NHS warns of scam COVID-19 text messages
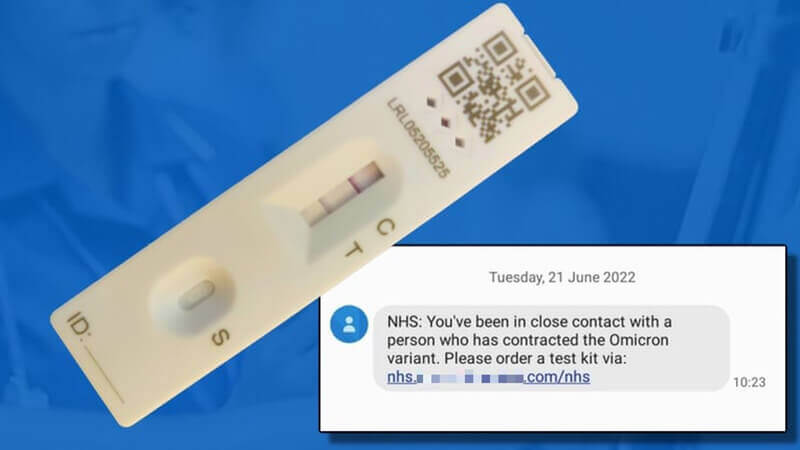
The UK’s National Health Service (NHS) has warned the public about a spate of fake messages, sent out as SMS text messages, fraudulently telling recipients that they have been exposed to the Omicron variant of COVID-19.
In a tweet, the NHS said that it had seen reports of text messages that claimed to come from the NHS, telling recipients that they had been in close contact with someone who had a confirmed COVID-19 infection, and that they should order a testing kit.
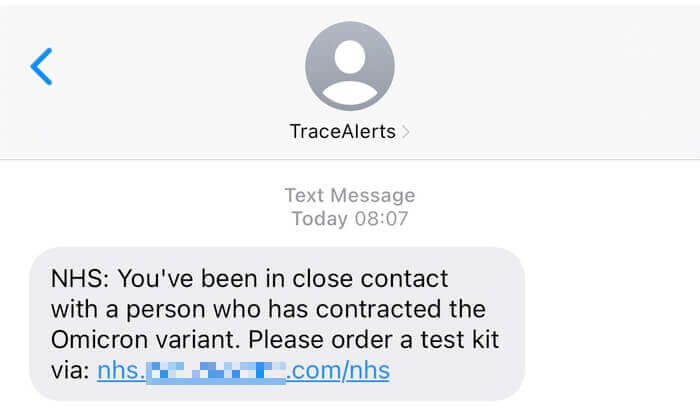
So, what happens if you do make the mistake of clicking on the link in the bogus text message you have received?
The real NHS website is at nhs.uk, but obviously the scammers don’t want you to go there.
Instead, the link sent to you by the scammers takes you to a lookalike website that pretends to belong to the NHS.


To the casual observer it looks very much like the real NHS website. Indeed, on a smartphone you may very well not notice that the domain you have visited is not nhs.uk.
This bogus website wants you to order a test kit, for which you will “only have to pay £0.99 for postage”.


The real NHS does not distribute free COVID-19 test kits anymore, so the notion that all you have to do to receive a free test is pay 99 pence postage should also ring alarm bells in the victim’s minds. However, if you’ve got this far through the scam chances are that you will also have forgotten that fact in your panic to get yourself tested for the Omicron variant.
Of course, the website doesn’t just want your money. It also wants your full name, address, date of birth, and other personal information. If you hand over this information you are unwittingly helping the fraudsters scam you further, by sharing your personal data. At some point in the future, this information could be used against you by a scammer to make them appear even more convincing.
The scammers are using a variety of different domains in their scam messages, many of which have only been created in the last few days.


In its warning the NHS references advice from the NCSC about spotting scams. One would imagine that the NHS is also reporting the scam websites to the NCSC so they can be shut down as quickly as possible, but – of course – opportunistic scammers will continue to create new domains, and send out more scam messages, for as long as they believe it will help them defraud innocent members of the public.
With so many scams reliant on the use of newly-created websites it’s a shame that giants like Apple and Google don’t do more to warn users that they are clicking on a link to a website which you should probably be more skeptical about than one which has existed for years and years.
And no, it should go without saying, you’re not going to receive a free COVID-19 testing kit through the post after handing over your personal information on one of these scam websites.
Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
The post ” NHS warns of scam COVID-19 text messages” appeared first on TripWire
Source:TripWire – Graham Cluley
