8 Key Insights from the 2020 (ISC)2 Cybersecurity Workforce Study

2020 has been a very interesting year for the global workforce, with the vast majority of organizations having to rapidly transition to a remote workforce with little to no prior notice thanks to the COVID-19 pandemic.
The 2020 (ISC)2 Cybersecurity Workforce Study looks at the effect of this transition to remote work and how organizations have fared. It also analyzes the impact of the pandemic and the resultant transition to remote work on cybersecurity professionals.
Here are eight key insights from the study:
1. The transition to a remote workforce (and securing this workforce) for most organizations was sudden but well managed
One of the key highlights from the 2020 (ISC)2 Cybersecurity Workforce Study is the sudden shift through which most organizations transitioned to a remote workforce as a result of the COVID-19 pandemic. The majority of organizations managed this transition successfully.
Thanks to the coronavirus pandemic, many organizations were forced to operate fully remotely (or mostly remotely) within days — with a considerable number of organizations forced to work remotely within a day.
Three in 10 organizations had to move to a remote workforce in a day or less, while nearly half (47%) had to move to this model within a week.

Things weren’t much different for the cybersecurity professionals tasked with securing the IT infrastructure of these organizations:

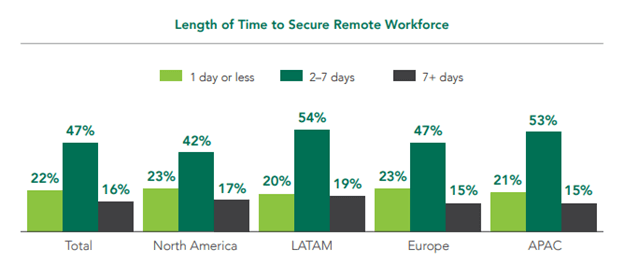
Close to a quarter (22%) of cybersecurity professionals were given a day or less to secure the remote workforce of the organization they work with, while 47 percent were given less than a week.
2. Most organizations were already well prepared to transition to remote work
While the COVID-19 pandemic was unprecedented and tested the wills of organizations to adapt their workforce to the new reality, the majority of organizations were not caught unprepared.
Quite surprisingly, 92% of organizations were at least somewhat prepared to transition to a remote workforce pre-pandemic, with the majority being very prepared.


More than half (53%) of cybersecurity professionals believed that their organizations were very prepared to transition to remote work, while 39 percent felt their organizations were at least somewhat prepared.
3. The shift to remote work positively impacted workplace communication
One of the main fears many had when the sudden need for remote work became clear was that workplace communication would suffer without a lot of face-to-face interactions.
One of the key findings of the (ISC)2 Cybersecurity Workforce Study was that the transition to remote work mostly helped workplace communication:


In particular, 60% of organizations reported that team communication was unaffected by the move to remote work. A quarter of organizations, on the other hand, reported improved communication. Just 12 percent of organizations reported worsened communication.
4. The percentage of organizations whose security have been compromised has only gone up slightly
Transitioning to a remote workforce isn’t the main challenge — securing a remote workforce is.
One of the expectations about the coronavirus pandemic-induced rapid shift to a remote workforce is a rise in the percentage of organizations that will be victims of cybersecurity incidents.
Quite surprisingly, there hasn’t been much change in terms of the number of organizations that have been compromised. If at all, only a few organizations witnessed security incidents after the transition to remote work.

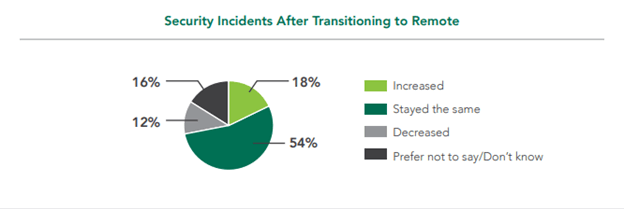
Just 18 percent of organizations reported an increase in security incidents after the transition to a remote workforce. Even fewer (12%) saw incidents decrease. For the vast majority of organizations (54%), things stayed the same.
5. Majority of cybersecurity professionals were unaffected by COVID-19
Despite massive job cuts across industries in response to the pandemic, for the vast majority of cybersecurity professionals, COVID-19 did not affect their jobs.

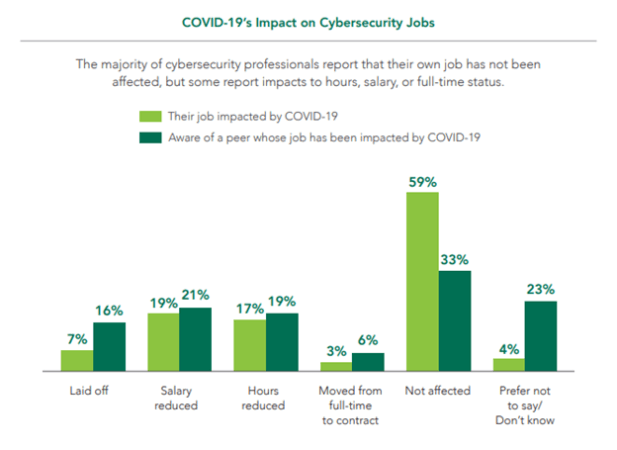
A whopping 59% of cybersecurity professionals reported that their jobs were not been affected by the COVID-19 pandemic. By contrast, just seven percent said they had been laid off as a result of the pandemic.
6. Being fully remote is not yet possible for a considerable percentage of cybersecurity professionals
Unsurprisingly, a significant percentage of cybersecurity professionals reported that working fully remotely is impossible for a number of reasons:
- 42 percent of cybersecurity professionals have to go to the office because it is impossible to fully do their job remotely.
- 36 percent have to go to the office because working to secure their organization requires them to be on-site.
- 24 percent work in a facility that does not allow remote work due to the classified nature of work involved.

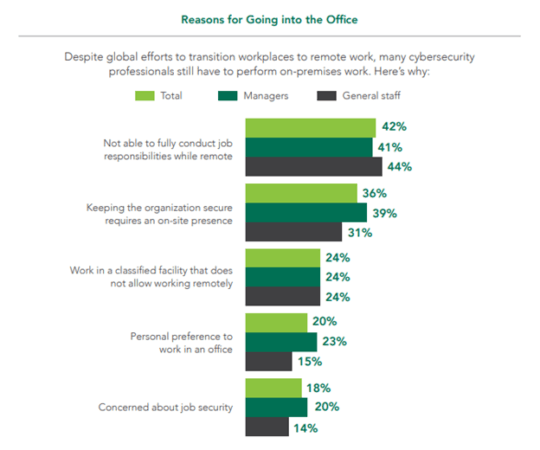
Not all cybersecurity professionals have to go to the office due to work requirements, however. Indeed, 20% said that they simply prefer to work in an office environment instead of remotely, while 18% were concerned about job security if they didn’t show up at the office.
7. Organizations plan to hire more cybersecurity professionals despite the COVID-19 pandemic
The COVID-19 pandemic did not affect the plans of the majority of organizations to expand their cybersecurity workforce – which makes sense considering that the pandemic has only further shown that the future will have more of a focus on remote work.

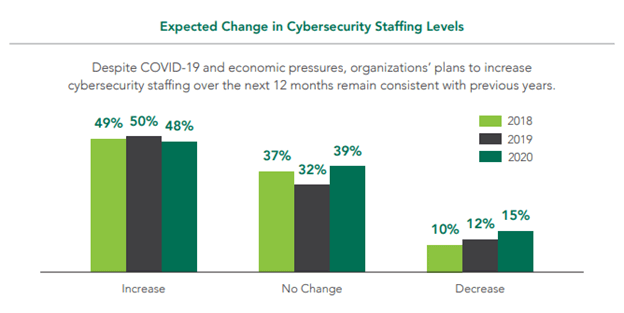
Nearly half (48%) of organizations said they were planning to increase the number of cybersecurity professionals they employ over the next 12 months, a number that is consistent with previous years. Meanwhile, only 15% of organizations noted they planned to decrease cybersecurity staff.
8. Most cybersecurity professionals are millennial males
The vast majority of cybersecurity professionals are millennials and male.

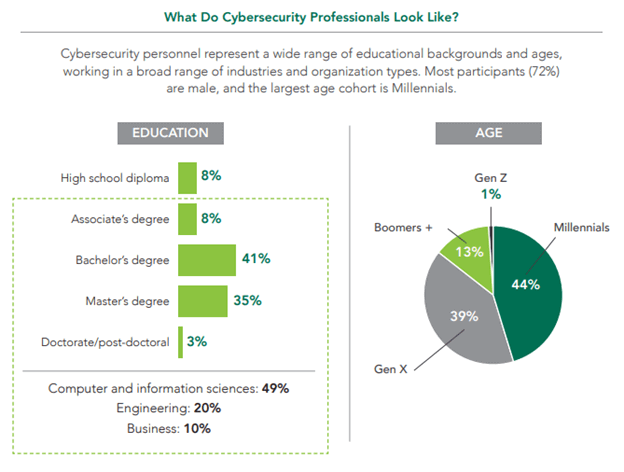
The 2020 (ISC)2 Cybersecurity Workforce Study found that 72% of cybersecurity professionals were male and 44% were millennials.
The lack of diversity in the cybersecurity space
The findings of (ISC)2 Cybersecurity Workforce Study were generally impressive, defying expectations in some ways, particularly with only 18% reporting an increase of security incidents following the transition to remote work. But perhaps the most salient and long-term issue is the continuing the lack of diversity in the cybersecurity space; the majority of cybersecurity professionals are male.
The fact that just a little over a quarter of cybersecurity professionals are female is not demographically reflective of the wider community of users and is something organizations should consciously address by actively seeking and incentivizing female cybersecurity professionals.
This coincides with the need to address the persistent skills-gap issue in the industry. Tripwire’s study published earlier in the year shows that the majority of cybersecurity professionals (83%) felt pressured and overworked going into 2020. (This was before the pandemic.) The massive shift to a remote workforce certainly hasn’t helped.
The industry still has work to do. A more diverse workforce is certainly something that should be a high priority for most organizations. To bridge the skills gap, don’t just focus on hiring those with computer science backgrounds or years of experience, either. Look to those with different backgrounds and different skills but who all have one thing in common: they want to help make the internet a safer place.
About the Author: Kristina Tuvikene is an editor at ONLINE ONLY, an agency that works with cloud services brands among others. You can find her on LinkedIn.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” 8 Key Insights from the 2020 (ISC)2 Cybersecurity Workforce Study” appeared first on TripWire
