Convergence and adoption of AI and ML countering the cyber threat

During the last few years, we have witnessed an increase in advanced cyber attacks. Cybercriminals utilize advanced technology to breach the digital boundary and exploit enterprises’ security vulnerabilities. No industry feels secure; security professionals do their utmost to close security gaps and strengthen their cyber defense. As new technologies pop up at an unprecedented rate, cybersecurity professionals are literally “chasing the tail”; they need time to train themselves in new systems and processes understand how they work, and adopt best practices to protect them against cyber threats.
To counter advanced technology a high-tech toolbox is needed. Technologies such as artificial intelligence (AI) and machine learning (ML) have come into play and are used in the cybersecurity industry. Can this inseparable duo play a significant role in the fight against cybercriminals in a way that eliminates inefficient human behavior and perception from the equation? Can security systems “be educated” to discover anomalies of behavioral changes as soon as they happen?
Cyber threats, AI and ML
As more businesses transform digitally, advanced cyber attacks become denser, and more “lethal” for their reputation and revenue. The proliferation of cyber threats during the last years is a fact, whilst the trend for the future is not an optimistic one. In the US the number of data breaches by the end of the third quarter of 2021 exceeded all of 2020 by 17%. Ransomware attacks are happening every 11 seconds resulting in a business downtime of more than 20 days and a massive amount of ransoms paid.
Although humans still play a significant role in cybersecurity today, technology is gradually catching up to us in several areas. AI gives computers the full responsive ability of the human mind, and ML uses existing behavior patterns to inform decision-making based on past data and conclusions with minimum or no human intervention.
AI and ML detect anomalies and potential threats in real-time. They employ algorithms to analyze massive amounts of data and build behavioral models to make accurate cyber attack predictions as new data emerges. These technologies assist the defenders to increase the accuracy and speed of response to cyber incidents.
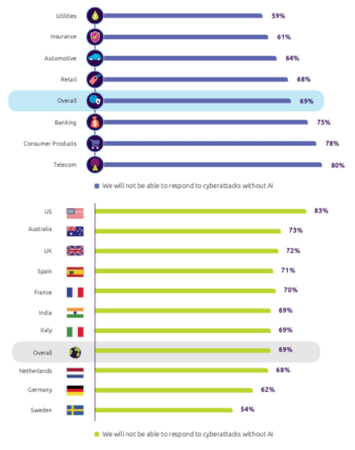
In the battle for cybersecurity AI and ML become significant allies against advanced attacks. According to the Capgemini Research Institute report, almost 7 out of 10 organizations can’t identify nor respond to cyber threats without AI, whilst the AI cybersecurity market is expected to grow to $46.3 billion by 2027.
How AI and ML can assist in cybersecurity
As we investigate the security implications of AI and ML it is critical to contextualize current cybersecurity, as a lot of processes can now be addressed by AI and ML technologies.
Time and cost savers
One of the most critical metrics for cybersecurity teams’ efficacy is threat response time. Cybercriminals use advanced automation to accelerate attack time significantly. In many cases the security response lags behind the attack; teams are reacting to successful attacks rather than preventing them.
AI and ML can instantly compile attack data for analysis and feed decision-makers with useful reports. Furthermore, these technologies can predict and prevent future attacks, as they can process large amounts of data in real-time. They are able to send alerts and create defensive patches autonomously, as soon as they detect an anomaly.
Additionally, the Capgemini report showed that the use of AI and ML technologies lowers IT costs by more than 10% and saves organizations’ expenditures. They are considered cost-effective technologies, as they reduce the threat detection and response effort.
The human uncertainty
AI and ML can help with the configuration of the systems. As new technologies are stacked on top of older frameworks, humans need to ensure that the new infrastructure is secure. The layered symbiosis and proper configuration of the old and new systems is a hard task for security teams. Support tasks, numerous updates, and manual assessment of the configuration security can drive security teams to omissions and potential mistakes. Adaptive automation can help these processes: advise teams on issues, adjust settings, and apply updates without any human intervention.
Threat alert fatigue is another weakness where AI and ML can assist humans. As the attack surface grows and expands, attacks increase. A lot of security systems are designed to respond to issues by sending quite a lot of proactive alerts to the security teams; then humans must decide and act within a highly condensed alert environment. As teams usually lack personnel, training, and time to staff all information provided, decision fatigue comes. With the assistance of AI and ML technology, this can be eliminated as threats can be labeled, sorted, prioritized, and treated automatically by algorithms.
Last but not least, AI and ML can help with the identification and prediction of new threats. Unknown attack types lead to security teams’ slow reaction, as they may remain well hidden, silent, and undiscovered for a long time. AI and ML can find commonalities between the old and the new threats. From this perspective, machine learning may help security teams forecast new risks and shorten the lag time as a result of greater threat awareness.
Humans may take a break
The benefits of using AI and ML technologies in cybersecurity are considerable, since they reduce the cyberattacks detection and response time; they analyze cyber threats and suspicious behaviors effectively, and improve the cybersecurity posture of any business using them.
In cybersecurity, AI and ML have been hailed as breakthrough technologies that are much closer than we realize. However, this is only a part of the reality; the truth is that in the age of technological advancement, even though technology has become superior to us, the human is still the leader. We cannot eliminate the human factor from cybersecurity. Although human behavior, mistakes, and fatigue impacts cybersecurity extremely, AI, ML and humans can work together and reduce drastically human inefficacy from the cyber security formula.


Christos is intrigued by new challenges, open minded, and excited for exploring the impact of cybersecurity on industrial, critical infrastructure, telecommunications, financial, aviation, and maritime sectors.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” Convergence and adoption of AI and ML countering the cyber threat” appeared first on TripWire
