FERC Releases Staff Report on Lessons Learned from CIP Audits

In October, the Federal Energy Regulatory Commission (FERC) released its “2020 Staff Report Lessons Learned from Commission-Led CIP Reliability Audits.” The report summarizes the Commission’s observations from Critical Infrastructure Protection (CIP) audits performed in conjunction with staff from Regional Entities and the North American Electric Reliability Corporation (NERC). It is intended to inform both the community that’s subject to the CIP reliability standards and the public of lessons learned from audits performed in 2020. In doing so, the report is careful to point out that while a majority of the cyber security elements adopted by the audited utilities met the minimum requirements of the standards, potential compliance infractions still came to the surface. Additionally, the report includes recommendations that are outside the guise of the CIP requirements.
Lessons Learned
The report cites twelve lessons learned from the audits. They are transcribed here:
- Ensure that all BES Cyber Assets are properly identified.
- Ensure that all substation BES Cyber Systems are properly categorized as high, medium, or low impact.
- Ensure that electronic access to BES Cyber System Information (BCSI) is properly authorized and revoked.
- Consider having a dedicated visitor log at each Physical Security Perimeter (PSP) access point.
- Consider locking BES Cyber Systems’ server racks where possible.
- Inspect all Physical Security Perimeters (PSPs) periodically to ensure that no unidentified physical access points exist.
- Review security patch management processes periodically and ensure that they are implemented properly.
- Consider consolidating and centralizing password change procedures and documentation.
- Ensure that backup and recovery procedures are updated in a timely manner.
- Ensure that all remediation plans and steps taken to mitigate vulnerabilities are documented.
- Ensure that all procedures for tracking the reuse and disposal of substation assets are reviewed and updated regularly.
- Consider evaluating the security controls implemented by third parties regularly and implement additional controls where needed when using a third party to manage BES Cyber System Information (BCSI).
My Observations
Trending Toward Procedural Controls
I found it especially interesting that none of the lessons learned included in this year’s report overlap with those cited in the 2019 report. Even so, there are some similarities. I don’t think that the intent here is to say that all the previous lessons learned still aren’t a problem or that they shouldn’t be a focus area for asset owners. Rather, I think it’s saying that the problem areas continue to multiply.
That being said, the Commission lessons appear to be trending toward procedural driven rather than remediable by a technical control. Being a personal fan of technical controls, this saddens me.
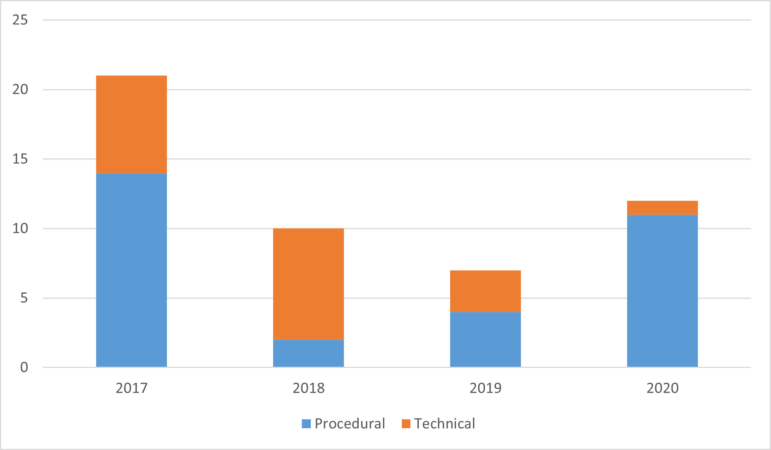
| 2017 | 2018 | 2019 | 2020 | |
|---|---|---|---|---|
| Procedural | 14 | 2 | 4 | 11 |
| Technical | 7 | 8 | 3 | 1 |
| Total | 21 | 10 | 7 | 12 |
This year, the procedural controls lessons cover much more than just asset identification and categorization. I’ll reorder with security over compliance in mind based on what I think should have been their priority:
- Backup and Recovery – Who hasn’t had a sleepness night worried about their backups? And with soaring ransomware cases, this is more important than ever.
- Security Patch Management
- Vulnerability Management – I’ll just leave this here.
- BCSI – Examples of misconfigured AWS S3 buckets are becoming even more prevalent. And I know I said I wouldn’t say anything about compliance, but we can’t forget this.
Asset and Facility Categorization Remains Focus
In the 2019 report, the first lesson states, “Consider all generation assets, regardless of ownership, when categorizing BES Cyber Systems associated with transmission facilities.” This year’s first and second lessons are closely related, leading me to believe that asset categorization remains a problematic oversight. Last year, staff homed in on generation assets associated with transmission facilities, and this year, they expanded the scope to include all BES Cyber Asset identification and substations.
BCSI
Last year, identification of BCSI made the list. This year, its revocation and authorization. Arguably more interesting is the inclusion of BCSI when managed by a 3rd party. Could the Commission be alluding to that 3rd party being your favorite SaaS or cloud provider? More than ever, BCSI “in the cloud” appears to be an industry hot topic. Coincidence? I think not.
Physical Security Easy Wins
A recurring theme continues to surface, which I would consider to be “easy wins” with regard to physical security. Visitor logs and key management are prime for implementing technological solutions to alleviate the manual efforts that cause these habitual problems.
Although I found a lot that I did not particular enjoy, I am still glad that the Commission takes the time and effort to put these reports together and I will continue to track my perceptions year to year, while hoping for a trend toward more technical control recommendations.
The post ” FERC Releases Staff Report on Lessons Learned from CIP Audits” appeared first on TripWire
Source:TripWire – Robert Landavazo
