Disconnect your WD My Book Live from the web to avoid data deletion, says Western Digital

Storage drive maker Western Digital is telling owners of its WD My Book Live device to disconnect it from the internet after reports that some have had their data erased by malicious software.
According to an advisory issued by the firm, malicious attackers are compromising the devices – commonly used to back up data such as home movies, photographs, and important documents – resulting in their entire contents being wiped in some cases.
Western Digital has determined that some My Book Live devices are being compromised by malicious software. In some cases, this compromise has led to a factory reset that appears to erase all data on the device.
The first indication that most victims will see is an “invalid password” message when they attempt to log into their device.
In a thread on Western Digital’s support forum, many My Book Live owners have described how all of their data has disappeared.
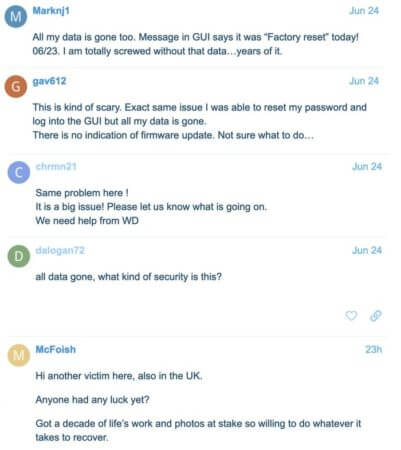
One user who fell victim to the attack said:
“Got a decade of life’s work and photos at stake so willing to do whatever it takes to recover.”
The attackers are thought to be exploiting a remote code execution vulnerability (CVE-2018-18472) that reportedly can be triggered by anyone who knows the IP address of the affected device.
Attacks seen in the wild this week have exploited the vulnerability to force devices into initiating a factory reset, which wipes all data.
All versions of the WD My Book Live and WD My Book Live Duo – which Western Digital stopped supporting and providing firmware updates for in 2015 – are said to be vulnerable.
But pay attention to product names. If you own a WD MyBook or WD My Book Duo (note without the “Live” part of the name), then your data shouldn’t be at risk from this attack.
Western Digital used the word “Live” in the storage devices’ names as a way of describing those backup devices that were connected to the internet and thus accessible remotely.
It remains to be seen whether it is possible for affected WD device owners to recover their lost information. As ever, individuals and organisations are advised to think carefully about their backup regime for valuable data and ensure that they are not just relying upon one technology.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” Disconnect your WD My Book Live from the web to avoid data deletion, says Western Digital” appeared first on TripWire
Source:TripWire – Graham Cluley
