98% of Infosec Pros Say Multi-Cloud Environments Create Additional Security Challenges, Reveals Survey

Organizations have multiple reasons for embracing a multi-cloud strategy. First, it enables them to avoid “vendor lock-in” where they need to rely on a single vendor for all their cloud-based needs. Second, it empowers them to take advantage of the perks offered by several cloud service providers at once. Lastly, such a strategy helps to protect them against data loss and/or downtime, as an issue in one environment won’t necessarily spill over into another.
But a multi-cloud strategy isn’t always easy. With multiple cloud environments to manage, some organizations struggle to maintain compliance with regulatory standards. They also might not have the necessary tools to manage vulnerabilities across their entire cloud infrastructure.
This reality raises several questions. How do teams view the security challenges associated with multi-cloud environments? And how are organizations working to address those factors?
More Complexity, More Challenges
To answer those questions, Tripwire commissioned Dimensional Research to survey 314 security professionals who held direct responsibility for securing their respective employer’s public cloud infrastructure. Their responses help to illuminate the state of cloud security for enterprise environments in 2021.
First, 73% of survey participants told Dimensional Research that their employer was using a multi-cloud environment. Those individuals cited all the benefits of using such a strategy that I discussed above. They also mentioned how multi-cloud environments in some cases align with their business requirements. Indeed, 41% pointed out how different teams, departments, and/or lines of business have standardized on different providers, making it essential for organizations to work with more than one cloud deployment. Similarly, approximately the same proportion (40%) indicated how some of their apps require specific providers.
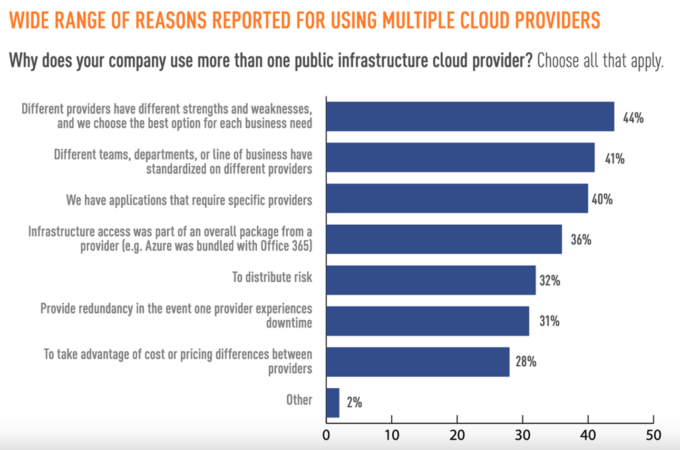
Even so, 98% of infosec professionals with multi-cloud environments agreed that such an approach created additional security challenges for their organization. Two-thirds of respondents specifically pointed out that different environments require different tools for managing security. Just slightly less than that (60%) said that they need to understand multiple sets of protocols because each provider has its own way of securing things.
Tim Erlin, vice president of product management and strategy at Tripwire, explained that he wasn’t surprised by these findings.
We’ve seen a massive shift to cloud in response to the growing business need to manage more data and have greater accessibility. Given the growing complexity of systems and threats that come with moving to a cloud environment as well as the security policies that are unique to each provider, it makes sense that organizations are finding it increasingly difficult to secure the perimeter.
Here’s what this difficulty looks like in practice:
- Just 21% of respondents said that their organizations used a central dashboard that provided them with a view across their multiple cloud accounts’ security posture and policy compliance.
- 59% of survey participants revealed that their organizations had established configuration standards for their public cloud environments. That proportion was even less for organizations with under 1,000 employees at 45%.
- Half of infosec professionals said that they use best practice security frameworks across all frameworks but not all instances. Just 38% said that they do both consistently.
How Organizations Could Address These Security Challenges
When asked about how they manage their multiple cloud environments, many respondents said that their organizations’ security teams took formal training or received certifications online. Others self-taught themselves online. No wonder then that only 9% of security professionals surveyed considered their organizations’ internal teams to be “experts” on public cloud security.


Organizations don’t need to cultivate their own internal expertise when it comes to public cloud security, however. Erlin clarified why:
For most security professionals, managing a multi-cloud cloud environment is a fairly new and somewhat ambiguous part of their day-to-day. Fortunately, there are well-established frameworks and solutions that exist to help fill in the gaps and ensure organizations don’t have to rely solely on their cloud providers to secure their environment.
Take Tripwire’s cloud cybersecurity solutions as an example. These solutions extend across organizations’ physical, virtual, and multi-cloud environments—something which 81% of respondents in the survey said that an ideal tool would do. With this unified approach, Tripwire’s solutions maintain consistent visibility of all network assets including cloud-based resources that are dynamically created and destroyed. Security teams can then leverage that visibility to monitor all their assets’ secure configurations and to manage vulnerabilities that might affect either their physical or cloud environments.
Unify your security approach with Tripwire today.
The post ” 98% of Infosec Pros Say Multi-Cloud Environments Create Additional Security Challenges, Reveals Survey” appeared first on TripWire
Source:TripWire – Jess Glackin
