Newly-discovered KryptoCibule malware has been stealing and mining cryptocurrency since 2018

Security researchers at Slovak security firm ESET have discovered a new family of malware that they say has been using a variety of techniques to steal cryptocurrency from unsuspecting users since at least December 2018.
The malware, which has been named KryptoCibule, uses a variety of legitimate technology – including Tor and the Transmission torrent client – as part of its scheme to mine cryptocurrency, divert digital currency transactions into its creators’ own accounts, and plant a backdoor for hackers to remotely access infected systems.
KryptoCibule poses a three-pronged threat when it comes to cryptocurrency.
Firstly, it exploits the CPU and GPU of infected computers to mine for Monero and Ethereum. In an attempt to avoid detection by the legitimate user of the computer, KryptoCibule monitors the battery level of infected devices and will not do any mining if the battery is at less than 10% capacity.
If the battery level status is between 10% and 30%, however, Ethereum-mining via the GPU is suspended and only Monero-mining via the CPU takes place, albeit limited to one thread.
However, if the battery level is 30% or more and there has been no user activity for the last three minutes, “both the GPU and CPU miners are run without limits.”
In this way, KryptoCibule attempts to surreptitiously mine cryptocurrency on infected PCs without users detecting anything suspicious.
Secondly, the KryptoCibule malware monitors the user’s clipboard. If it detects that a legitimate cryptocurrency wallet address has been placed in the clipboard it silently replaces it with one of its own – meaning that users might unwittingly be transfer funds directly into the hackers’ own digital pockets.
Thirdly, the malware scouts drives attached to an infected computer, hunting for files which might contain content of interest – such as passwords and private keys.
And if this wasn’t bad enough, KryptoCibule’s RAT (Remote Access Trojan) component allows attackers to run commands on victims’ PCs via a backdoor, and install additional malicious code.
According to ESET’s research, KryptoCibule has been distributed via malicious torrents posing as pirated versions of popular games and other software on uloz.to; a popular file-sharing site in Czechia and Slovakia.
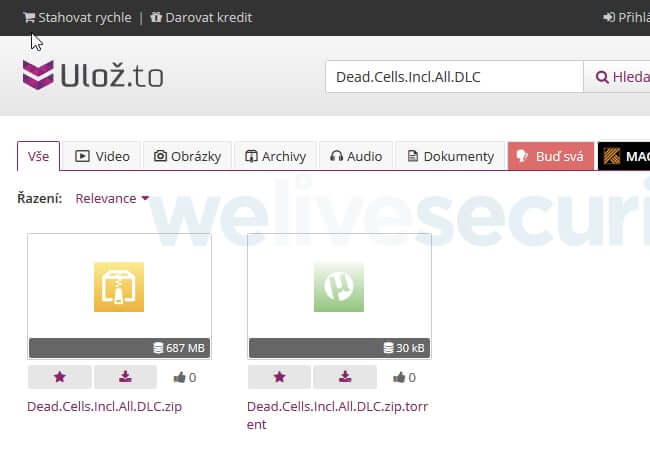
To disguise its behaviour, users who download the torrents and execute the installer do not realise that malicious code is being run in the background.
The link to Czechia and Slovakia is reinforced when it comes to the malware’s methods to avoid detection. If KryptoCibule detects that it is being installed on PCs running Avast, AVG, and ESET (all security products with head offices based in the two countries) it deliberately does not deploy its cryptocurrency-mining code, helping it to avoid attention.
To date, perhaps because of its geographic focus and desire to remain in the shadows, KryptoCibule does not appear to have infected a large number of computers. ESET believes that victims may number in the hundreds rather than thousands. However, it has remained active in the wild since at least late 2018, and has been regularly updated with new capabilities.
While threats like KryptoCibule continue to be actively developed we would be unwise to underestimate them.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” Newly-discovered KryptoCibule malware has been stealing and mining cryptocurrency since 2018″ appeared first on TripWire
Source:TripWire – Graham Cluley
