Cybersecurity Maturity Model Certification (CMMC) – A Model for Everyone

Data breaches have reached a fever pitch over the last few years. The rapid frequency of successful attacks coupled with the rising costs to businesses has raised attention at the highest levels of global governments. In the past, breaches were relatively “localized,” that is, they affected the targeted company only. However, the newer attacks have disrupted entire supply chains. While many companies have invested large sums to protect against such attacks, part of a fulsome security program requires the ability to demonstrably validate this security readiness.
What is CMMC?
Government agencies are an attractive target for attackers. The Defense Industrial Base (DIB) as well as the Department of Defense (DoD) supply chains are tempting goals. The DIB sector contains more than 300,000 companies that contribute to all aspects of the Defense Department. Multiple groups within the DoD have created a uniform system for all of these companies to demonstrate compliance. It is known as the Cybersecurity Maturity Model Certification (CMMC).
Many security professionals are familiar with the Cybersecurity Framework. Developed by the National Institute for Standards and Technology (NIST), it has been a recognized standard for many organizations that aim to show security readiness with a formalized security program. The CMMC gives a company the ability to prove readiness through a variety of tiers that can be objectively assessed.
The CMMC offers five tiers of conformity against two separate columns of achievements. To clarify, processes and practices are matched to higher compliance levels.
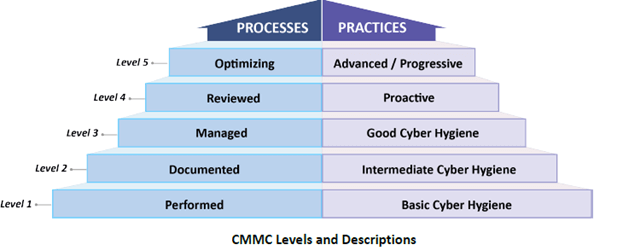
The arrangement of processes and practices is a welcome addition to the canon of cybersecurity guidance. It gives a clear understanding of what processes are expected against their respective practices. This removes a lot of the seemingly discretionary judgement that exists in many other evaluation criteria.
Against that background, the CMMC goes further than just the levels. Quoting from the document:
“In addition to the CMMC level descriptions, the specification and mapping of processes and practices to a particular level take into account multiple considerations . . .”
It also states that,
“The CMMC model, in effect, provides a means of improving the alignment of maturity processes and cybersecurity practices with the type and sensitivity of information to be protected and the range of threats.”
It would seem that these statements are provided to show an understanding that not all data are the same. More specifically, particular types of information are aligned at each level. For example, the protection of Federal Contract Information is classified at a lower level than protecting Controlled Unclassified Information.
Getting into the details
The level of granularity of the CMMC is reminiscent of auditing tools of the private sectors such as the Control Objectives for Information Technology (COBIT) and other assessment standards. The CMMC criteria are spread over 17 “domains.” These domains cover all aspects of a thorough cybersecurity practice. As one examines the separate requirements to fulfill each domain, it becomes evident that there are a total of 171 “best practices” that comprise the CMMC. (This is also stated in the summary of the document.)

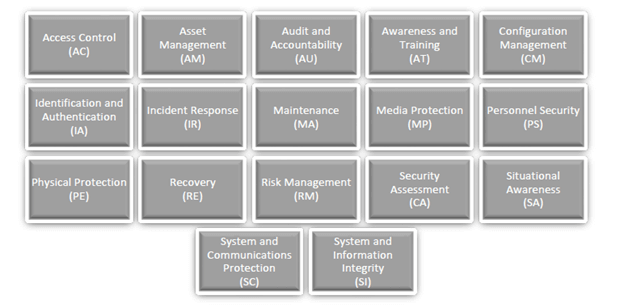
As one progresses along the path of the CMMC, it would appear that the processes of CMMC are arguably more easily attained than the practices. This is because the processes can be approached as a practical set of behaviors, whereas the practices are based upon a “cultural” adherence to those behaviors. “The term institutionalization characterizes the extent to which an activity is embedded or ingrained in the operations of an organization.” That sounds a lot like what we security professionals have been trying to articulate within our organizations for a very long time! Hence the reason why it seems like a more challenging undertaking.
If an organization has a mixture of any of these levels across the organization, then the certification prescribes that the company will be classified under the lowest two designations: Performed, or Documented process; and Basic, or Intermediate Cyber Hygiene practices.
It should be noted that the CMMC is an organizational certification much in the same way that a System and Organization Control (SOC) audit is an avowal of an organization’s effectiveness of controls that are in place. The CMMC is not a personal certification in the security industry, although an individual can become certified as a CMMC or as a higher designation across a set of CMMC “Assessor” levels. As one of the newer DoD requirements, these will prove to be a valuable credential to possess in the cybersecurity community.
The CMMC is in full effect for all organizations that are part of the supply chain for the U.S. Department of Defense. The certification is well developed, and cybersecurity professionals in any organization should become acquainted with it. Like many of the NIST guidance documents, adoption of the CMMC can elevate every organization’s cybersecurity profile. This is a model for everyone.
If you are starting on your path to achieving a CMMC designation for your organization, see how Tripwire can help.
You can also learn more about achieving the DoD’s top three compliance requirements here.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” Cybersecurity Maturity Model Certification (CMMC) – A Model for Everyone” appeared first on TripWire
Source:TripWire – Bob Covello
