your security team the ability to visualize the current security status of the IT environment by adding Tripwire’s deep configuration and change data with IT information stored in Splunk Enterprise. Log Center also filters and correlates the data then forwards only events of interest, a flow which not only reduces Splunk costs but also pulls in data from Tripwire Enterprise when used with the Tripwire Enterprise App for Splunk Enterprise. In so doing, it unites two of your most important workflow tools into one intuitive display.
Tripwire’s File Analyzer delivers detailed behavioral reports on suspicious files and executables in minutes straight from your Tripwire Enterprise console. Whether your data resides on-premises or in the cloud, File Analyzer inspects files in a quarantined sandbox environment. A comprehensive report is then provided within the Tripwire Enterprise console. It automatically provides behavioral information about files and executables, giving your team the visibility it needs to protect the organization.
The dynamic availability of containers makes them almost as ephemeral as a rainbow, running on moment and dormant the next according to need. Fortunately, with Tripwire IP360 for vulnerability management with granular risk scoring and prioritization, you can extend its capabilities into the cloud and discover Docker servers. Tripwire IP360 enumerates Docker containers (both running and non-running) and scans them for vulnerabilities. This includes the ability to scan offline containers, as well.
Attackers use automated tools to find misconfigured Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP) accounts and storage including AWS S3 buckets and Azure/GCP Blobs. Deploy your own automated monitoring to detect—and even automatically correct—misconfigurations before attackers gain an opening with Tripwire® Configuration Manager, which corrects human error and indicators of compromise automatically. Tripwire Configuration Manager provides periodic assessment of security settings compared with industry standards, specifically the Center for Internet Security (CIS) Foundations Benchmarks. You are immediately alerted to non-compliant settings that could be exposing your company. This stand-alone SaaS solution does not require a separate installation of Tripwire Enterprise.
This is only an introduction to the Tripwire product catalog. Tripwire offers so many services and products that it would seem like they have covered all colors of the rainbow. Whether your needs are on-premises or cloud-based or whether you are seeking a managed service to assist you in keeping your company secure, Tripwire is the right solution to help you bridge the IT and OT facets of your organization.
Want to read more about these and other offerings in the Tripwire product line? See our white paper here.
The post ” A Full Rainbow of Protection: Tripwire Is More than ‘Just FIM’” appeared first on TripWire
Source:TripWire – David Gilmore
