99% of Federal Security Pros Feel the U.S. Government Must Do More to Protect Its Data and Systems

As you’ll recall, the White House published an Executive Order (EO) on Improving the Nation’s Cybersecurity back in May 2021. The EO issued several commands such as creating a Cyber Safety Review Board to lead post-incident analysis of significant security events and requiring software developers to make data about their solutions publicly known. The directive also emphasized the importance of moving the federal government to secure cloud services and zero-trust architecture as well as protecting federal systems with encryption, multi-factor authentication (MFA), and other foundational security controls.
It’s been several months since the EO came out. Considering that span of time, many of us at Tripwire found ourselves wondering the following question: How is the federal government doing with the security of its systems and data?
To find out, Tripwire commissioned Dimensional Research to survey 306 security professionals including 103 individuals working for a United States federal government agency with direct responsibility for the security of their employer. Their responses help to provide insight into the current state of federal security and where there’s room for improvement.
A Curious Dichotomy
In its survey, Tripwire found that more than half (56%) of federal security professionals believed federal agencies were doing a better job securing their systems than personnel at non-governmental organizations. A third of security professionals working at critical infrastructure organizations said they felt the same.
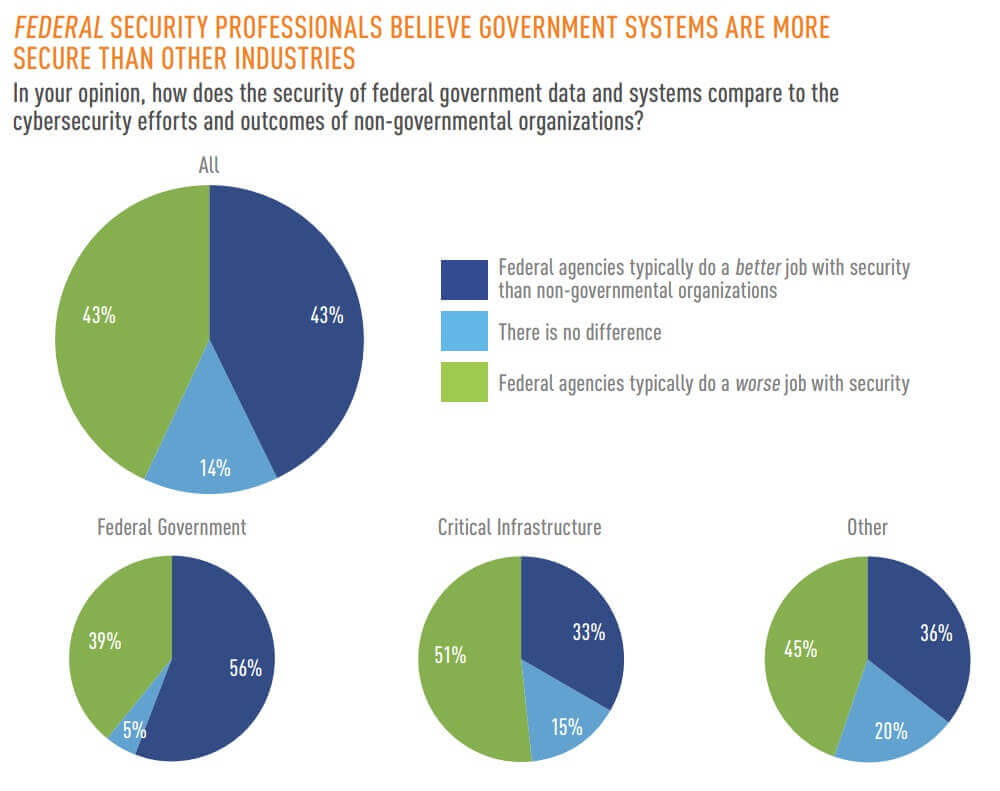
Not everyone agreed on this point. Indeed, nearly half (46%) of survey participants working at non-federal organizations felt that federal agencies did a worse job with securing their systems than their employers. It was even higher among critical infrastructure respondents at 50%.
Struggling to Keep Up
Federal respondents aren’t pretending that their organizations security is perfect, however. On the contrary, 24% said that they’re falling behind. When asked why they thought this was the case, 42% of federal survey participants cited a lack of prioritization among leadership of cybersecurity. This was followed by a lack of internal expertise and resources as well as an inability to keep up with new threats at 50% and 45%, respectively.
These issues are all interconnected. If leadership doesn’t prioritize cybersecurity, to what extent can they make sure that security teams have the necessary resources and personnel to do their jobs? Some might say the cybersecurity skills gap is a contributing factor here, but internal training and certifications can help to level the playing field—if leadership is willing to take cybersecurity seriously, that is. This executive buy-in is crucial if organizations hope to protect themselves against emerging threats.


It’s therefore no wonder that 67% of professionals who felt their employers were staying ahead of cyber threats attributed this posture to leadership prioritizing cyber security efforts. Investing heavily in people and tools was the second most-cited factor at 62%, which was followed by doing the basics at 45%.
A Call for More Action in the Federal Government
In total, 99% of federal security professionals said that the government should do more to protect their own data and systems. Nearly two-fifths (38%) of respondents specified that the government should introduce new legislation with enforcement and oversight of security standards. Slightly fewer (36%) voiced their desire for better enforcement of NIST standards, followed by regulating cryptocurrencies to create barriers to ransomware at 28%.

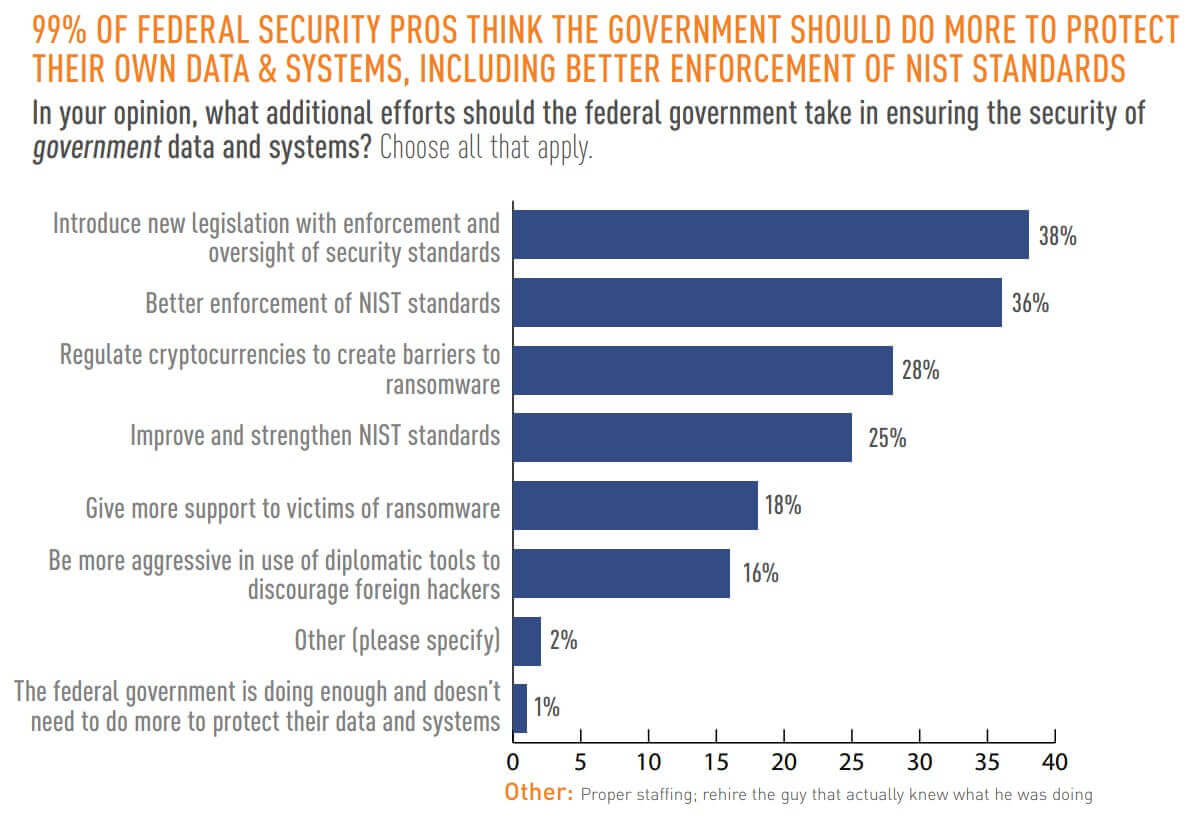
Survey participants didn’t feel that the government’s security duties ended there, however. The majority (95%) of respondents regardless of sector said that the government should play a bigger role in securing non-governmental organizations. Many of these individuals also highlighted a focus on NIST standards and legislation as the way forward.
“It’s clear that organizations—both public and private sector—are seeking further guidance from the federal government,” explained Tim Erlin, vice president of strategy at Tripwire. “Generally, long term enforcement and implementation of cybersecurity policy will take time, but it’s important that agencies lay out a plan and measure execution against that plan to protect our critical infrastructure and beyond.”
Their plan should include working to implement some of the security controls outlined in the May 2021 EO. Some organizations are taking this advice to heart when it comes to zero trust architecture. Indeed, a quarter of security professionals working at a federal agency said that their organization had fully implemented zero trust architecture. About a third (31%) of those respondents said that their organization’s implementation was well developed but still required some work, while 26% wrote that their deployment plan was in progress.
This plan should also include working with a trusted provider of security and compliance solutions for enterprises and industrial organizations. Such a provider should bring years of experience working as a strategic partner with the U.S. federal government to help federal agencies not only advance their security journeys but also to meet regulatory standards such as FISMA, NIST, DISA and CIS.
Learn how Tripwire can augment the security posture of your federal agency.
The post ” 99% of Federal Security Pros Feel the U.S. Government Must Do More to Protect Its Data and Systems” appeared first on TripWire
Source:TripWire – Maurice Uenuma
