FBI warns of Ranzy Locker ransomware threat, as over 30 companies hit

The FBI has warned that over 30 US-based companies had been hit by the Ranzy Locker ransomware by July this year, in a flash alert to other organisations who may be at risk.
According to the alert, issued with the Cybersecurity and Infrastructure Security Agency (CISA), most of the victims were compromised after brute force credential attacks targeting Remote Desktop Protocol (RDP) to gain access to targets’ networks.
Recent victims, according to the FBI, have reported that the malicious hackers exploited known vulnerabilities in Microsoft Exchange Server and phishing attacks as a way of compromising systems.
Once in place, those using the Ranzy Locker ransomware would exfiltrate files from the compromised network, often stealing personal information, customer details, and financial records, before deploying the ransomware to encrypt files across the system.
Victims would find a ransom note in affected folders, demanding a cryptocurrency payment be made for the key to unlock the encrypted files, and to prevent the exfiltrated files being leaked online via the computer underground.
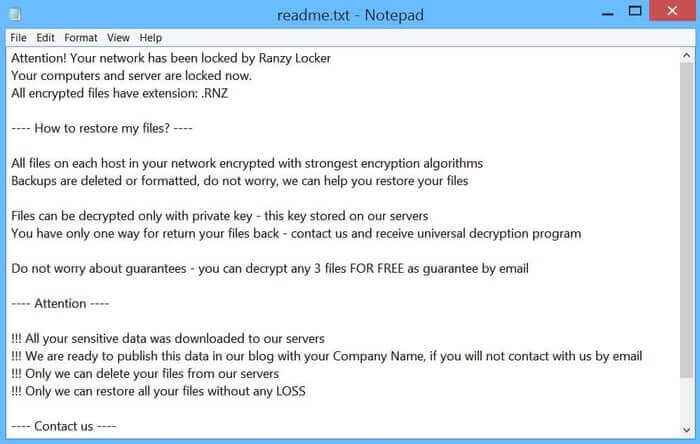
Ranzy Locker follows the popular business model of ransomware-as-a-service (RaaS), that has put more sophisticated attack infrastructure into the hands of anyone who is prepared to sign-up as an affiliate.
The fact that anyone can, essentially, “rent” ransomware like Ranzy Locker to conduct their own attacks makes it all the more dangerous.
If only one group were using Ranzy Locker to attack corporations, they would be limited in their number of victims by their limited resources. But when ransomware is available to all, there’s nothing stopping any Tom, Dick or Harry from trying their luck and launching an attack.
So, it’s clearly important that organisations know what to look out for, and for that reason the FBI flash alert includes indicators of compromise (IOCs) associated with Ranzy Locker, as well as Yara rules to detect the threat.
In addition, the FBI makes some suggestions regarding how the ransomware threat can be mitigated:
- Implement regular backups of all data to be stored as air gapped, password protected copies offline. Ensure these copies are not accessible for modification or deletion from any system where the original data resides.
- Implement network segmentation, such that all machines on your network are not accessible from every other machine.
- Install and regularly update antivirus software on all hosts, and enable real time detection.
- Install updates/patch operating systems, software, and firmware as soon as updates/patches are released.
- Review domain controllers, servers, workstations, and active directories for new or unrecognized user accounts.
- Audit user accounts with administrative privileges and configure access controls with least privilege in mind. Do not give all users administrative privileges.
- Disable unused remote access/Remote Desktop Protocol (RDP) ports and monitor remote access/RDP logs for any unusual activity.
- Consider adding an email banner to emails received from outside your organization.
- Disable hyperlinks in received emails.
- Use double authentication when logging into accounts or services.
Don’t assume that your organisation won’t be the next victim of ransomware, whether it be Ranzy Locker or one of the many other families of ransomware out there. Keep your IT systems patched against the latest vulnerabilities, follow best practices to harden your defences, and check out Tripwire’s tips on how you can harden the security of your business against ransomware attacks.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” FBI warns of Ranzy Locker ransomware threat, as over 30 companies hit” appeared first on TripWire
Source:TripWire – Graham Cluley
