5 tips for spotting and avoiding Pig butchering scams
A new type of scam, called “pig butchering” is gaining momentum. Pig butchering is a unique scam which uses a romance scam script, but with an investment spin on it, where victims are groomed to invest large sums of money, often on fake crypto apps. Behind the scenes of these scams are scam centers run by cryptocurrency scammers, who coerce human trafficking victims into executing the online scam en masse, sometimes defrauding the unsuspecting victims of their life savings.
How do they work?
Often, these scams start by texting the victim via SMS, or frequently on WhatsApp, either pretending to be a wrong number or an acquaintance from the past, immediately striking up a friendly conversation with a victim. Communication is very frequent (several times a day) and soon turns to investment talk. Most people now know to avoid requests for money, so scammers are getting smarter and using persuasion rather than direct requests. Through discussions about investments and profits, the victim is slowly sucked into what looks like an innocent conversation but is actually in a grooming stage, in which they are prepared to engage in an investment. This stage can last days or even weeks. Scammer also take cues from the victim, assessing what type of relationship are they after; companionship, relationship, or business deal, adjusting and adapting the conversation accordingly. The potential victim is then heavily coached through screenshots about how to download trading apps, transfer funds, and buy or transfer funds into cryptocurrency. They are encouraged to invest more and more as time goes on, even getting loans and taking money out of their retirement plan to continue investing. The losses can be devastating.
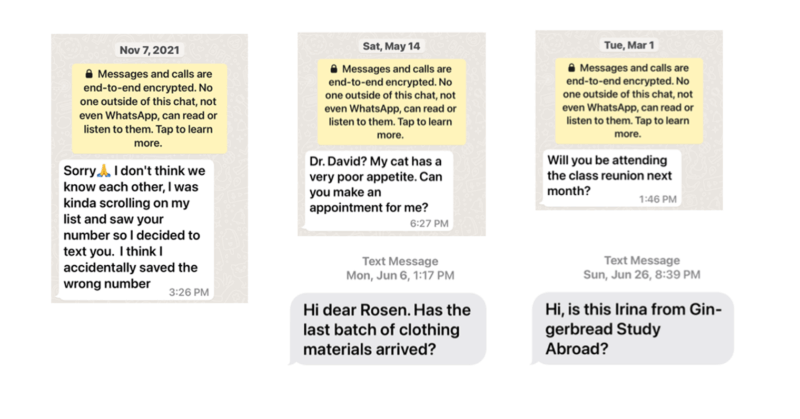
This is how the typical correspondence starts.
Things to watch for
- Random text or email from someone you don’t know, engaging you in frequent conversation. Encouraging engagement in any type of conversation is a small win for scammers. This is a known scam technique. People like to be consistent and once you reply once, it will be harder to stop. Communication will be very frequent and may focus first on mundane things, like what you are doing, eating, or similar innocent activities. Frequent communication has been found to elevate emotional involvement.
- Person you are communicating with refuses to talk on the phone.
Scammers will avoid phone and video conversations. They will say their English is not good enough and may invent stories that give a good reason for not wanting to video call, e.g., their loved one died while driving and video calling someone. Or they may just ignore the request by distracting you and asking about other things.
- Conversation quickly focuses on investment that is earning high returns for the person communicating with you.
While talking about daily routines, the conversation quickly turns to high earnings the person is making by investing. The scammer may also boast about houses in several locations or mention other status symbols like nice cars, expensive holidays, or hired staff, such as a chauffeur, or personal assistant.They may or may not state they have secret inside trading info that assures risk-free wins. They will ask you if you want to try investing too, even offering free simulations so you can see how it works (which can be manipulated to look like big wins, so victims are reassured and persuaded to invest). The scammer may reassure you that you should not invest if you are nervous, or to start small, but after a small amount, which will likely result in a profit, you will be more likely to engage further.
- Conversation is flirtatious and the person is praising you, but mostly when you are talking about investing
The person communicating is flirtatious with you, praising or complimenting you, or they may express the desire for a future with you. But these types of messages are more frequent when you are engaging in conversations about investments or promising to invest. At other times, when you try to talk about other things, conversations are short, and the person will tell you that they are busy. They may also threaten to stop communicating if you ask too many questions, or if you request photos or video calls. You are made to feel like you must talk about the investment, or follow their instructions to continue communicating with them.
- Scammer is focusing your attention on the prize
This is a known scam technique – reminding potential victims what they could do with the winnings, how they can improve their life. Also, if you invest a small amount because you are afraid of the risk, the scammer may focus your attention on how the win could have been more if you initially invested more. This technique works by evoking greed and desensitizing the potential victim to invest amounts they are uncomfortable losing.
Pig butchering scams are very clever and combine several methods found in different types of scams. Rather than follow the exact script, the scammer tailors the scam based on the victim’s response and level of engagement, sometimes developing intense romantic relationships quickly or acting as a friend and confidante. Their focus is to insert themselves in your daily life, keep earning your trust and slowly introducing the idea of investing over time, until the victim is ready to invest. As such, this scam may not raise typical warning signs that come with typical investment scams, like being pressured to invest. Instead, they rely on priming that happens over time (slowly exposing you to an idea of investment to evoke compliance later on), which is often subconscious. The best thing to do, in order to avoid getting involved, is to ignore any unsolicited messages, however innocent they sound.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor and do not necessarily reflect those of Tripwire, Inc.
The post ” 5 tips for spotting and avoiding Pig butchering scams” appeared first on TripWire
Source:TripWire – Martina Dove
