Achieving CIP Compliance, NERC-Style
It’s often said that cybersecurity is hard. Anyone who has ever worked their way through the SANS Critical Controls, PCI-DSS or even something deceptively minimalist as the OWASP Top 10 knows that success in achieving these security initiatives requires time-consuming, diligent and often a multi-team effort.
Now imagine amplifying that responsibility over a power plant that extends over a broad geographic region, and you start to get an idea of the challenge that awaits you. In recent years, plenty of power plants have struggled to strengthen their digital security and suffered digital attacks in the process. Back in 2016, for instance, Reuters reported that investigators had found the W32.Ramnit and Conficker computer viruses hiding in a computer system at the B unit of the Gundremmingen nuclear power plant. It was a year later when BBC News reported that the nuclear power plant in Chernobyl resorted to manually monitoring radiation levels after suffering a NotPetya attack. A couple of years after that, the Nuclear Power Corporation of India Limited confirmed the breach of the administrative network at the Kudankulam Nuclear Power Plant (KKNPP) in Tamil Nadu, India, as reported by The Washington Post.
Cybersecurity and the NERC CIP Reliability Standards
If you work in cybersecurity for a power company, you are most likely familiar with the North American Electric Reliability Corporation (NERC) and its Critical Infrastructure Protection (CIP) Reliability Standards. If you do not work in the power industry, there are many lessons to be learned from this sector that are applicable to all cybersecurity practices.
That being said, there are two striking differences between power companies and other industries. The first is that the power sector is one of the few industries that relies on collaboration between different companies on a regular basis. Rarely do we find two companies based in other sectors working in cooperation to achieve a goal to serve a population. As an example of this point, when two rival pharmaceutical companies announced that they would begin working together during the global pandemic crisis, it made major news. That’s a far cry from energy companies, which have been working together cooperatively for years.
The second striking difference between power companies and other industries is the vastness of a power company’s campus. While one could compare it to the sprawling landscape of a university or a large corporate headquarters, a power company differs in that any breach of security by even a casual trespasser could have grave consequences. For example, one could remove a Wi-Fi hotspot from the grounds of Harvard University, which would create a minor disruption, but the same is not true for the grounds of a power company. Unlike corporate organizations or universities that have centralized data centers, nearly every inch of a power plant, if tampered with, has the potential for a serious disruptive event. Something as seemingly harmless as disabling a monitoring system in one area of a power plant could result in unacceptable “instability, uncontrolled use or cascading within an interconnection.”
It is for those reasons that achieving the Reliability Standards can be such a challenge. The Reliability Standards take a broad approach to cybersecurity, covering everything from risk planning and physical security to personnel training. When visualized in a chart, the requirements become clear. (The orange highlighted boxes show the areas where the Tripwire NERC Solution Suite can help you to achieve compliance.)
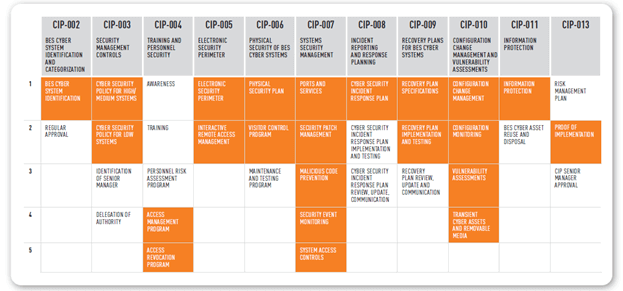
When viewed this way, it is easy to see how intricate the NERC CIP Reliability Standards can be. Organizations strive to meet these controls because they build public trust and confidence. When approached with the idea of achieving a greater vision, the audit process is also easily satisfied. However, even with the greatest intent of integrity and service, some of the concerns surrounding these controls include:
- The inability to stay current with changing security requirements
- Difficulty to fully understand the specifics of some of the expectations
- The inability to update documentation to reflect the changing environments
- The struggle to manually monitor an increasingly vast environment
In many ways, these concerns are no different than any entity that must adhere to one or many regulatory requirements. Yet as was recently experienced when an independent energy company was damaged by a natural event, the need to protect critical infrastructure carries greater responsibility. People depend on this critical infrastructure in order to lead their daily lives. If security professionals don’t take the security of this critical infrastructure seriously, they could threaten the public safety and/or security of countless individuals.
Acknowledging these potential threats, Tripwire’s NERC Solution Suite can help your organization to achieve NERC CIP compliance. We recently released a white paper that discusses the challenges faced by organizations along with the many services that are available to ease the burden and that can allow your staff to focus on their core job functions. Read the full white paper here to learn how Tripwire can help you succeed.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” Achieving CIP Compliance, NERC-Style” appeared first on TripWire
Source:TripWire – Bob Covello
