A Bank SMS Text Phish Attempt

Phishing attempts over text messages are becoming more prevalent. I received an SMS text message that contained a phishing attempt for a Canadian Bank. The message implied that I have received a new notification with this bank and I should visit the provided link. I usually do not click on any links, but I decided to see what would happen when I navigated to the page.
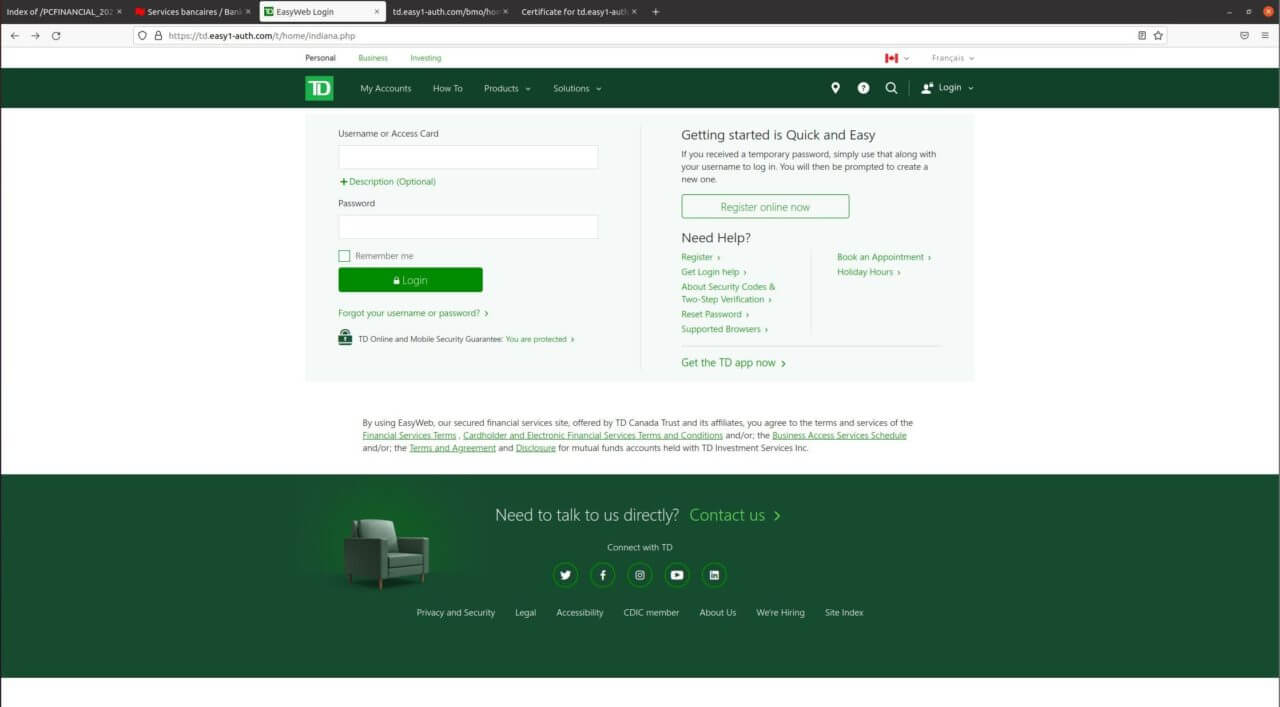
The Fake TD Login Page
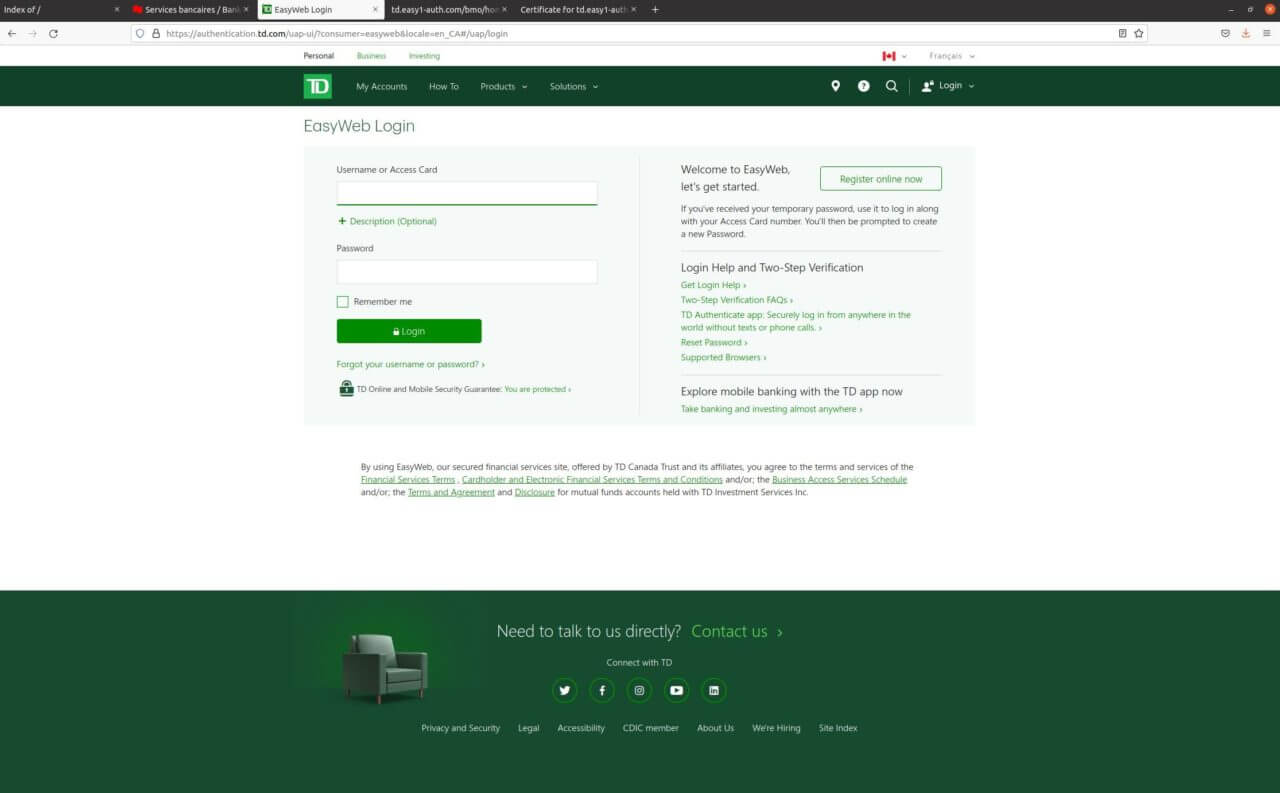
The fake login page looks very similar to the one that is displayed when you load the real TD web site. The text on the bottom of the fake login page was an exact copy from the real TD login page. The main difference was that the fake site was not functional and only offered the fake login form. If you tried to request any other page, the browser would report an issue with the fake web site. This seemed like an attempt to keep potential victims trapped on the current page. I hope that would have raised a red flag for potential victims.
Fake TD Login:

Real TD Login:

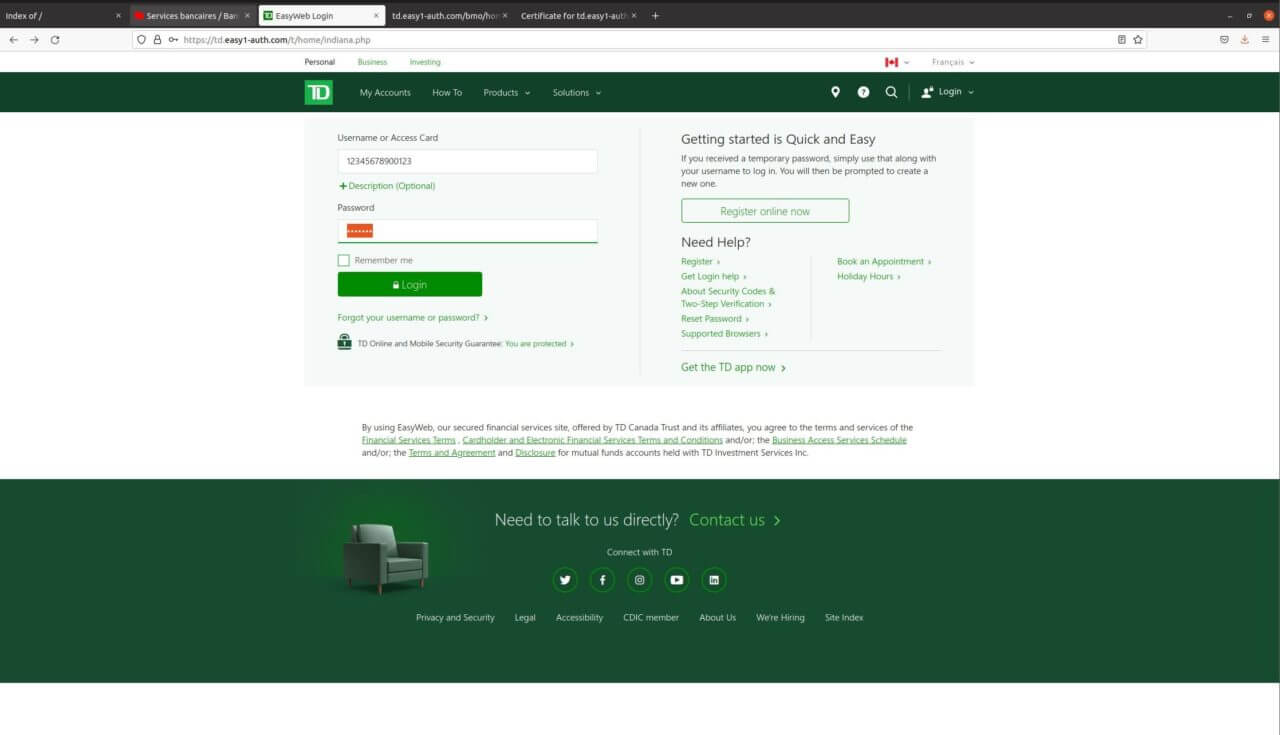
The Scam
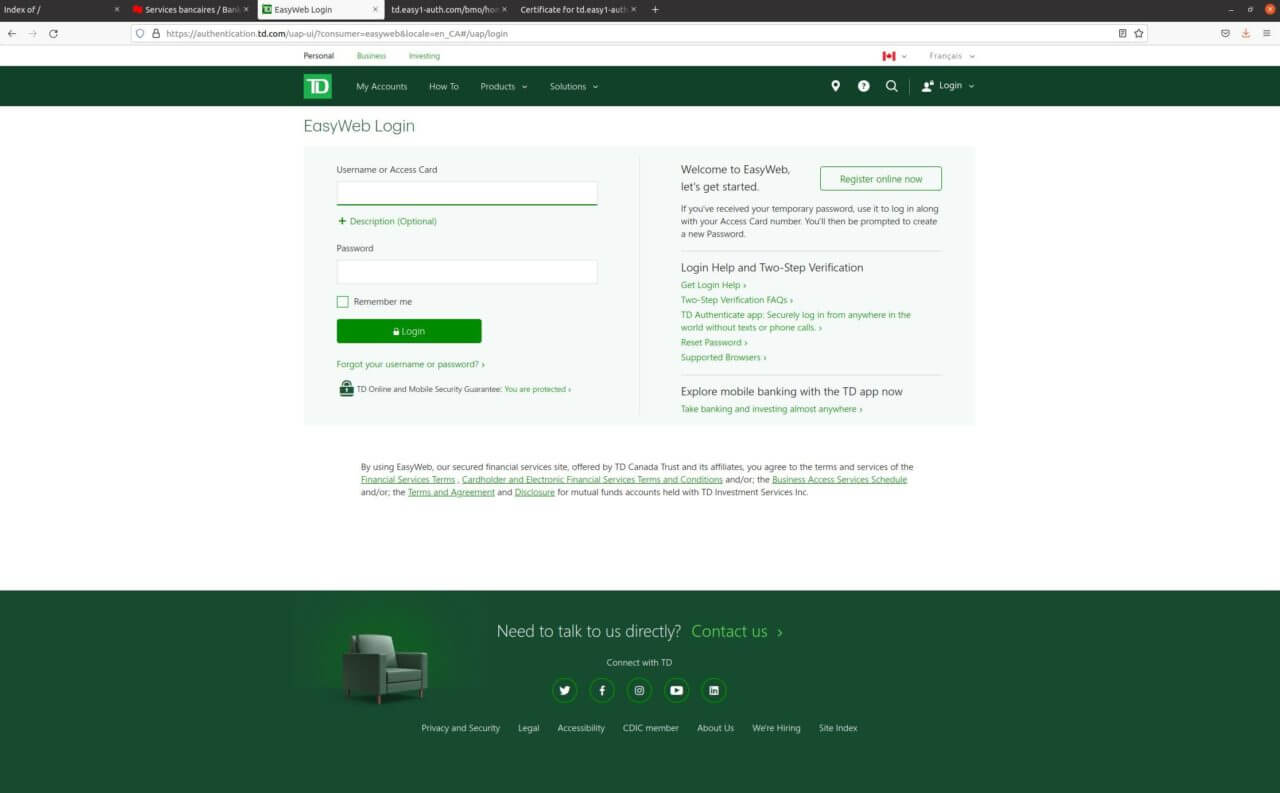
This scam is similar to previous bank scams in that it just captures all the input that is passed into the provided fields. Once all the required data is captured the fake web site redirects victims to the real TD login page. This allows any victim the ability to log into their bank account.
This part captures the bank card/access card and the password.

The next part of the phish was to get a customer to send their verification code to them. This is so the scammer could just log into the account without requesting a pin or bypassing the code.

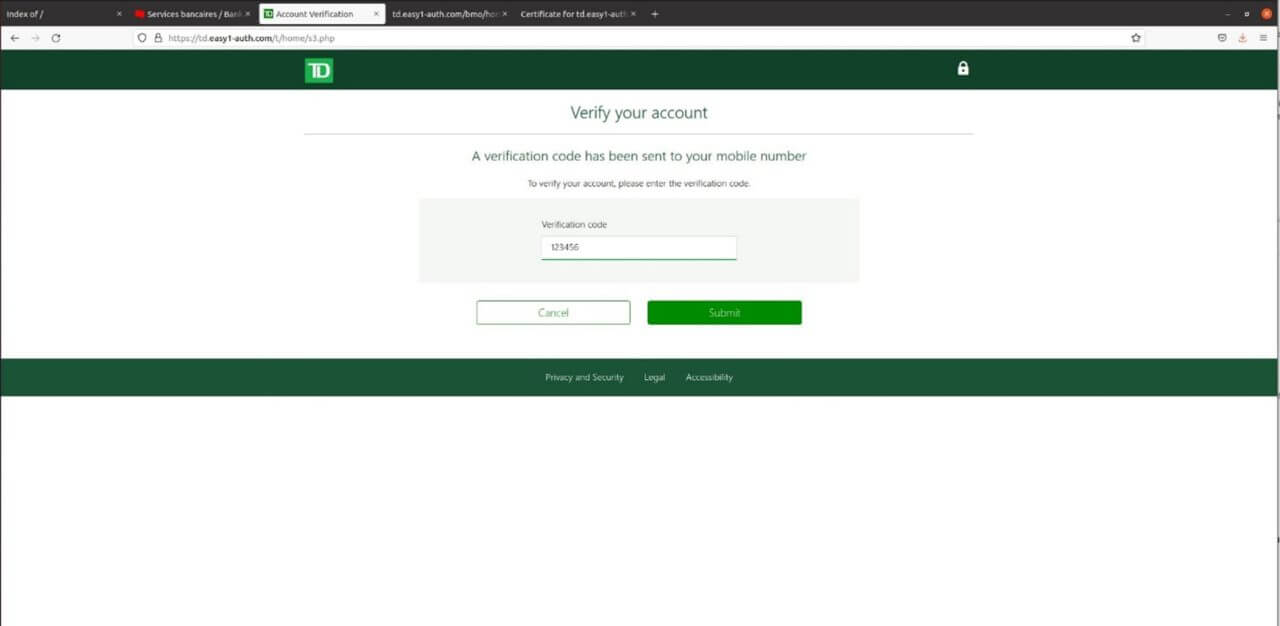
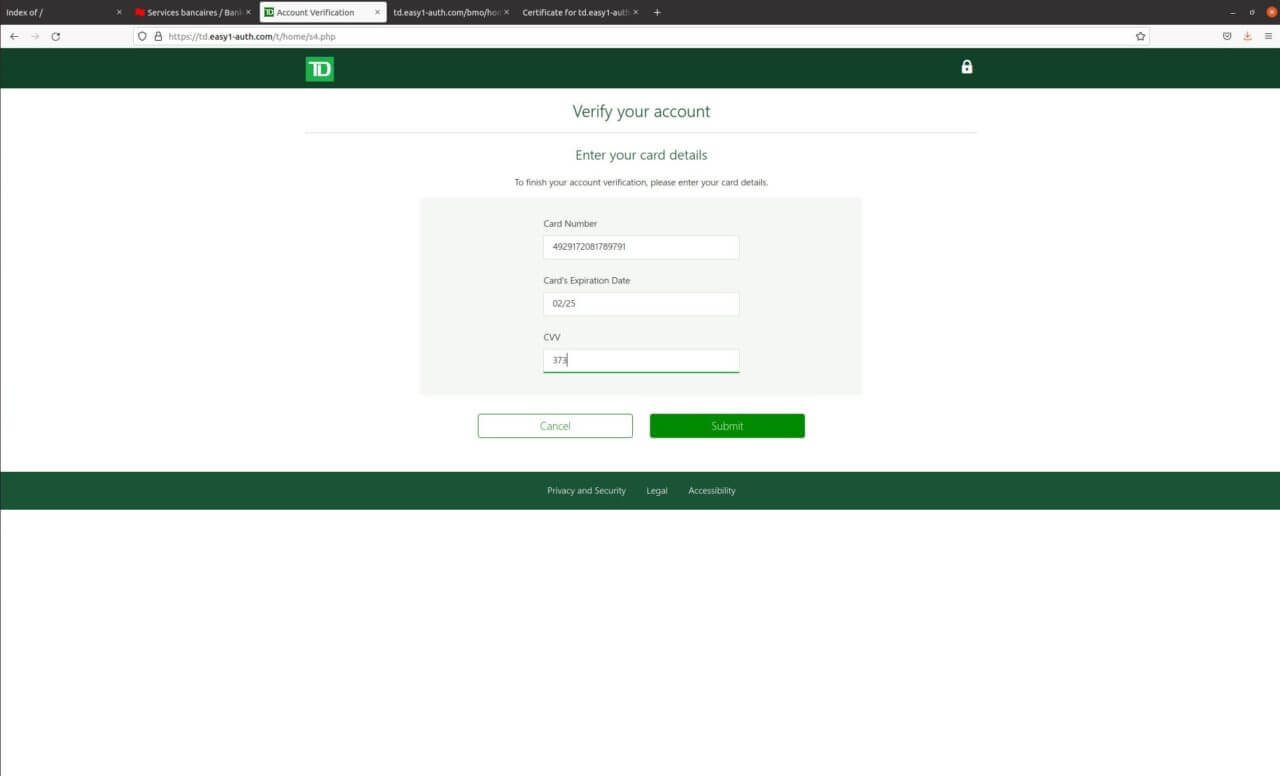
This part ensures that the scammer gets the correct card number. This might also give the scammer enough information to make a purchase.

Here you can see how victims would get redirected to the real TD login page.

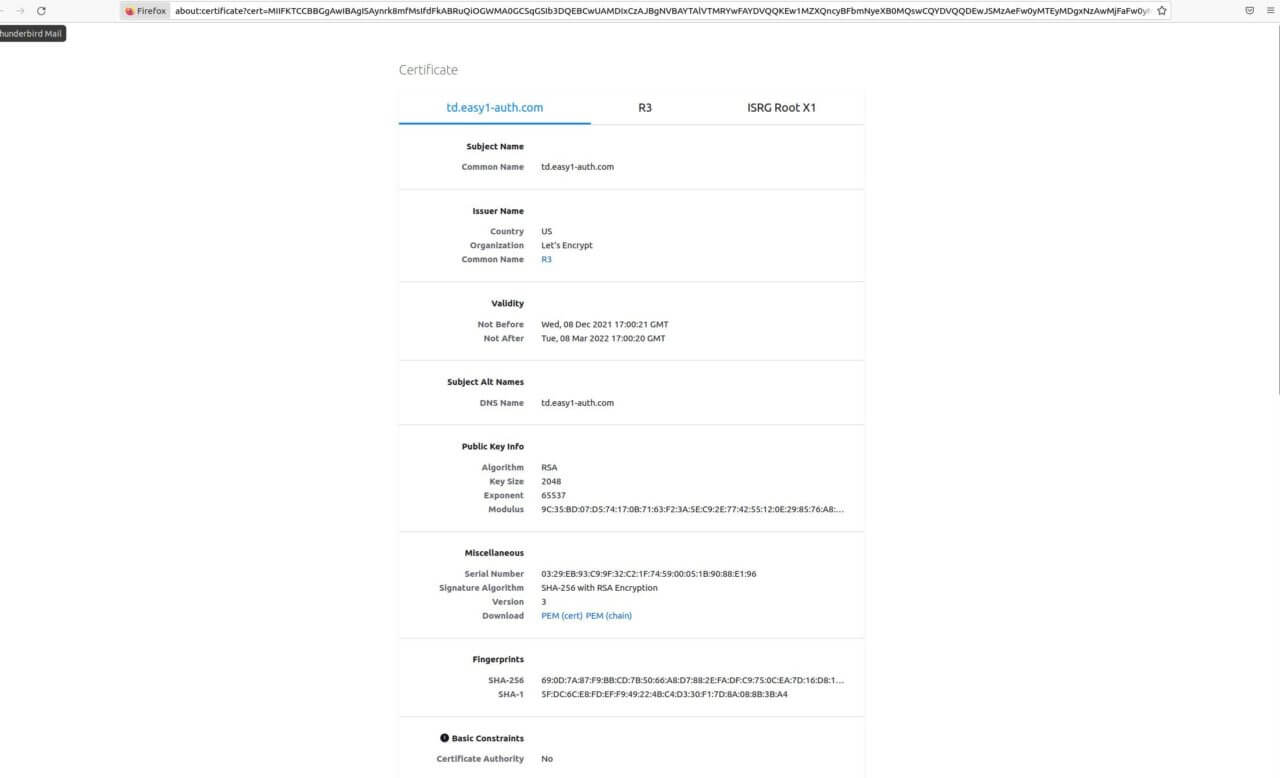
The Certificate
The browser should catch any site with an improper certificate, but this site had a valid certificate that was signed by Let’s Encrypt. I reported that a malicious web site was using the certificate to Let’s Encrypt. However, they refused to revoke the certificate because they do not monitor content of web sites. This feels very unfortunate given that they start that blog post by saying, “our mission is to help build a safer and more secure Web.”

The Server is Hosting Other Banking Scams
While investigating the server, I noticed that this server was host other Canadian Bank scams. The server also hosts fake login pages for BMO, TD, National Bank, and PC Financial.
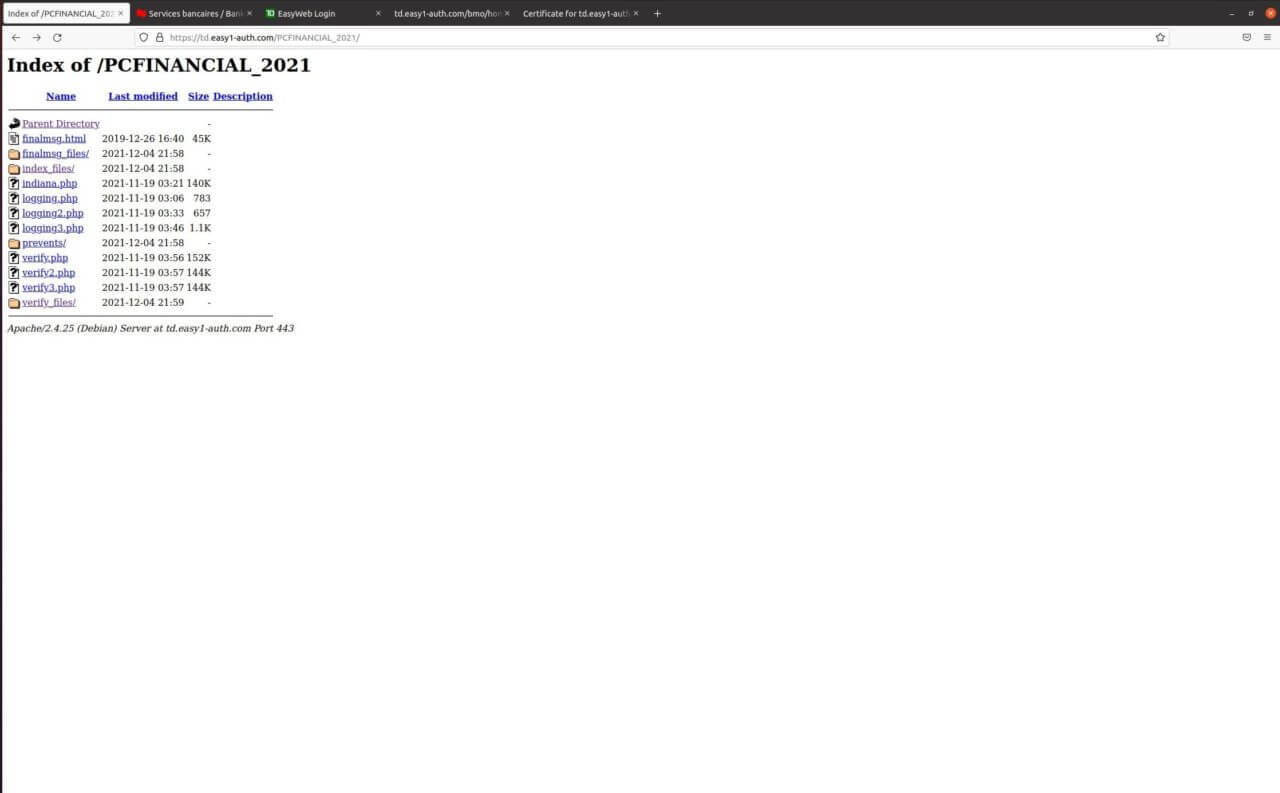
Here you can see the directory listing for other scams.

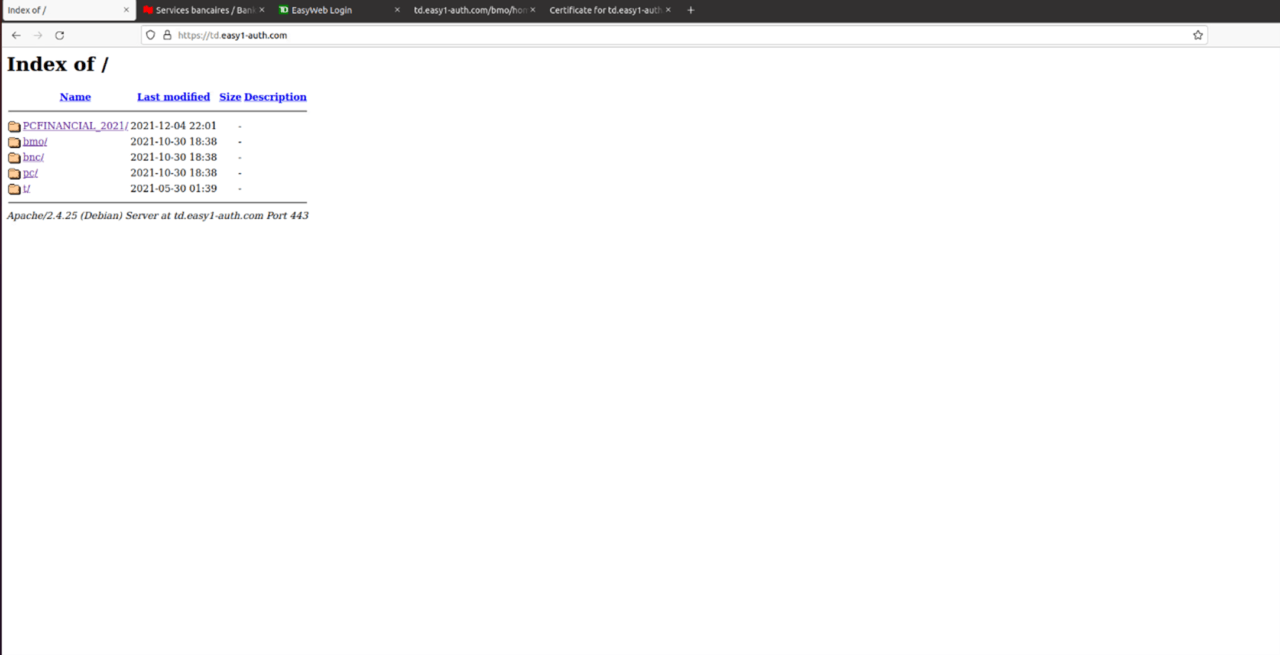
A BMO Scam:

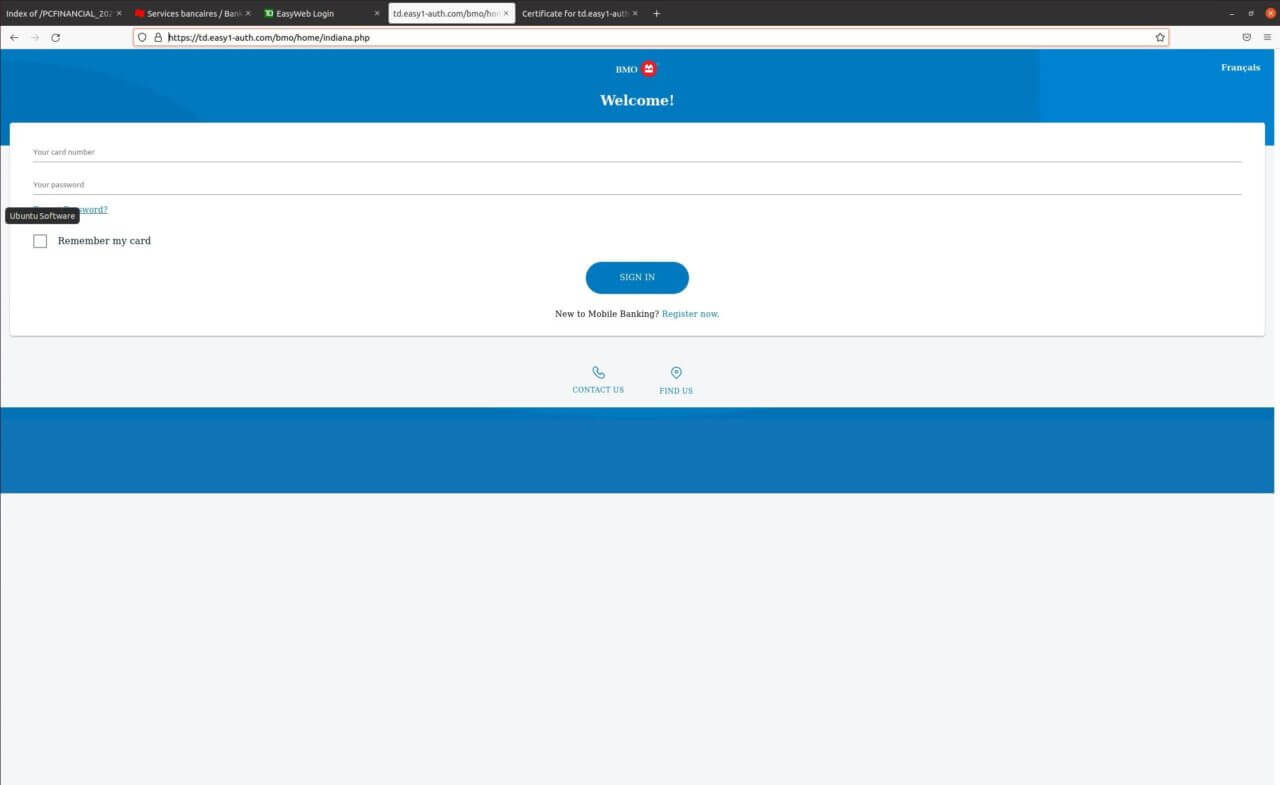
TD Scam:

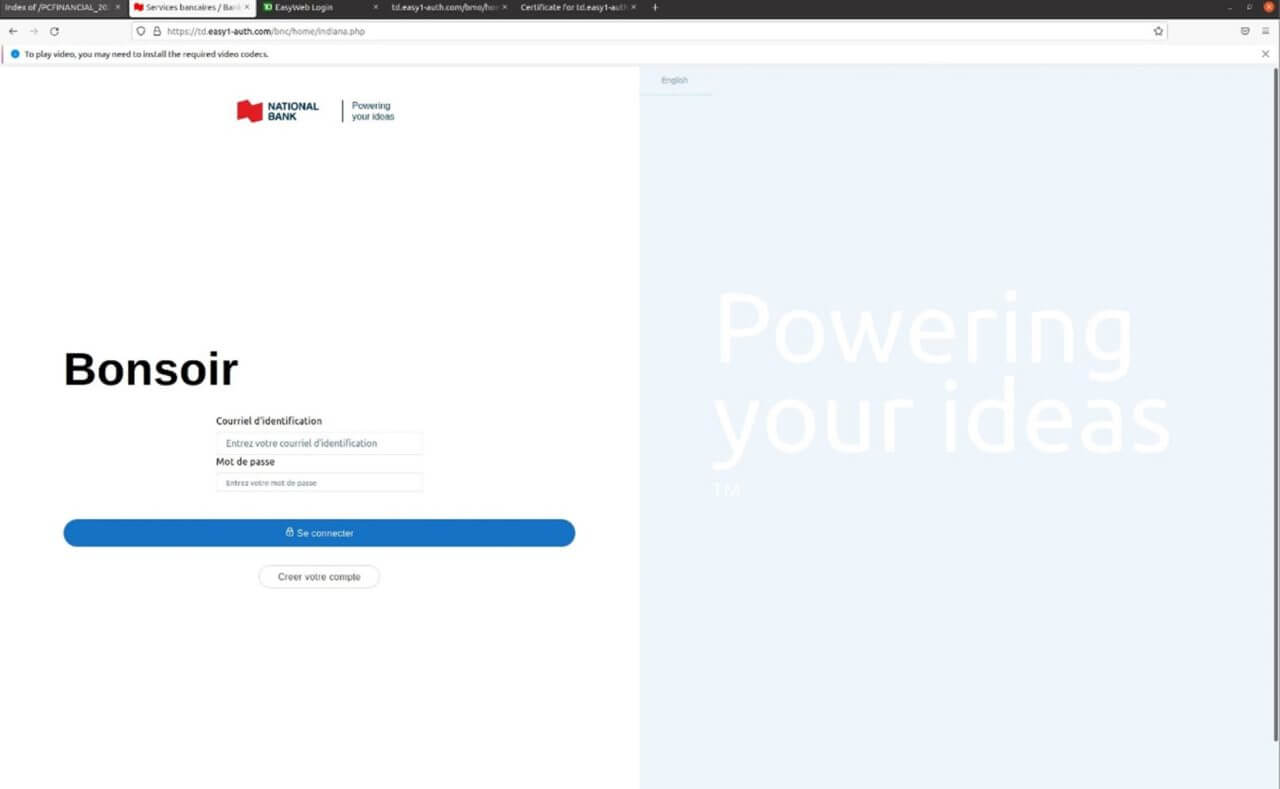
National Bank Scam:

PC Financial Scam:

Reporting the Scam
These fake pages looked like they were going to trick several people into disclosing their private banking information. I decided to report the scam to two of the Canadian Banks. These banks have phishing emails that they use to collect information related to phishing attacks. I reported the phishing text message to [email protected] and [email protected].
This malicious web site is now being reported as being deceptive.


The post ” A Bank SMS Text Phish Attempt” appeared first on TripWire
Source:TripWire – Andrew Swoboda
