Zoom Releases New Security Features to Counter Zoombombing

Zoom released new security features to help its users counter disruptive meeting intrusions, otherwise known as “Zoombombing.”
Matt Nagel, security & privacy PR lead at the American communications technology company, announced in a blog post on November 16 that Zoom had released two new anti-Zoombombing features over the previous weekend.
The first new feature enables hosts and co-hosts to temporarily pause all meeting activity including recording, chat, screen sharing and breakout rooms.
Nagel explained how hosts and co-hosts can use this feature to eject disruptive participants from their meeting:
The hosts or co-host will be asked if they would like to report a user from their meeting, share any details, and optionally include a screenshot. Once they click “Submit,” the reported user will be removed from their meeting, and Zoom’s Trust & Safety team will be notified. Hosts and co-hosts may resume their meeting by individually re-enabling the features they’d like to use. Zoom will also send them an email after the meeting to gather more information.
This feature is enabled by default for all Zoom users.
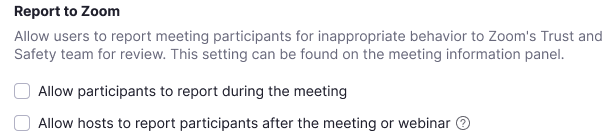
The second new capability announced by Zoom allows meeting participants to report disruptive users directly from the video app client.
All hosts and co-hosts need to do is make sure that this reporting feature is enabled for participants in their web settings.
News of these two new features arrived soon after Zoom announced that it would be deploying an “At-Risk Meeting Notifier” to scan public social media posts and other websites for shared Zoom meeting links, automatically alert account holders if and when it found something as well as help them take action to prevent Zoombombing.
Zoom clarified that one of the best ways for users to protect themselves against Zoombombing is to never share their meeting ID or passcode on a public site.
Users can follow these best practices to strengthen their Zoom security even further.
The post ” Zoom Releases New Security Features to Counter Zoombombing” appeared first on TripWire
Source:TripWire – David Bisson
